Ssl performance – Comtrol Hub DeviceMaster User Manual
Page 80
80 - DeviceMaster Security
DeviceMaster Installation and Configuration Guide: 2000594 Rev. A
SSL Performance
-
RSA Server Certificate used by SSL servers
• This is the RSA identity certificate that the DeviceMaster uses during
SSL/TLS handshaking to identify itself. It is used most frequently by
SSL server code in the DeviceMaster when clients open connections to
the DeviceMaster's secure web server or other secure TCP ports. If a
DeviceMaster serial port configuration is set up to open (as a client), a
TCP connection to another server device, the DeviceMaster also uses
this certificate to identify itself as an SSL client if requested by the
server.
• In order to function properly, this certificate must be signed using the
Server RSA Key. This means that the server RSA certificate and server
RSA key must be replaced as a pair.
-
DH Key pair used by SSL servers
This is a private/public key pair that is used by some cipher suites to
encrypt the SSL/TLS handshaking messages.
Possession of the private portion of the key pair allows an eavesdropper to
decrypt traffic on SSL/TLS connections that use DH encryption during
handshaking.
-
Client Authentication Certificate used by SSL servers
If configured with a CA certificate, the DeviceMaster requires all SSL/TLS
clients to present an RSA identity certificate that has been signed by the
configured CA certificate. As shipped, the DeviceMaster is not configured
with a CA certificate and all SSL/TLS clients are allowed.
SSL Performance
The DeviceMaster has these SSL performance characteristics:
•
Encryption/decryption is a CPU-intensive process, and using encrypted data
streams will limit the number of ports that can be maintained at a given serial
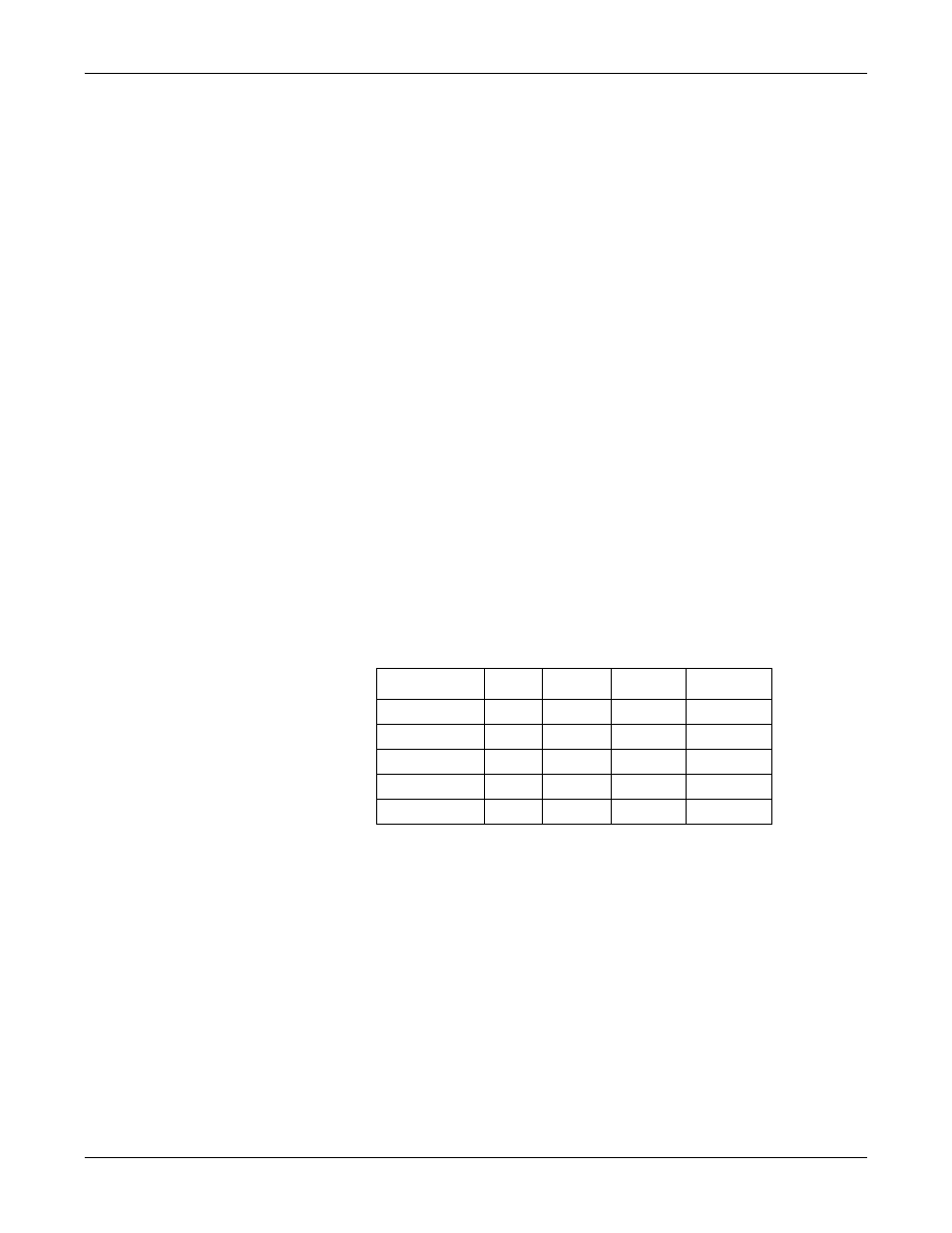
throughput. For example, the table below shows the number of ports that can
be maintained by SocketServer at 100% throughput for various cipher suites
and baud rates.
Note: These throughputs required 100% CPU usage, so other features such as the
web server are very unresponsive at the throughputs shown above. To
maintain a usable web interface, one would want to stay well below the
maximum throughput/port numbers above.
•
The overhead required to set up an SSL connection is significant. The time
required to open a connection to SocketServer varies depending on the public-
key encryption scheme used for the initial handshaking. These are typical
setup times for the three public-key encryption schemes for the DeviceMaster:
-
RSA 0.66 seconds
-
DHE 3.84 seconds
-
DHA 3.28 seconds
•
Since there is a certain amount of overhead for each block of data sent/
received on an SSL connection, the SocketServer polling rate and size of bocks
that are written to the SocketServer also has a noticeable effect on CPU usage.
Writing larger blocks of data and a slower SocketServer polling rate will
decrease CPU usage and allow somewhat higher throughputs.
9600
38400
57600
115200
RC4-MD5
32
16
10
5
RC4-SHA
32
13
9
4
AES128-SHA 28
7
5
2
AES256-SHA 26
7
4
2
DES3-SHA
15
3
2
1
