Ssl cipher order, Viewing the ssl cipher order section, Ssl cipher order section components – HP Secure Key Manager User Manual
Page 183
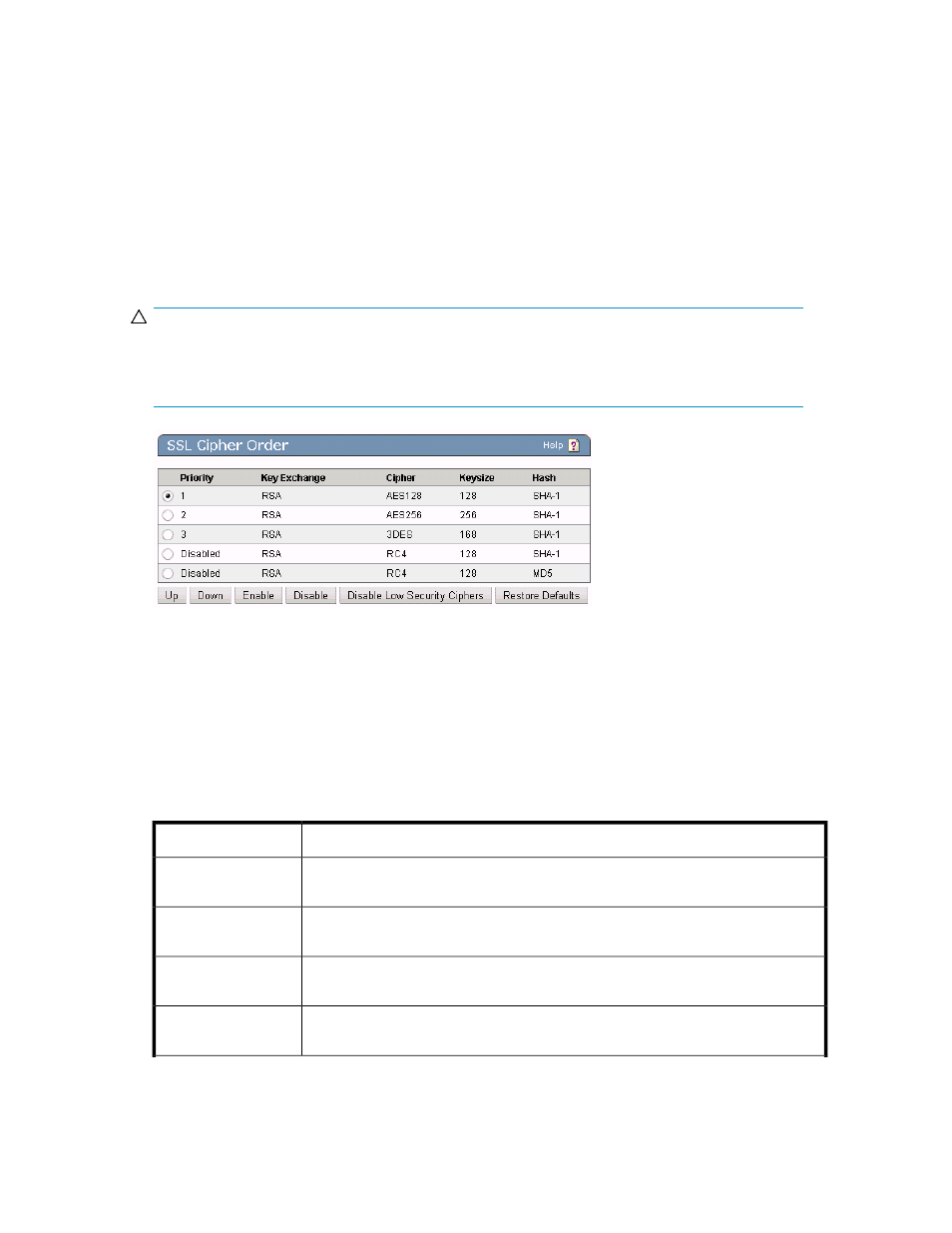
SSL Cipher Order
Use this section to enable, disable, and order the priority of SSL ciphers.
Different applications and databases support different encryption algorithms for securing SSL sessions.
The SKM supports many SSL ciphers and consequently can communicate securely using all common
ciphers.
Please note that the SSL Cipher Order pertains to the communication channel between the client
(application, database, etc.) and the SKM. It does not affect the keys that might be used to encrypt
data by the KMS Server. When an application or database presents the SKM with a list of supported
ciphers, the SKM chooses the supported cipher that is highest on its priority list.
CAUTION:
Exercise caution when modifying the SSL Cipher Order. Unless you are familiar with SSL Ciphers,
you should not rearrange the Cipher Order list. Changes to the list may affect both performance and
security. Click Restore Defaults to reset the list to the original settings.
Figure 99 Viewing the SSL Cipher Order section
The following table describes the components of the SSL Cipher Order section.
Table 80 SSL Cipher Order section components
Description
Component
You can arrange the SSL Cipher order using the Up and Down buttons. One (1) is
the highest priority, and ten (10) is a low priority.
Priority
This field specifies the algorithm to use for encryption and authentication. Supported
algorithms: RSA and RSA Low Security.
Key Exchange
This field specifies the symmetric cipher to use to encrypt SSL sessions. Supported
ciphers: AES, DES, 3DES, RC2, and RC4.
Cipher
This field specifies the number of bits of the session key size. Supported key sizes
vary for each cipher.
Keysize
Secure Key Manager
183
