Weldscore, Checkpoint™ cloud-based architecture – Lincoln Electric IM8000 CHECKPOINT User Manual
Page 20
Chapter 1. General Information
WeldScore™
1.4
CheckPoint™ User Manual
IM8000
Mobile Devices
With CheckPoint™, you can download native apps for iPhone®, Blackberry® and Android to provide mobile
users access to their welder data anytime from anywhere. Users can view dashboard widgets, history and
alarm events, receive real-time text and e-mail messages, download the latest documents, and scan
barcodes as part of an easy-to-use traceability solution.
Links for downloading mobile applications are available at
www.lincolncheckpoint.com
under the Mobile
Enabled portion of the home page. For more information on using the mobile version, please refer to the
CheckPoint™ Mobile App User Manual.
WeldScore™
WeldScore™, a new feature available in all third-generation Welding Power Source models (including the
i400, C300, S350, S500 and AC/DC 1000 SD), can be used to support a weld quality control program. It
assigns a score to welds on a 0% to 100% scale that indicates the acceptability of the weld. The score is
based on a comparison to previously trained welding conditions. Any weld with a score of 85% to 90% or
above can be considered, with a reasonable amount of confidence, to be an acceptable weld. WeldScore™
can be used independently on the power source or together with CheckPoint™. Please refer to the Power
Wave® Manager User Manual for more in-depth information on WeldScore™.
NOTE |
WeldScore™ is not a guarantee of quality and is not
intended to replace a quality control system.
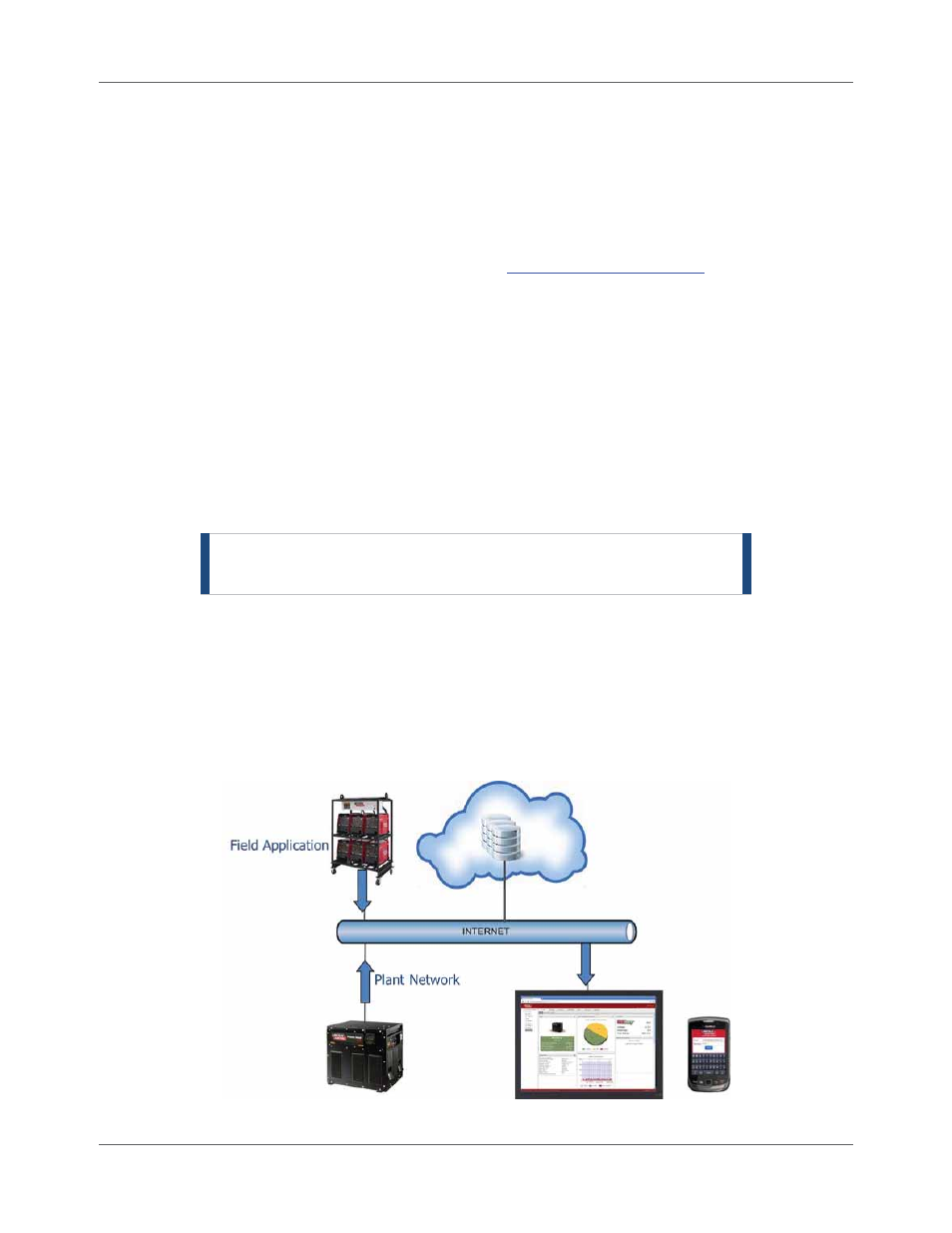
CheckPoint™ Cloud-Based Architecture
The CheckPoint™ system uses a cloud-based architecture. This means that there is no dedicated computer
required at your company to collect and store the data. Each piece of welding equipment simply requires a
network connection. The Welding Power Source initiates the transfer of information through firewall-
friendly communications to the data center. (The data transfer does not initiate from outside the power
source.) At that point, the data is accessible using a web browser and a secure login.
Figure 1.1 CheckPoint™ Cloud-Based Architecture
