1 encryption, 2 authentication, 1 encryption 6.2.2 authentication – ZyXEL Communications ZyXEL ZyWALL 5 User Manual
Page 103: Figure 30 zywall wireless security levels
ZyWALL 5 User’s Guide
102
Chapter 6 Wireless LAN
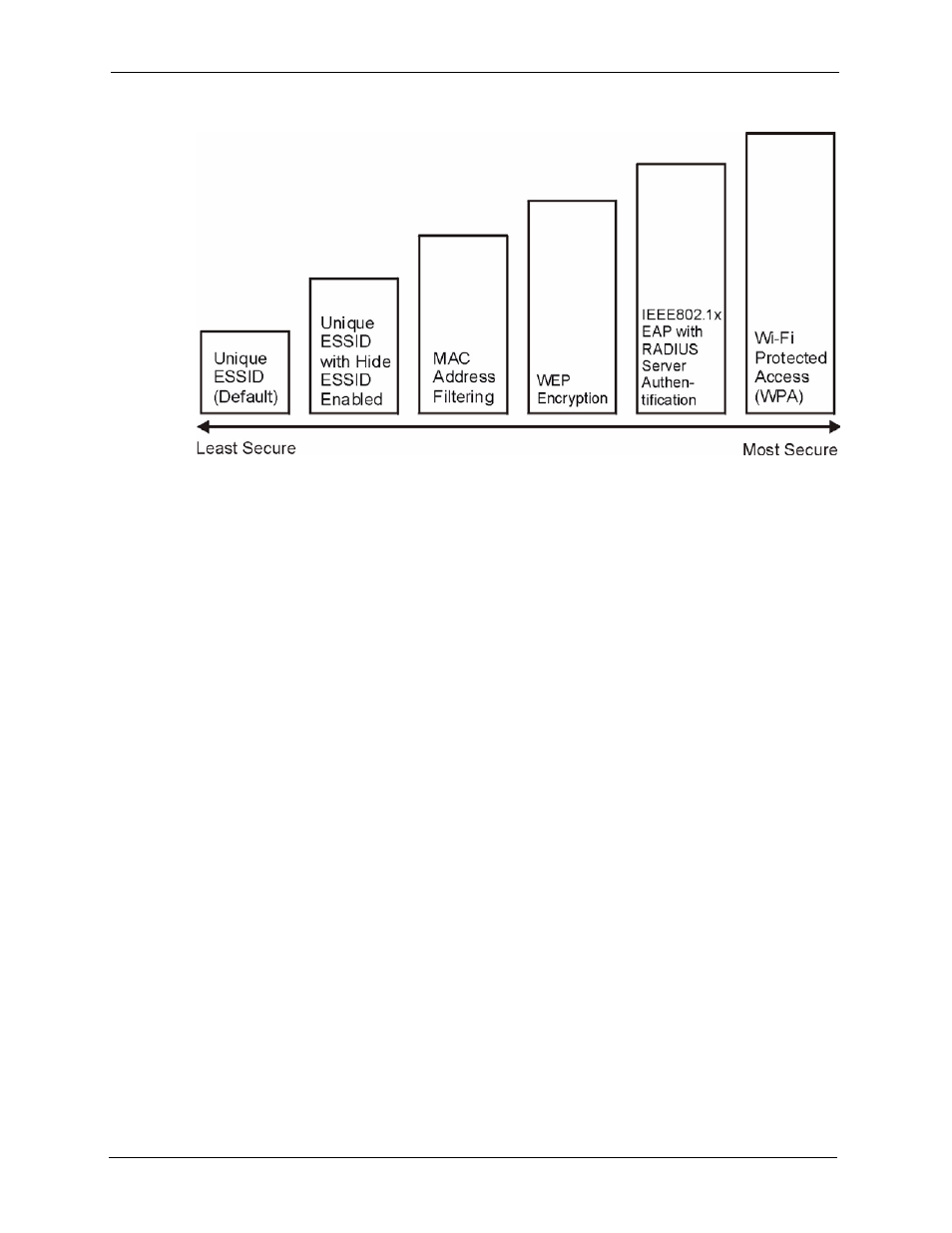
Figure 30 ZyWALL Wireless Security Levels
If you do not enable any wireless security on your ZyWALL, your network is accessible to any
wireless networking device that is within range.
Use the ZyWALL web configurator to set up your wireless LAN security settings. Refer to the
chapter on using the ZyWALL web configurator to see how to access the web configurator.
6.2.1 Encryption
• Use WPA security if you have WPA-aware wireless clients and a RADIUS server. WPA
has user authentication and improved data encryption over WEP.
• Use WPA-PSK if you have WPA-aware wireless clients but no RADIUS server.
• If you don’t have WPA-aware wireless clients, then use WEP key encrypting. A higher
bit key offers better security at a throughput trade-off.
6.2.2 Authentication
Use a RADIUS server with WPA or IEEE 802.1x key management protocol. You can also
configure IEEE 802.1x to use the built-in database (Local User Database) to authenticate
wireless clients before joining your network.
• Use RADIUS authentication if you have a RADIUS server. See the appendices for
information on protocols used when a client authenticates with a RADIUS server via the
ZyWALL.
• Use the Local User Database if you have less than 32 wireless clients in your network.
The ZyWALL uses MD5 encryption when a client authenticates with the Local User
Database
