Hwtacacs basic message exchange process – H3C Technologies H3C SecPath F1000-E User Manual
Page 166
156
HWTACACS RADIUS
Supports authorization of configuration commands.
Which commands a user can use depends on both the
user level and the AAA authorization. A user can use
only commands that are at, or lower than, the user
level and authorized by the HWTACACS server.
Does not support authorization of configuration
commands. Which commands a user can use solely
depends on the level of the user. A user can use all the
commands at, or lower than, the user level.
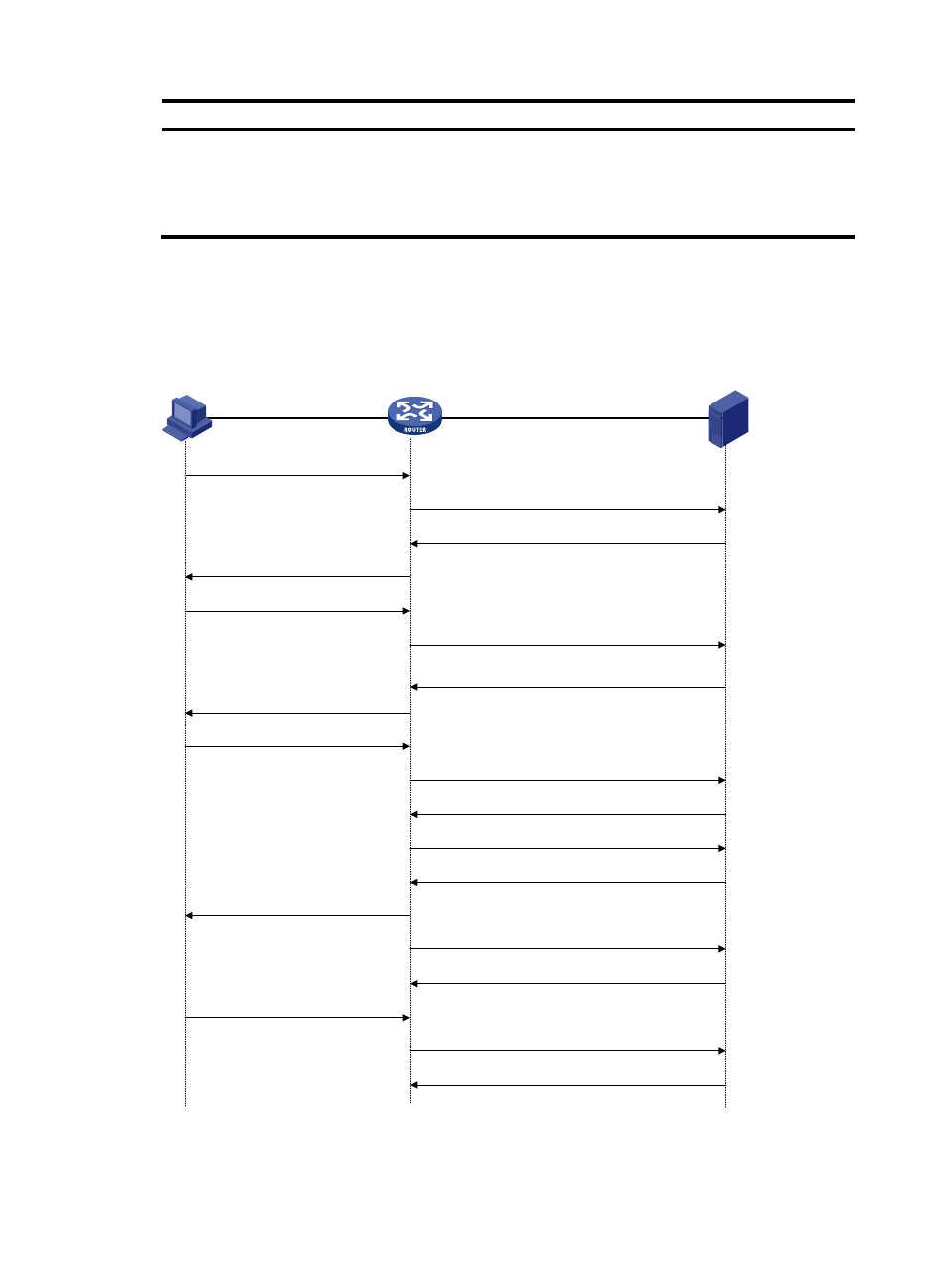
HWTACACS basic message exchange process
The following example describes how HWTACACS performs user authentication, authorization, and
accounting for a Telnet user.
Figure 134 HWTACACS basic message exchange process for a Telnet user
HWTACACS operates in the following manner:
1.
A Telnet user sends an access request to the HWTACACS client.
Host
HWTACACS client
HWTACACS server
1) The user logs in
2) Start-authentication packet
3) Authentication response requesting the username
4) Request for username
5) The user inputs the username
6) Authentication continuance packet with the
username
7) Authentication response requesting the login
password
8) Request for password
9) The user inputs the password
11) Authentication response indicating successful
authentication
12) User authorization request packet
13) Authorization response indicating successful
authorization
14) The user logs in successfully
15) Start-accounting request
16) Accounting response indicating the start of
accounting
17) The user logs off
18) Stop-accounting request
19) Stop-accounting response
10) Authentication continuance packet with the
login password
- H3C SecPath F5000-A5 Firewall H3C SecPath F1000-A-EI H3C SecPath F1000-E-SI H3C SecPath F1000-S-AI H3C SecPath F5000-S Firewall H3C SecPath F5000-C Firewall H3C SecPath F100-C-SI H3C SecPath F1000-C-SI H3C SecPath F100-A-SI H3C SecBlade FW Cards H3C SecBlade FW Enhanced Cards H3C SecPath U200-A U200-M U200-S H3C SecPath U200-CA U200-CM U200-CS
