User account lockout settings, Viewing the user account lockout settings section, User account lockout settings section components – HP Secure Key Manager User Manual
Page 189
Description
Component
This field allows you to select a profile to use to verify that client certificates are signed
by a CA trusted by the SKM. This option is only valid if you require clients to provide
a certificate to authenticate to the KMS Server. For more information, see
Certificate Authority List Profiles
. As delivered, the default Trusted CA List profile
contains no CAs. You must either add CAs to the default profile or create a new
profile and populate it with at least one trusted CA before the KMS Server can authen-
ticate client certificates.
Trusted CA List Profile
This option allows you to specify the certificate field from which the username is de-
rived. The username can be derived from the UID (user ID), CN (Common Name),
SN (Surname), E (Email address), E_ND (Email without domain), or OU (Organiza-
tional Unit) field. When you select the E_ND option, the KMS Server matches against
the data to the left of the @ symbol in the E-mail address in the certificate request. For
example, if the certificate request contains the E-mail address [email protected],
then the KMS Server matches against User1.
Username Field in Cli-
ent Certificate
When this option is enabled, the KMS Server expects that the client certificate
presented by the client application has an IP address in the subjectAltName field. The
KMS Server obtains the IP address from the subjectAltName and compares that to
the source IP address of the client application; if the two IP addresses match, the KMS
Server authenticates the user. If the two IP addresses do not match, the KMS Server
closes the connection with the client.
Require Client Certific-
ate to Contain Source
IP
Click Edit to modify the KMS Server authentication settings.
Edit
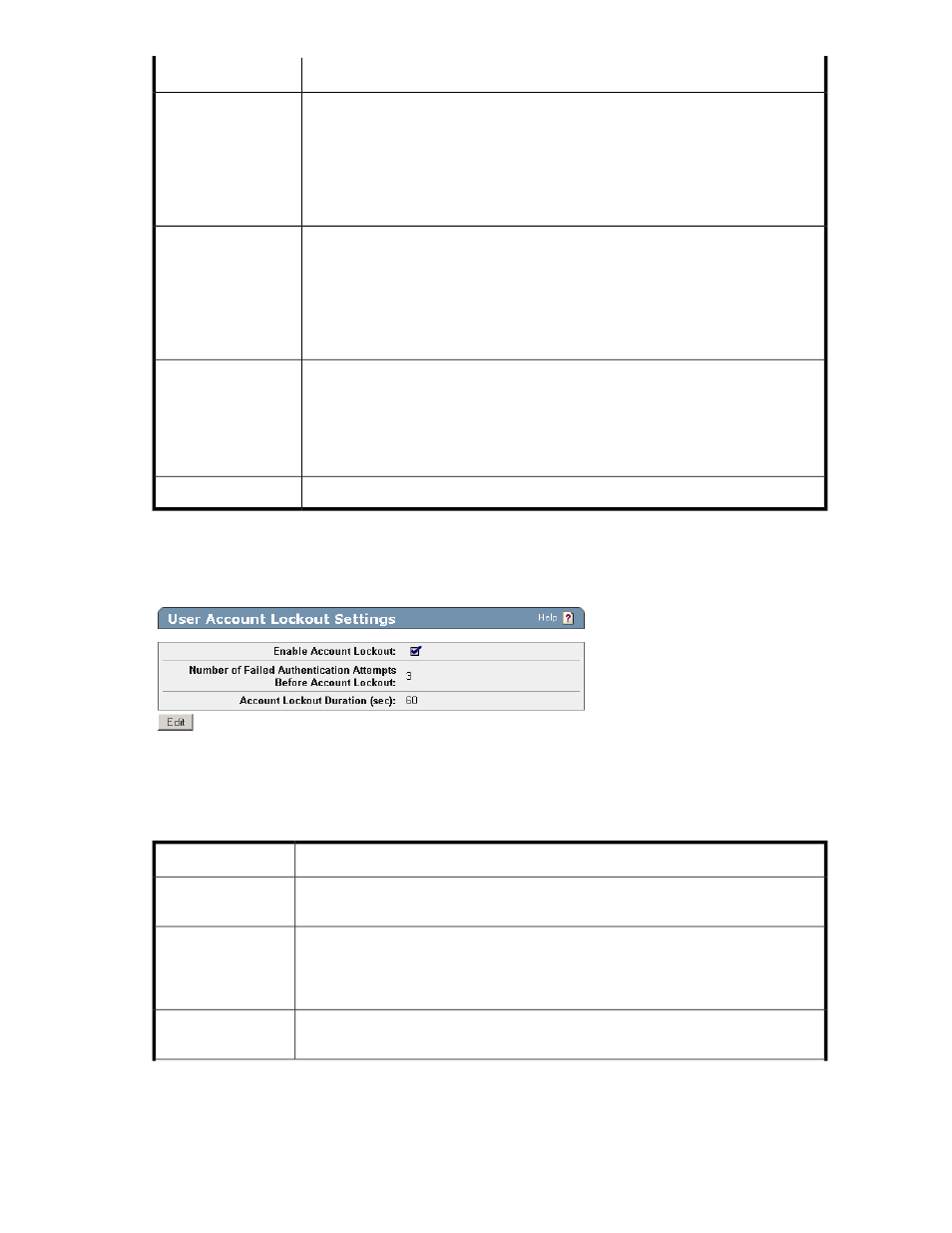
User Account Lockout Settings
Use the User Account Lockout Settings section to manage an account lockout policy.
Figure 102 Viewing the User Account Lockout Settings section
The following table describes the components of the User Account Lockout Settings section.
Table 83 User Account Lockout Settings section components
Description
Component
Indicates if the feature is enabled. When not enabled, users can make unlimited attempts
to log in to an account.
Enable Account
Lockout
The number of failed login attempts permitted before the system temporarily forbids
access to the account. After the last failed authentication attempt, the system ignores
any subsequent login requests until the end of the account lockout duration, at which
time the counter is reset.
Number of Failed
Authentication At-
tempts Before Ac-
count Lockout
The period of time during which the account is not available.
Account Lockout Dur-
ation (sec)
Secure Key Manager
189
