Configuring the cluster, Clustering overview – HP Secure Key Manager User Manual
Page 191
Description
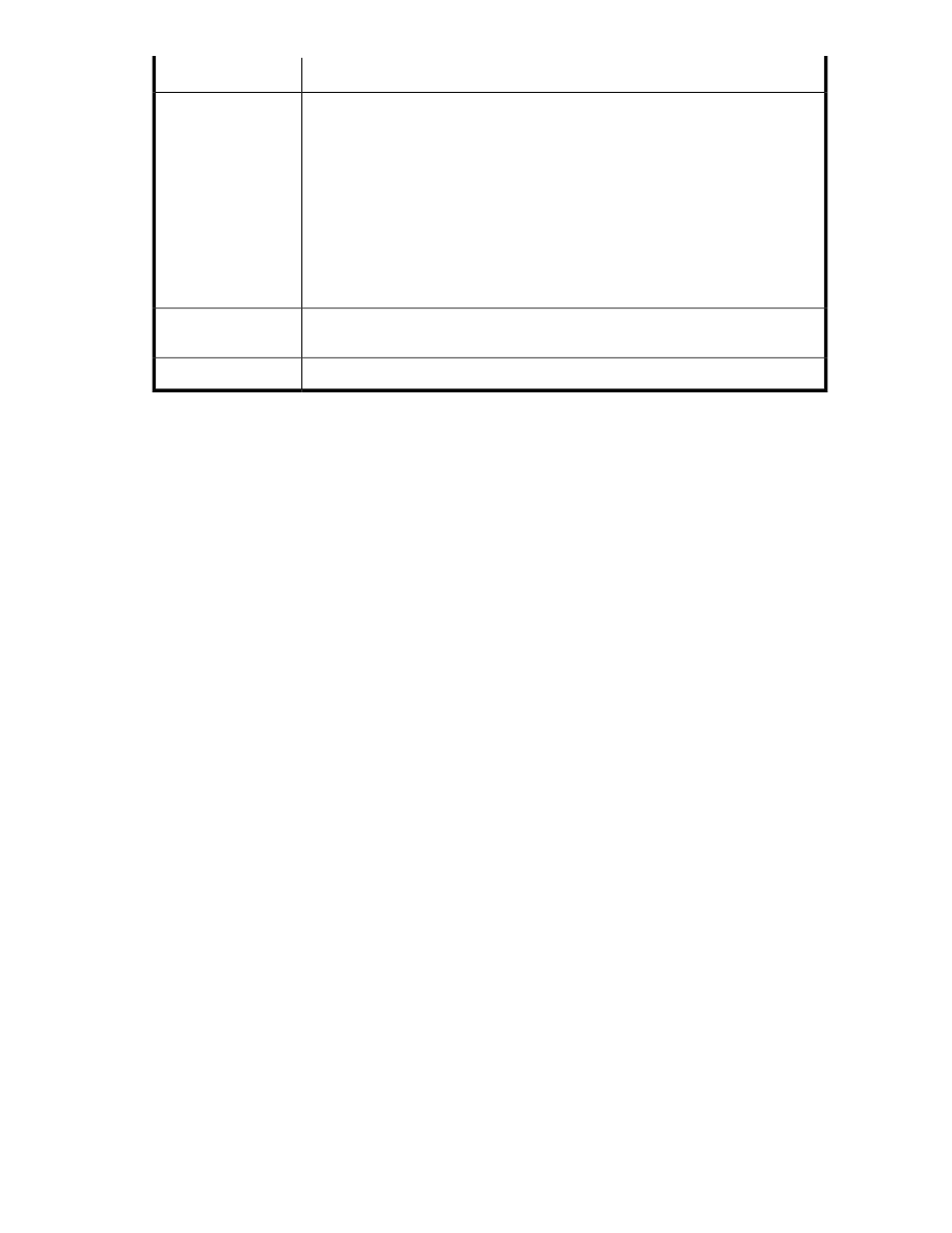
Component
In this field you specify the IP address on which you want to listen for health check
requests. You can specify an individual IP address bound to the SKM or you can
specify All.
IMPORTANT:
We strongly recommend that you limit the Health Check feature to a specific IP
address. If you have four IP addresses bound to the SKM, and you enable the
Health Check feature for all IP addresses, then the SKM listens for health check
requests on four different IP addresses; whereas, if you specify a single IP
address, the SKM listens for health check requests on only one IP address. This
can greatly reduce system vulnerability to outside attacks.
Local IP
In this field you specify the port on which you want the SKM to listen for health check
requests. The default value for this setting is 9080.
Local Port
Click Edit to modify the health check settings.
Edit
Configuring the cluster
Clustering enables multiple SKMs in a distributed environment to synchronize and replicate configuration
information, thus reducing administration overhead. This chapter contains the following information:
• Clustering Overview
• Cluster Configuration Page
• Clustering Procedures
Clustering overview
A cluster enables multiple KMS Servers to share configuration settings. Any changes made to these
values on one cluster member are replicated to all members within the same cluster. This enables you
to immediately share configuration changes with other KMS Servers.
When a configuration operation is performed on one cluster member, the cluster feature determines
if the operation should be replicated throughout the cluster. If so, the KMS Server immediately sends
a similar operation request to every other member using the cluster port.
If the replication succeeds for a device, the operation is recorded in the System Log. If the replication
fails, the server waits 30 seconds and tries again. If three consecutive replications fail, the server
records the failure in the System Log and sends an SNMP trap indicating that the cluster is out of sync.
Once a device is out of sync, an administrator must synchronize it manually.
The following configuration settings are replicated within a cluster:
•
Keys
•
Local Users & Groups
•
KMS Server
•
NTP
•
DNS
•
SNMP
•
Log Signing Certificate
•
Local Certificate Authorities (CAs)
•
Authorization Policies
Secure Key Manager
191
