Network requirements, Network diagram, Configuration procedure – H3C Technologies H3C S3100 Series Switches User Manual
Page 546
3-14
# Set the circuit ID sub-option in DHCP packets from VLAN 1 to “abcd” on Ethernet 1/0/3.
[Switch] interface Ethernet1/0/3
[Switch-Ethernet1/0/3] dhcp-snooping information vlan 1 circuit-id string abcd
Unauthorized DHCP Server Detection Configuration Example
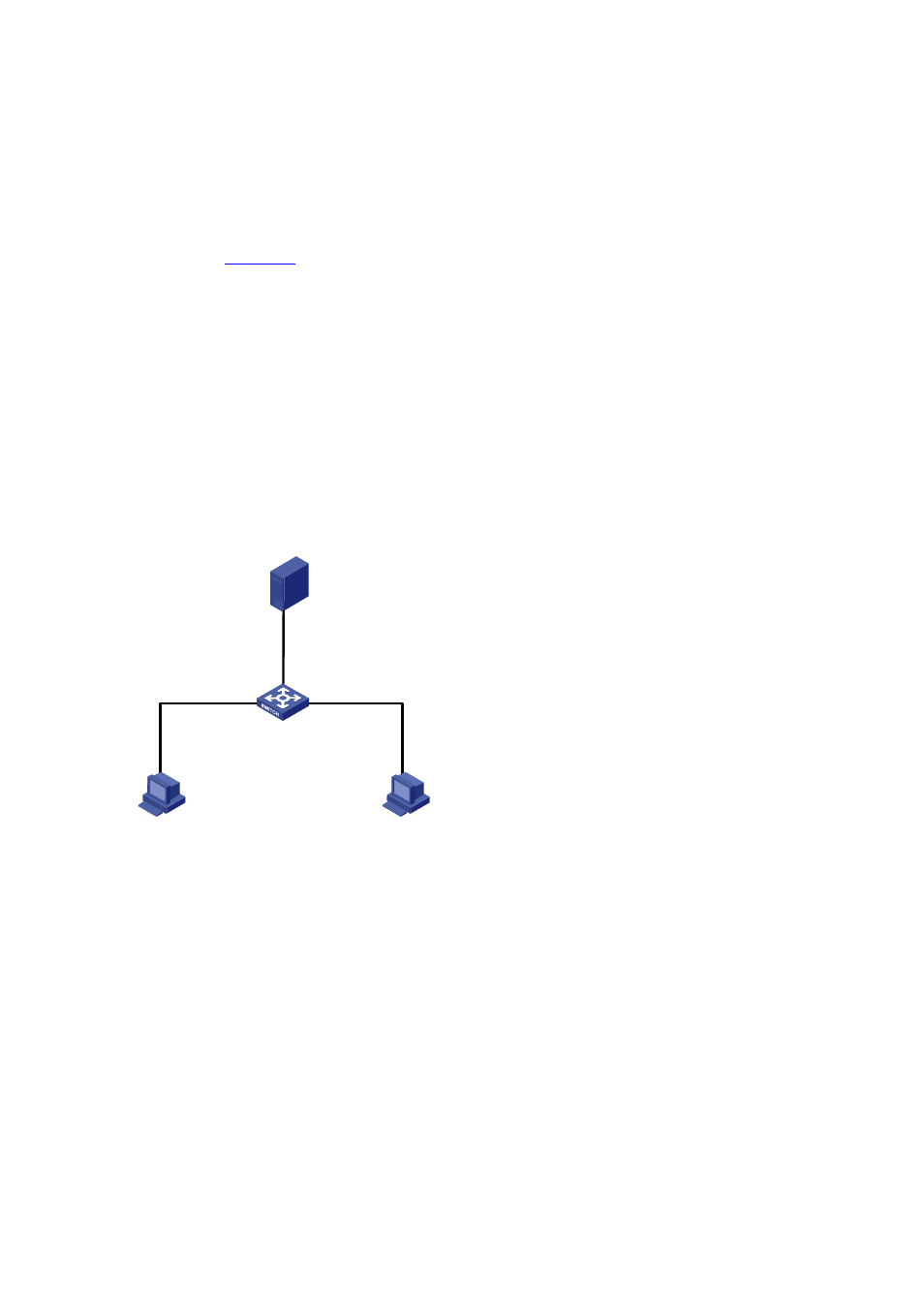
Network requirements
As shown in
, Ethernet 1/0/1 of the switch (S3100-SI) is connected to the DHCP server, and
Ethernet 1/0/2 and Ethernet 1/0/3 are respectively connected to Client A, Client B.
z
Enable DHCP snooping on the switch.
z
Enable unauthorized DHCP server detection on Ethernet 1/0/2 and Ethernet 1/0/3. When an
authorized DHCP server is detected on Ethernet 1/0/2, a trap message will be sent; when an
authorized DHCP server is detected on Ethernet 1/0/3, the interface is shut down administratively.
z
To prevent attackers from filtering the detecting DHCP-DISCOVER packets, specify the source
MAC address for such packets as 000f-e200-1111 (different from the bridge MAC address of the
switch) on the switch.
Network diagram
Figure 3-9 Network diagram for unauthorized DHCP server detection
Eth1/0/1
DHCP server
Switch
Eth1/0/2
Eth1/0/3
ClientA
ClientB
Configuration procedure
# Enable DHCP snooping.
Enter system view, return to user view with Ctrl+Z.
[Sysname] dhcp-snooping
# Specify the source MAC address for the DHCP-DISCOVER messages as 000f-e200-1111.
[Sysname] dhcp-snooping server-guard source-mac 000f-e200-1111
# Enable unauthorized DHCP server detection on Ethernet 1/0/2.
[Sysname] interface ethernet1/0/2
[Sysname-Ethernet1/0/2] dhcp-snooping server-guard enable
# Specify the method for handling unauthorized DHCP servers as trap on Ethernet 1/0/2.
[Sysname-Ethernet1/0/2] dhcp-snooping server-guard method trap
