Rm protection, Rm protection 81 – HP XP RAID Manager Software User Manual
Page 81
Using RAID Manager
81
RM protection
The RAID Manager protection facility restricts RM volume control
operations to volumes that:
• the host is allowed to see, with or without host-based LUN security
(Secure LUN XP)
• are listed in the RM configuration file.
To avoid inconsistency, RM security cannot be controlled within RM itself.
RM security is determined by command device definition within the SVP,
Remote Console, or via SNMP. Upon definition, the protection facility for
each command device can be enabled by setting an attribute. RM refers to
this attribute when it first recognizes the command device.
Command devices with protection ON permit access to volumes that are
not only on their list of allowed volumes, but are also host viewable.
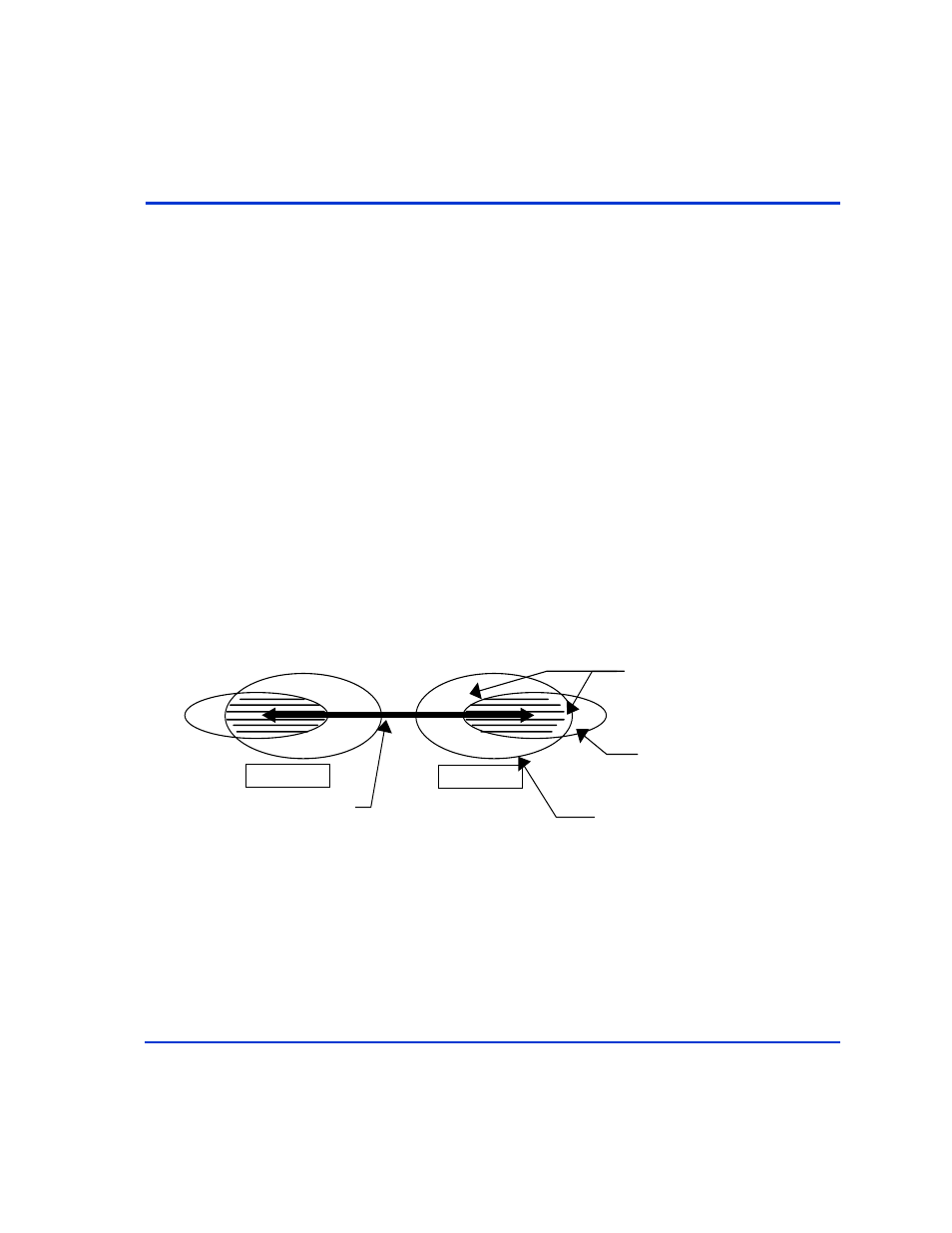
The following figure shows the definition of a protected (access refused)
volume:
Permitted volumes
Volumes within Host view via
LUN Security
Volumes in the horcm.conf file viewable via
protection ON command device
Protected (refused) volumes
HOST1
HOST2
- StorageWorks MSL6000 Tape Library (61 pages)
- Лент-е накопители HP StoreEver DAT (64 pages)
- Лент-е накопители HP StoreEver DAT (50 pages)
- StoreEver TapeAssure Software (40 pages)
- StoreEver Ultrium Tape Drives (75 pages)
- StoreEver Ultrium Tape Drives (60 pages)
- Linear Tape File System Software (28 pages)
- Linear Tape File System Software (25 pages)
- StoreEver Ultrium Tape Drives (78 pages)
- StoreEver Ultrium Tape Drives (76 pages)
- Linear Tape File System Software (20 pages)
- StoreEver Ultrium Tape Drives (61 pages)
- 2600fx Optical Disk Drive (65 pages)
- Ленточный автозагрузчик HP StorageWorks DAT 72x10 (58 pages)
- StorageWorks 1500cs Modular Smart Array (52 pages)
- StorageWorks 1500cs Modular Smart Array (71 pages)
- 2000fc Modular Smart Array (150 pages)
- StorageWorks 1000 Modular Smart Array (72 pages)
- StorageWorks 1000 Modular Smart Array (81 pages)
- StorageWorks 1500cs Modular Smart Array (48 pages)
- Servidor de almacenamiento HP ProLiant DL585 G2 (152 pages)
- Sistemas de almacenamiento de red HP StorageWorks X3000 (152 pages)
- Software de HP StoreVirtual VSA (127 pages)
- Software de HP StoreVirtual VSA (85 pages)
- X500 Data Vault (331 pages)
- StorageWorks 1000i Virtual Library System (122 pages)
- StorageWorks XP Remote Web Console Software (20 pages)
- 200 Storage Virtualization System (176 pages)
- XP Array Manager Software (101 pages)
- StorageWorks MSA 2.8 SAN Switch (307 pages)
- StorageWorks MSA 2.8 SAN Switch (22 pages)
- StorageWorks MSA 2.8 SAN Switch (104 pages)
- StorageWorks MSA 2.8 SAN Switch (270 pages)
- StorageWorks All-in-One SB600c Storage Blade (72 pages)
- StorageWorks All-in-One SB600c Storage Blade (80 pages)
- StorageWorks All-in-One SB600c Storage Blade (78 pages)
- StorageWorks All-in-One SB600c Storage Blade (60 pages)
- ProLiant DL585 G2 Storage-Server (150 pages)
- Data Protector Express Basic-Software (83 pages)
- Data Protector Express Basic-Software (93 pages)
- ProLiant DL185 G5 Storage Server (174 pages)
- ProLiant High Availability Storage Server (72 pages)
- 2000I G2-Modular-Smart-Array (48 pages)
- P2000 G3 MSA Array Systems (58 pages)
- StorageWorks 2000fc G2 Modular Smart Array (76 pages)
