Configuring the kms server, Authentication overview – HP Secure Key Manager User Manual
Page 184
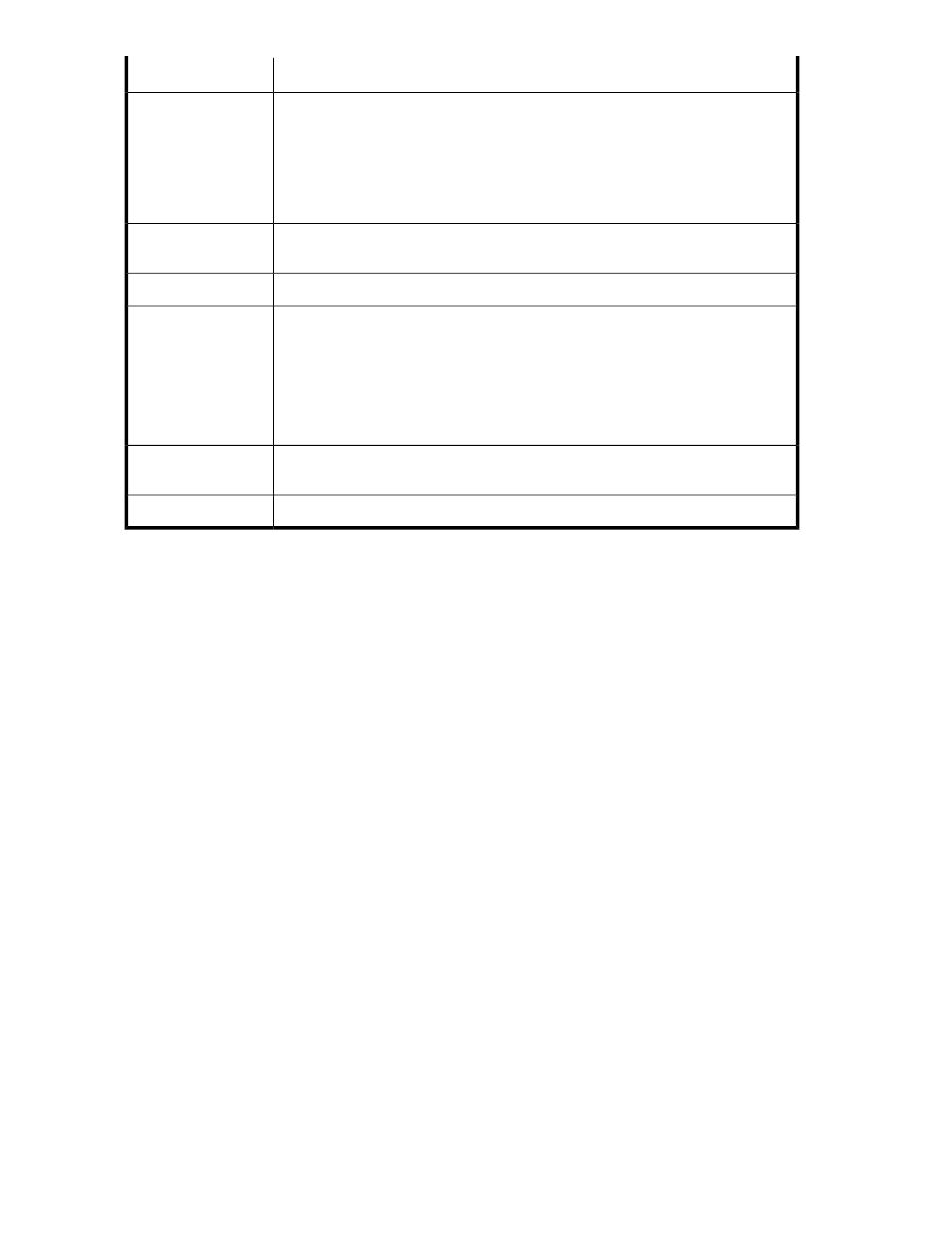
Description
Component
This field specifies the Hash function to use for SSL session integrity. The supported
Hash functions are:
•
SHA–1: (Secure Hash Algorithm). SHA–1 operates on 64–byte blocks of data
and produces a 160–bit authentication value.
•
MD5: (Message Digest algorithm). MD5 operates on 64–byte blocks of data and
produces a 128–bit authentication value.
Hash
This field allows you to mandate that only high security ciphers (128–bit and above)
are used within an organization.
Disable Low Security
Ciphers
Click Up and Down to arrange the SSL Cipher order.
Up / Down
Click Enable and Disable to enable and disable the selected cipher.
NOTE:
Enabling RC4 ciphers or any RSA Low Security ciphers on a FIPS-compliant
device will take the device out of FIPS compliance - possibly in a manner that
does not comply with FIPS standards. For information on disabling FIPS
compliance, see
Enable
Click the Disable Low Security Ciphers to disable the low security ciphers.
Disable Low Security
Ciphers
Click Restore Defaults to restore the original SSL cipher order.
Restore Defaults
Configuring the KMS Server
The HP StorageWorks Secure Key Manager allows you to off-load cryptographic operations from
application servers and other back-end devices to the SKM. Clients, such as application servers and
databases, make requests to the KMS Server to perform cryptographic operations. The KMS Server
is capable of performing such cryptographic operations as asymmetric and symmetric encryption and
decryption, MACs and MAC verifies, keyed hashes, digital signatures and verifications, RNG, and
combinations of these operations. This chapter contains the following topics:
• Authentication Overview
• Key Management Services Configuration Sections
• KMS Server Procedures
• Health Check Overview
• Health Check Sections
Authentication overview
The communication between the KMS client and the server varies slightly, depending on whether your
KMS configuration requires users to authenticate. If you decide not to authenticate, then users have
access only to global keys. Global keys are keys that are available to everyone, with no authentication
required.
If you want to require authentication, then you must create keys for each user or group of users. An
authenticated user has access to all global keys, all the keys owned by the user, and all keys accessible
to groups to which that user belongs. In addition, a group of users can have an authorization policy
assigned to it, which restricts the use of the keys accessible by that group to certain time periods or
certain operations per hour.
Using the Management Console
184
