Keep alive, Nat traversal, 6 keep alive – ZyXEL Communications ZyXEL ZyAIR 100 User Manual
Page 212: 7 nat traversal
ZyWALL 10~100 Series Internet Security Gateway
15-6
VPN
Screens
15.6 Keep Alive
When you initiate an IPSec tunnel with keep alive enabled, the ZyWALL automatically renegotiates the
tunnel when the IPSec SA lifetime period expires (see section 15.11 for more on the IPSec SA lifetime). In
effect, the IPSec tunnel becomes an “always on” connection after you initiate it. Both IPSec routers must
have a ZyWALL-compatible keep alive feature enabled in order for this feature to work.
If the ZyWALL has its maximum number of simultaneous IPSec tunnels connected to it and they all have
keep alive enabled, then no other tunnels can take a turn connecting to the ZyWALL because the ZyWALL
never drops the tunnels that are already connected. Check Table 1-1 Model Specific Features in chapter 1 to
see how many simultaneous IPSec SAs your ZyWALL model can support.
When there is outbound traffic with no inbound traffic, the ZyWALL automatically
drops the tunnel after two minutes.
15.7 NAT Traversal
NAT traversal allows you to set up a VPN connection when there are NAT routers between the two IPSec
routers.
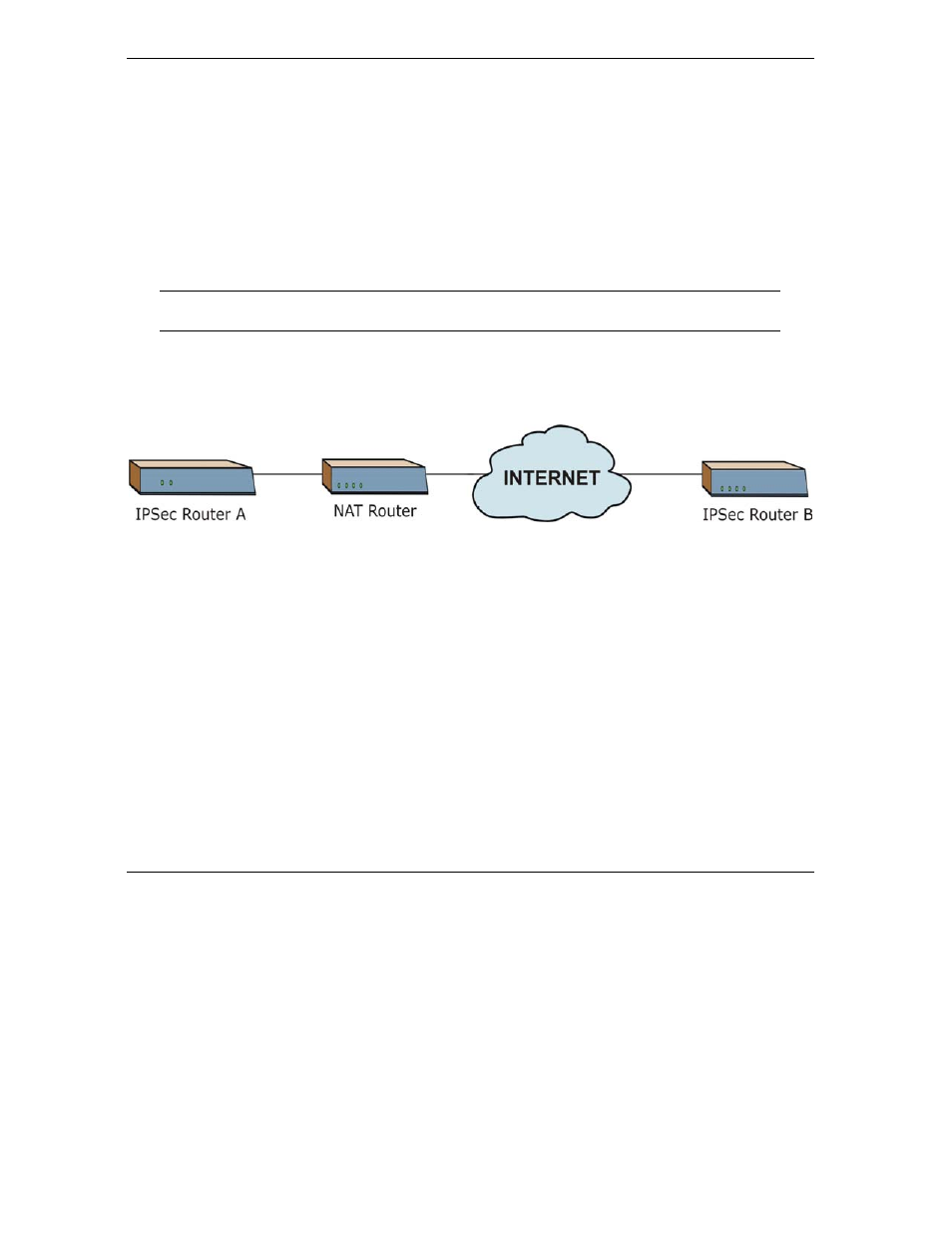
Figure 15-3 NAT Router Between IPSec Routers
Normally you cannot set up a VPN connection with a NAT router between the two IPSec routers because the
NAT router changes the header of the IPSec packet. In the previous figure, IPSec router A sends an IPSec
packet in an attempt to initiate a VPN. The NAT router changes the IPSec packet’s header so it does not
match the header for which IPSec router B is checking. Therefore, IPSec router B does not respond and the
VPN connection cannot be built.
NAT traversal solves the problem by adding a UDP port 500 header to the IPSec packet. The NAT router
forwards the IPSec packet with the UDP port 500 header unchanged. IPSec router B checks the UDP port
500 header and responds. IPSec routers A and B build a VPN connection.
15.7.1 NAT Traversal Configuration
For NAT traversal to work you must:
Use ESP security protocol (in either transport or tunnel mode).
Use IKE keying mode.
