Red Lion IndustrialPr 6000 Router User Manual
Page 80
Software User Guide
80
Network Tab
Tunnel Type: Controls the initial mode of the tunnel at startup. The options given to IPsec will be:
Client: auto=start
Server: auto=add
Dynamic: auto=route
For more information, please consult an IPsec user guide on aspects of these specific modes.
Negotiation Mode: As a default, this field is set to Main mode ISAKMP Negotiation. When using dynamic, or DHCP
issued IP addresses (for example with cellular cards), some remote devices may require the use of Aggressive Mode
ISAKMP Negotiation. Should you encounter this situation, you can perform aggressive mode ISAKMP negotiation by
changing this parameter from “Main” to “Aggressive ISAKMP”. To use Aggressive ISAKMP Negotiations, select Yes from
the list provided or No to prevent it’s use.
Dead Peer Detection Action: This feature can help detect when a remote end‐point is no longer communicating prop‐
erly. Once an error is detected, the “hold” state will only renegotiate the tunnel after new traffic destined for the tun‐
nel is detected. The “restart” state will attempt to immediately re‐establish the connection to the concentrator. For
this reason, “restart” may use more bandwidth and may not be the ideal choice for a limited data plan. However, if a
host at the central site needs to initiate connections down to a local device through the tunnel, “restart” may be nec‐
essary so that the tunnel is always up and waiting for new data from the concentrator.
Use Perfect Forward Secrecy: Specifies whether or not the tunnel will use Perfect Forward Secrecy when negotiation
cryptography parameters with the remote device. Note: This parameter must be set the same on the devices on both
sides of the tunnel in order for a Security Association (SA) to be established. This is one of the first things that should
be checked when tunnel negotiation difficulties are encountered.
•
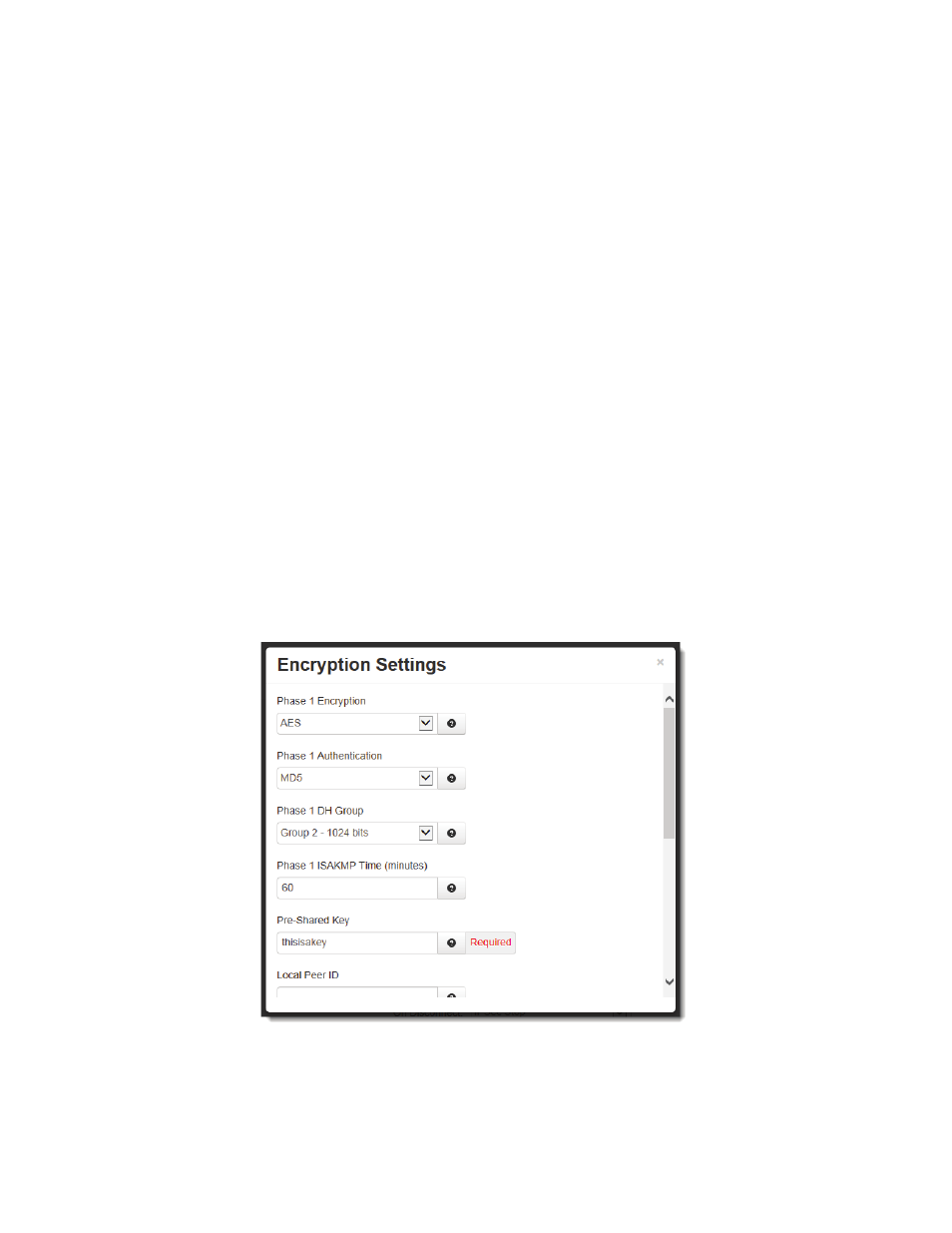
Click on the NEXT button and the following Encryption Settings dialog window will appear:
Phase 1 Encryption: Select the type of encryption needed for phase 1 (IKE).
Phase 1 Authentication: Select the type of authentication needed for phase 1 (IKE).
