Activity log, Fields in the activity log, Values for the detail field in the activity log – HP Secure Key Manager User Manual
Page 253
Activity Log
The Activity Log contains a record of each request received by the KMS Server. For client requests
that contain multiple cryptographic operations, each operation is logged as a separate entry in the
Activity Log. Requests for cryptographic operations are not logged until the KMS Server has received
all the data from the client or an error has occurred. When there is no data for a particular field, a
dash is inserted. The format of the Activity Log is as follows:
The following table describes the fields that are present in the Activity Log.
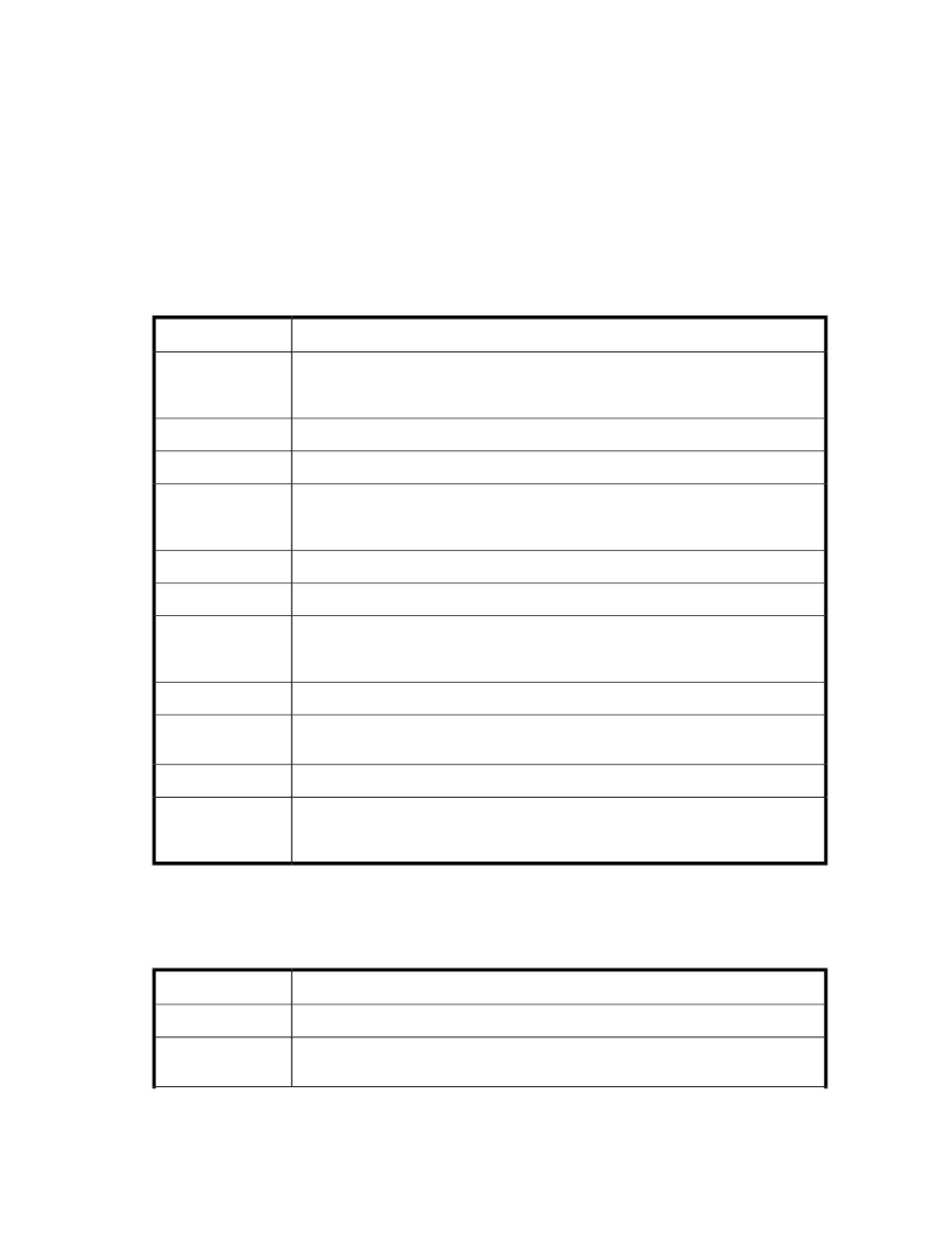
Table 127 Fields in the Activity Log
Description
Field
enclosed in brackets ( [] ), the date field shows the date and time that the SKM finished
processing the request, specified in the local time zone. The date and time are repres-
ented as follows: yyyy-mm-dd hh:mm:ss.
date
ERROR or INFO, depending on the result of the request
priority
IP address of the client machine
ip
enclosed in brackets ( [] ), the common name field displays the common name defined
in the certificate that was provided by the client. This field only has data when you re-
quire client authentication.
common name
authenticated user that issued the request
user
request ID of the client request
request id
type of client request; the request type field is the name of the XML request without the
suffix “Request.” For example, a KeyGenRequest log entry would have a request type
value of “KeyGen.”
request type
name of the key specified in the request
key
enclosed in brackets ( [] ), the detail field provides different information based on the
type of request; the details field is described in
.
detail
numerical error code returned to the client
error code
enclosed in brackets ( [] ), the message field displays either “Success” if the server was
able to fulfill the request, or, if there was an error, this field displays the error message
that coincides with the appropriate numerical error code
message
As mentioned, the detail field provides different information depending on what the client requests.
The following table lists the different types of requests the client might submit and then describes what
information is present in the detail field for each request.
Table 128 Values for the Detail Field in the Activity Log
Detail Information
Request Type
username provided by the client
authentication
algorithm and key size; the value for the Deletable and Exportable options are listed
as well if they are set by the client
key generation
Secure Key Manager
253
