Introduction to arp attack detection, Man-in-the-middle attack, Arp attack detection – H3C Technologies H3C S3100 Series Switches User Manual
Page 488
1-4
Introduction to ARP Attack Detection
Man-in-the-middle attack
According to the ARP design, after receiving an ARP response, a host adds the IP-to-MAC mapping of
the sender into its ARP mapping table even if the MAC address is not the real one. This can reduce the
ARP traffic in the network, but it also makes ARP spoofing possible.
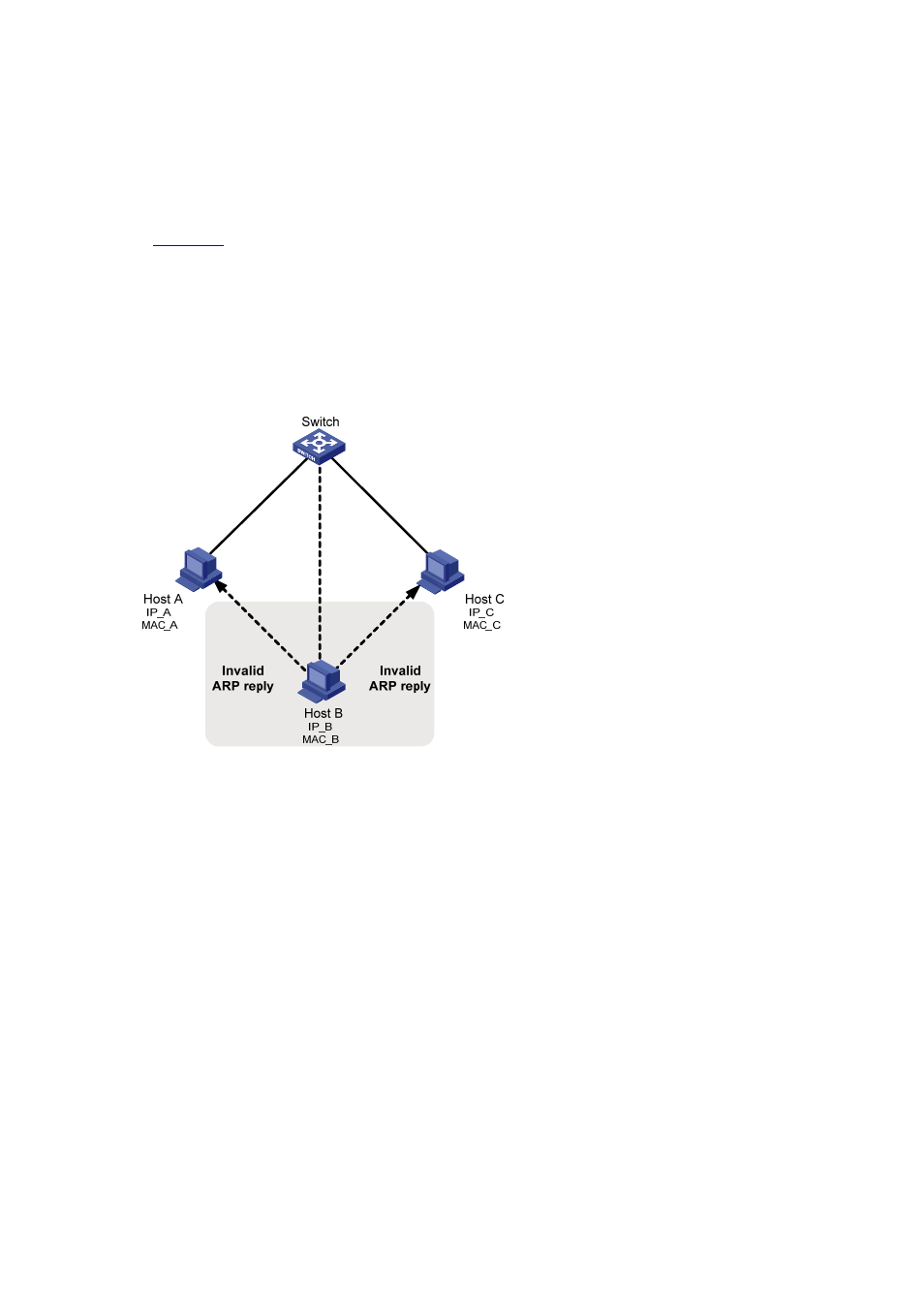
, Host A communicates with Host C through a switch. To intercept the traffic between Host
A and Host C, the hacker (Host B) forwards invalid ARP reply messages to Host A and Host C
respectively, causing the two hosts to update the MAC address corresponding to the peer IP address in
their ARP tables with the MAC address of Host B. Then, the traffic between Host A and C will pass
through Host B which acts like a “man-in-the-middle” that may intercept and modify the communication
information. Such attack is called man-in-the-middle attack.
Figure 1-3 Network diagram for ARP man-in-the-middle attack
ARP attack detection
To guard against the man-in-the-middle attacks launched by hackers or attackers, S3100-EI series
Ethernet switches support the ARP attack detection function. All ARP (both request and response)
packets passing through the switch are redirected to the CPU, which checks the validity of all the ARP
packets by using the DHCP snooping table or the manually configured IP binding table. For description
of DHCP snooping table and the manually configured IP binding table, refer to the DHCP snooping
section in the part discussing DHCP in this manual.
After you enable the ARP attack detection function, the switch will check the following items of an ARP
packet: the source MAC address, source IP address, port number of the port receiving the ARP packet,
and the ID of the VLAN the port resides. If these items match the entries of the DHCP snooping table or
the manual configured IP binding table, the switch will forward the ARP packet; if not, the switch
discards the ARP packet.
z
With trusted ports configured, ARP packets coming from the trusted ports will not be checked,
while those from other ports will be checked through the DHCP snooping table or the manually
configured IP binding table.
z
With the ARP restricted forwarding function enabled, ARP request packets are forwarded through
trusted ports only; ARP response packets are forwarded according to the MAC addresses in the
