2 ike sa proposal, 3 diffie-hellman (dh) key exchange – ZyXEL Communications G.SHDSL.bis 4-port Security Gateway P-793H User Manual
Page 157
P-793H User’s Guide
Chapter 11 IPSec VPN
157
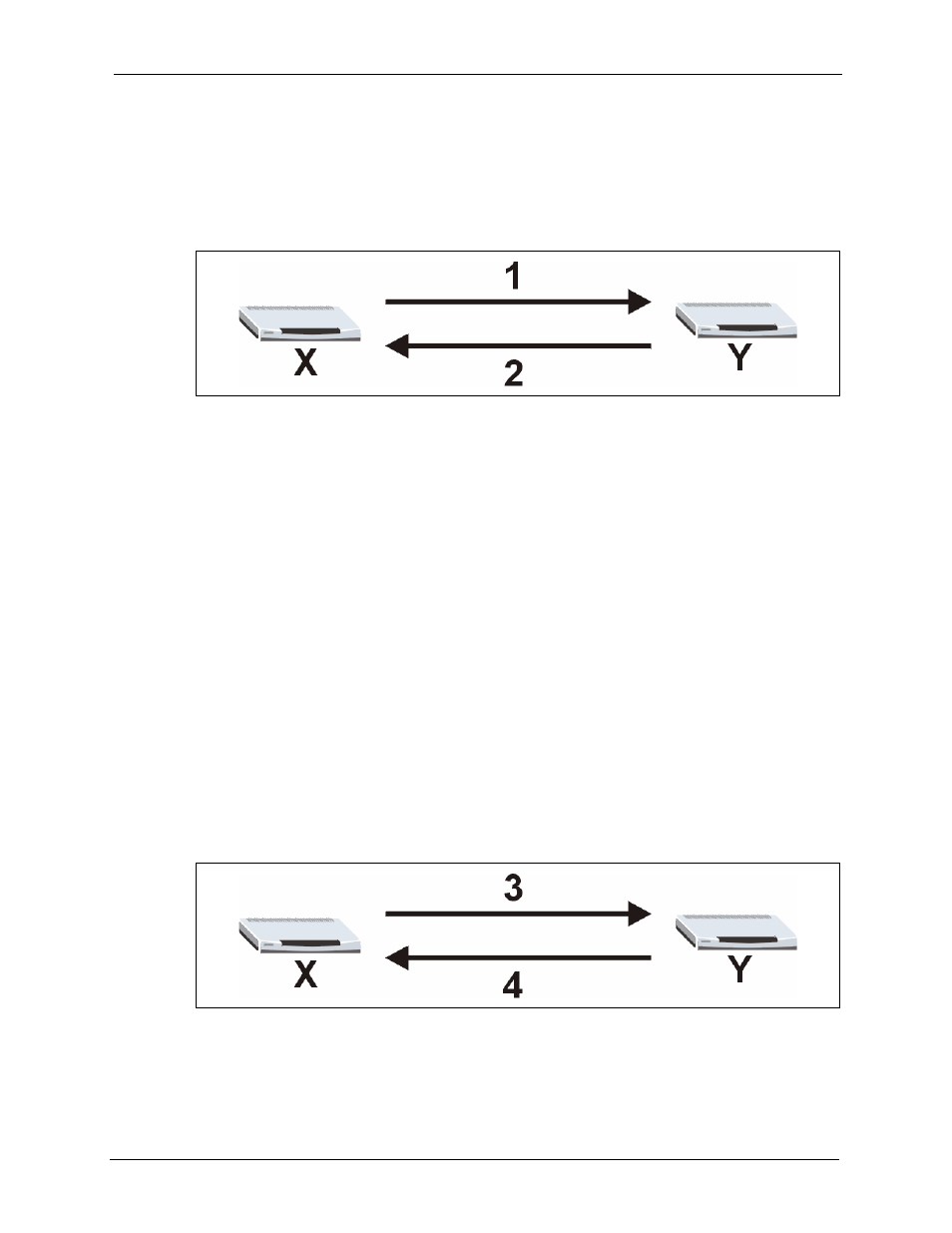
11.1.1.2 IKE SA Proposal
The IKE SA proposal is used to identify the encryption algorithm, authentication algorithm,
and Diffie-Hellman (DH) key group that the ZyXEL Device and remote IPSec router use in
the IKE SA. In main mode, this is done in steps 1 and 2, as illustrated below.
Figure 73 IKE SA: Main Negotiation Mode, Steps 1 - 2: IKE SA Proposal
The ZyXEL Device sends one or more proposals to the remote IPSec router. (In some devices,
you can set up only one proposal.) Each proposal consists of an encryption algorithm,
authentication algorithm, and DH key group that the ZyXEL Device wants to use in the IKE
SA. The remote IPSec router selects an acceptable proposal and sends the accepted proposal
back to the ZyXEL Device. If the remote IPSec router rejects all of the proposals (for example,
if the VPN tunnel is not configured correctly), the ZyXEL Device and remote IPSec router
cannot establish an IKE SA.
Note: Both routers must use the same encryption algorithm, authentication algorithm,
and DH key group.
See the field descriptions for information about specific encryption algorithms, authentication
algorithms, and DH key groups. You can also see
for more
information about the role of DH key groups.
11.1.1.3 Diffie-Hellman (DH) Key Exchange
The ZyXEL Device and the remote IPSec router use a DH key exchange to establish a shared
secret, which is used to generate encryption keys for IKE SA and IPSec SA. In main mode, the
DH key exchange is done in steps 3 and 4, as illustrated below.
Figure 74 IKE SA: Main Negotiation Mode, Steps 3 - 4: DH Key Exchange
The DH key exchange is based on DH key groups. Each key group is a fixed number of bits
long. The longer the key, the more secure the encryption keys, but also the longer it takes to
encrypt and decrypt information. For example, DH2 keys (1024 bits) are more secure than
DH1 keys (768 bits), but DH2 encryption keys take longer to encrypt and decrypt.
