Network requirements, Configuration procedure – H3C Technologies H3C SecPath F1000-E User Manual
Page 146
136
{
URL: http://192.168.0.111:8080/portal.
[SecPathA] portal server newpt ip 192.168.0.111 key portal port 50100 url
http://192.168.0.111:8080/portal
# Enable Layer 3 portal authentication on the interface connecting SecPath B.
[SecPathA] interface gigabitethernet 0/2
[SecPathA–GigabitEthernet0/2] portal server newpt method layer3
[SecPathA–GigabitEthernet0/2] quit
On SecPath B, configure a default route to subnet 192.168.0.0/24, setting the next hop as 20.20.20.1.
(Details not shown.)
Configuring direct portal authentication with extended
functions
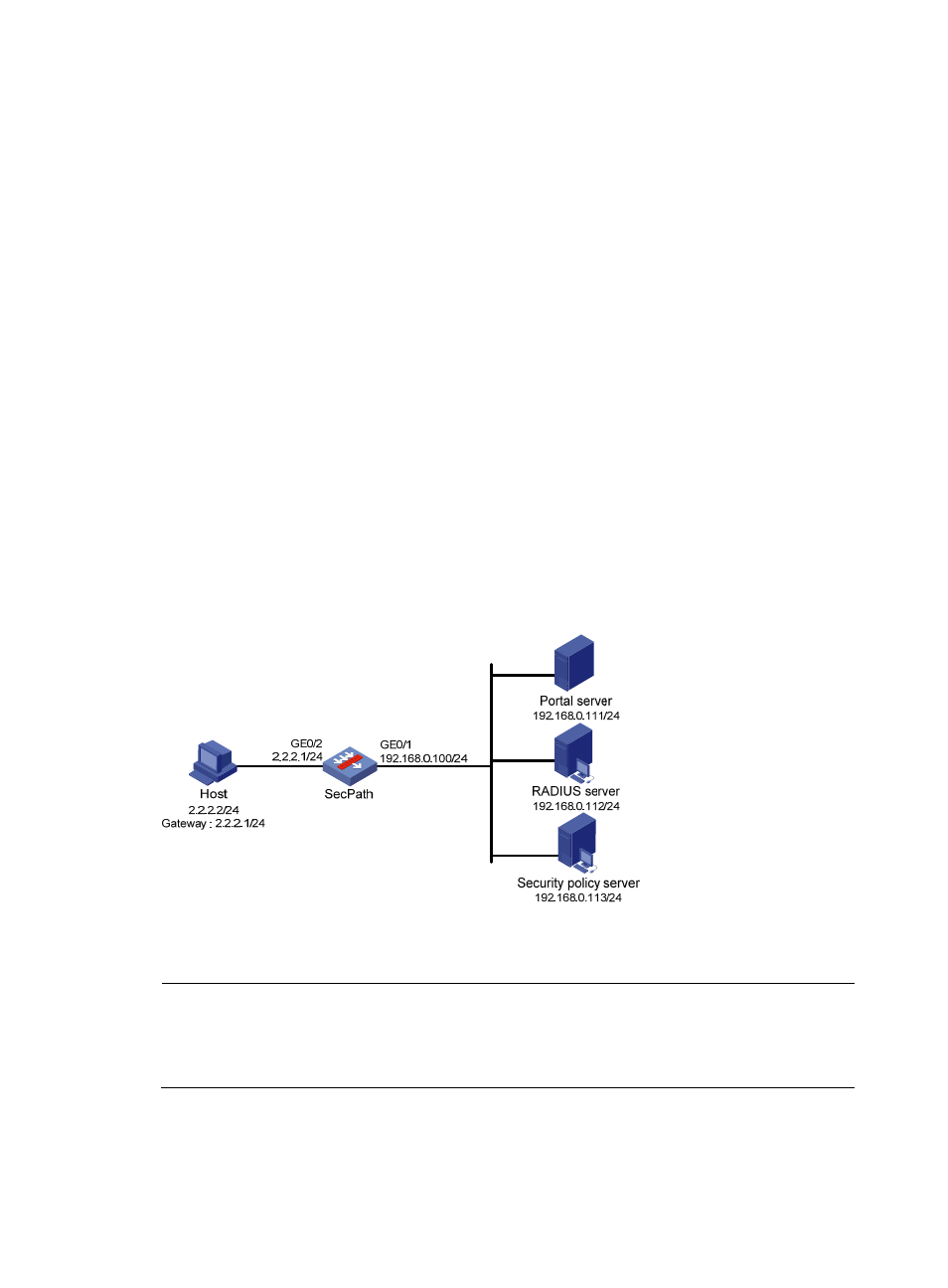
Network requirements
As shown in
:
•
The host is directly connected to the SecPath and the SecPath is configured for direct portal
authentication. The host is assigned with a public network IP address either manually or through
DHCP. If a user fails security check after passing identity authentication, the user can access only
subnet 192.168.0.0/24. After the user passes security check, the user can access Internet resources.
•
A RADIUS server serves as the authentication/accounting server.
Figure 120 Network diagram
Configuration procedure
NOTE:
•
Configure IP addresses for the host, SecPath, and servers as shown in
and make sure that
routes are available between devices before extended portal is enabled.
•
Configure the RADIUS server properly to provide authentication/accounting functions for users.
1.
Configure a RADIUS scheme on the SecPath:
# Create a RADIUS scheme named rs1 and enter its view.
- H3C SecPath F5000-A5 Firewall H3C SecPath F1000-A-EI H3C SecPath F1000-E-SI H3C SecPath F1000-S-AI H3C SecPath F5000-S Firewall H3C SecPath F5000-C Firewall H3C SecPath F100-C-SI H3C SecPath F1000-C-SI H3C SecPath F100-A-SI H3C SecBlade FW Cards H3C SecBlade FW Enhanced Cards H3C SecPath U200-A U200-M U200-S H3C SecPath U200-CA U200-CM U200-CS
