8 content filter policy: schedule – ZyXEL Communications ZyWALL 2 Plus User Manual
Page 239
Chapter 12 Content Filtering Screens
ZyWALL 2 Plus User’s Guide
239
12.8 Content Filter Policy: Schedule
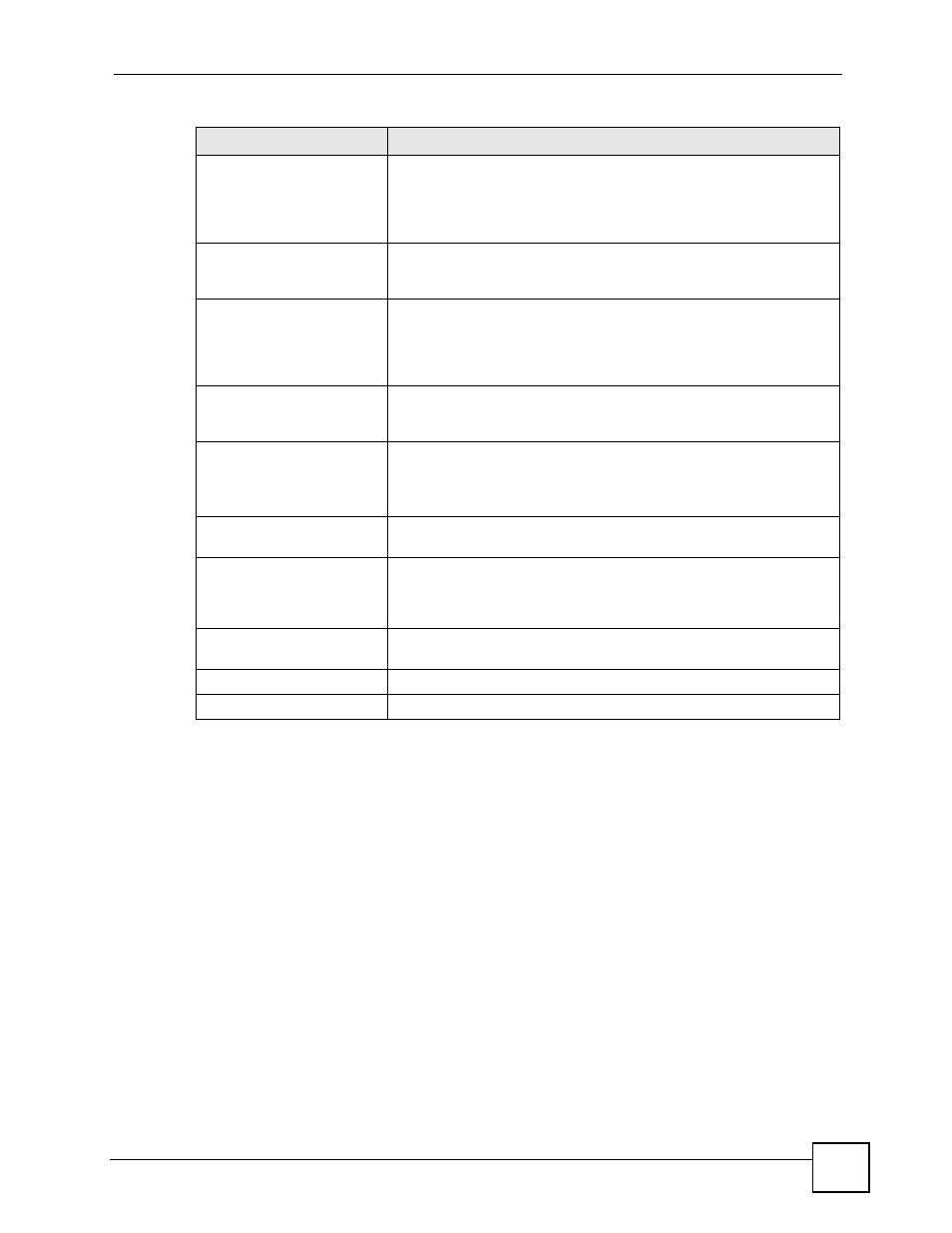
Click SECURITY > CONTENT FILTER > Policy and then a policy’s schedule icon to
display the following screen.
Use this screen to set for which days and times the policy applies.
Available Trusted Object
This list displays the trusted host names you configured in the
SECURITY > CONTENT FILTER > Object screen (click Available
Trusted Object to go there). Select the ones to which you want to allow
access and use the arrow button to move them to the Trusted Web
Sites list.
Trusted Web Sites
This list displays web sites to which this content filtering policy allows
access. Select an entry and use the arrow button to remove it from the
list.
Available Forbidden Object
This list displays the forbidden host names you configured in the
SECURITY > CONTENT FILTER > Object screen (click Available
Forbidden Object to go there). Select the ones you want this policy to
block and use the arrow button to move them to the Forbidden Web
Sites list.
Forbidden Web Sites
This list displays web sites to which this content filtering policy blocks
access. Select an entry and use the arrow button to remove it from the
list.
Keyword Blocking
Keyword blocking allows you to block websites with URLs that contain
certain keywords in the domain name or IP address.
See
for how to set how much of the URL the
ZyWALL checks.
Block Web sites which
contain these keywords.
Select this checkbox to enable keyword blocking.
Available Keyword Object
This list displays the keywords you configured in the SECURITY >
CONTENT FILTER > Object screen (click Available Keyword Object
to go there). Select the ones you want this policy to block and use the
arrow button to move them to Keyword List.
Keyword List
This list displays the keywords that this content filtering policy blocks.
Select an entry and use the arrow button to remove it from the list.
Apply
Click Apply to save your settings and exit this screen.
Cancel
Click Cancel to exit this screen without saving.
Table 60 SECURITY > CONTENT FILTER > Policy > Customization (continued)
LABEL
DESCRIPTION
