10 firewall thresholds, Figure 106 three-way handshake, Table 45 security > firewall > anti-probing – ZyXEL Communications NBG410W3G User Manual
Page 181
Chapter 9 Firewall
NBG410W3G Series User’s Guide
181
The following table describes the labels in this screen.
9.10 Firewall Thresholds
For DoS
attacks, the ZyXEL Device uses thresholds to determine when to start dropping
sessions that do not become fully established (half-open sessions). These thresholds apply
globally to all sessions.
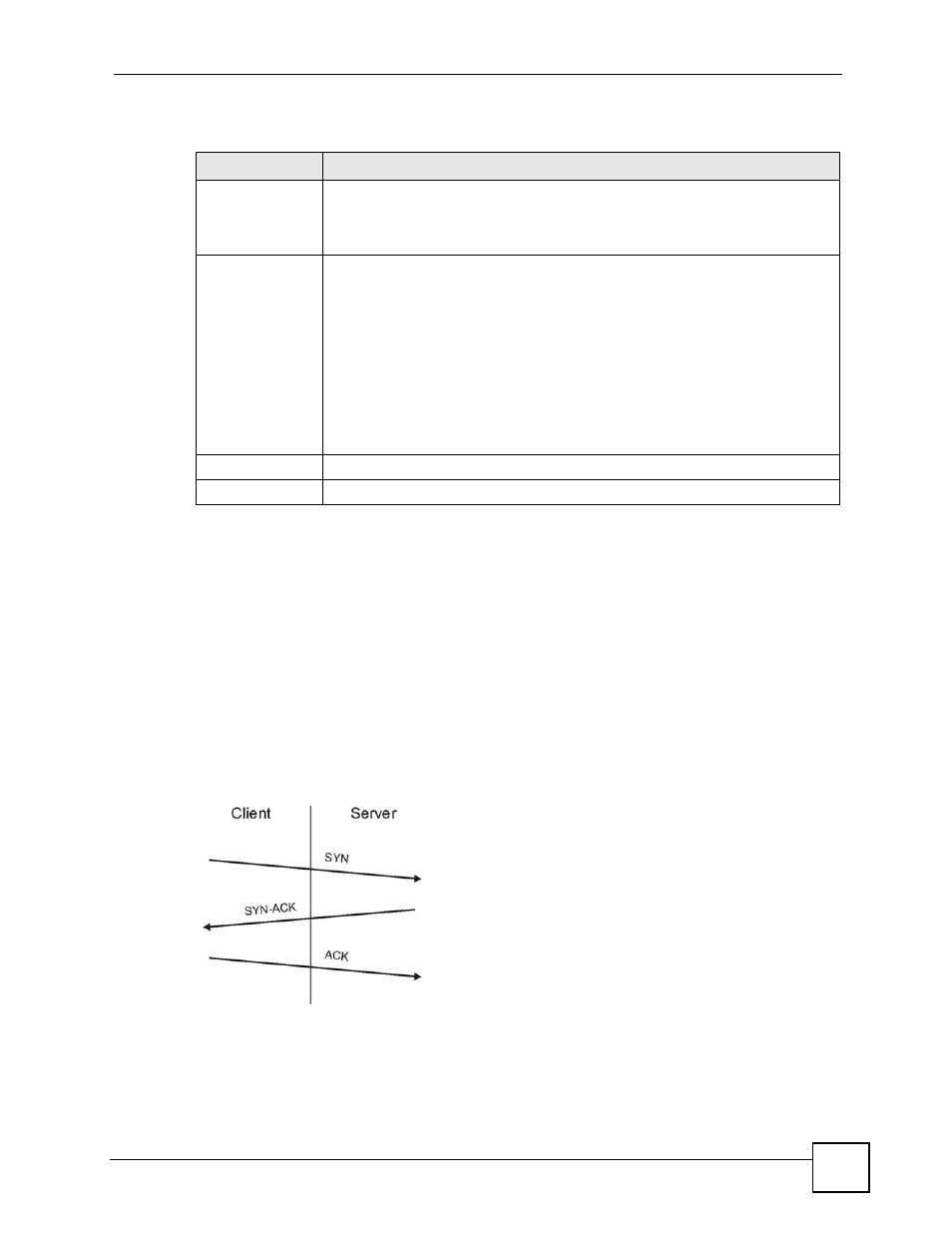
For TCP, half-open means that the session has not reached the established state-the TCP three-
way handshake has not yet been completed. Under normal circumstances, the application that
initiates a session sends a SYN (synchronize) packet to the receiving server. The receiver
sends back an ACK (acknowledgment) packet and its own SYN, and then the initiator
responds with an ACK (acknowledgment). After this handshake, a connection is established.
Figure 106 Three-Way Handshake
For UDP, half-open means that the firewall has detected no return traffic. An unusually high
number (or arrival rate) of half-open sessions could indicate a DOS attack.
Table 45 SECURITY > FIREWALL > Anti-Probing
LABEL
DESCRIPTION
Respond to PING
on
Select the check boxes of the interfaces that you want to reply to incoming Ping
requests.
Clear an interface’s check box to have the ZyXEL Device not respond to any Ping
requests that come into that interface.
Do not respond to
requests for
unauthorized
services.
Select this option to prevent hackers from finding the ZyXEL Device by probing for
unused ports. If you select this option, the ZyXEL Device will not respond to port
request(s) for unused ports, thus leaving the unused ports and the ZyXEL Device
unseen. If this option is not selected, the ZyXEL Device will reply with an ICMP
port unreachable packet for a port probe on its unused UDP ports and a TCP reset
packet for a port probe on its unused TCP ports.
Note that the probing packets must first traverse the ZyXEL Device's firewall rule
checks before reaching this anti-probing mechanism. Therefore if a firewall rule
stops a probing packet, the ZyXEL Device reacts based on the firewall rule to
either send a TCP reset packet for a blocked TCP packet (or an ICMP port-
unreachable packet for a blocked UDP packets) or just drop the packets without
sending a response packet.
Apply
Click Apply to save your changes.
Reset
Click Reset to begin configuring this screen afresh.
