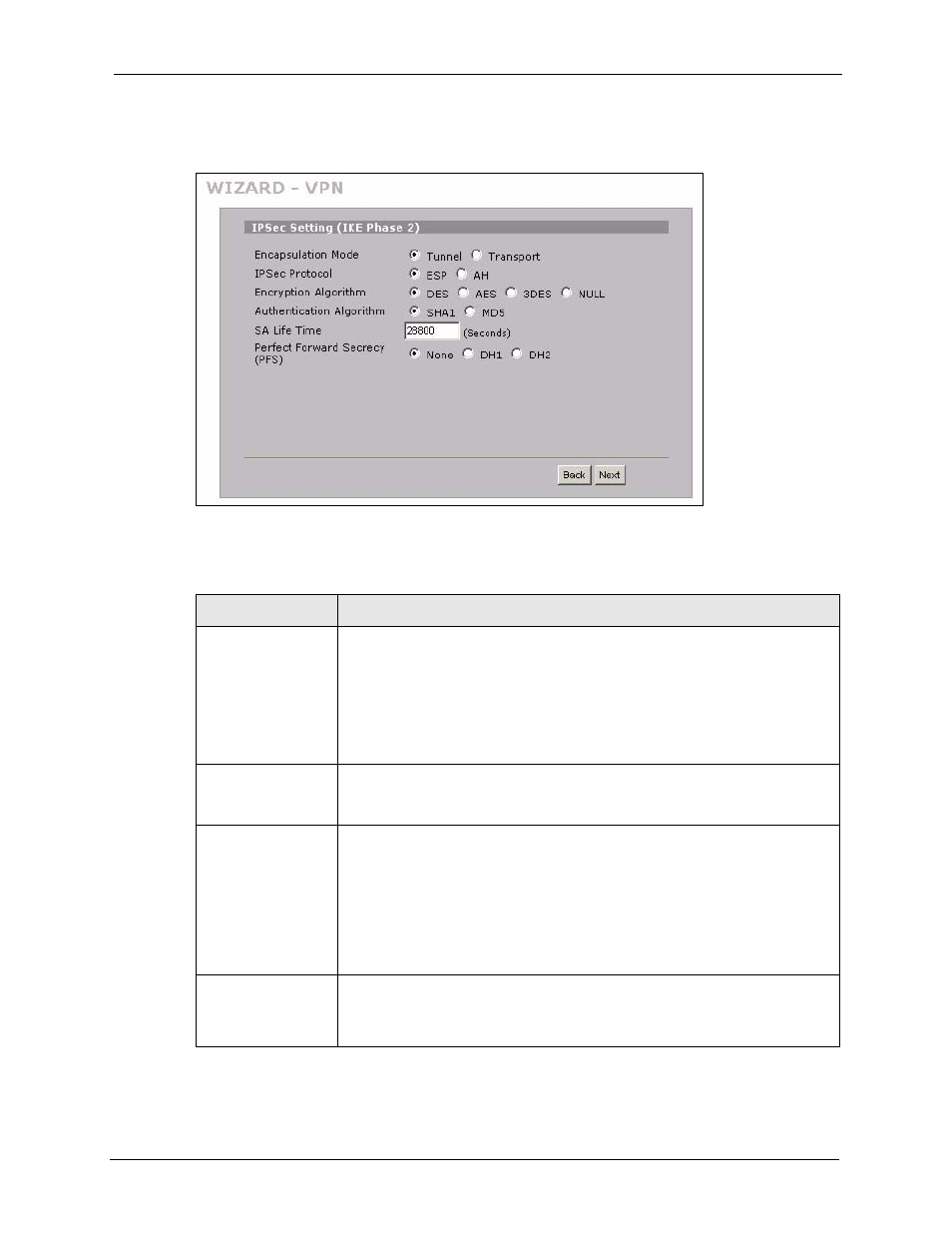
6 vpn wizard ipsec setting (ike phase 2), Figure 29 vpn wizard: ipsec setting, Table 18 vpn wizard: ipsec setting – ZyXEL Communications 70 Series User Manual
Page 98
ZyWALL 5/35/70 Series User’s Guide
Chapter 3 Wizard Setup
98
3.6 VPN Wizard IPSec Setting (IKE Phase 2)
Figure 29 VPN Wizard: IPSec Setting
The following table describes the labels in this screen.
Table 18 VPN Wizard: IPSec Setting
LABEL
DESCRIPTION
Encapsulation Mode Tunnel is compatible with NAT, Transport is not.
Tunnel mode encapsulates the entire IP packet to transmit it securely. A Tunnel
mode is required for gateway services to provide access to internal systems.
Tunnel mode is fundamentally an IP tunnel with authentication and encryption.
Transport mode is used to protect upper layer protocols and only affects the
data in the IP packet. In Transport mode, the IP packet contains the security
protocol (AH or ESP) located after the original IP header and options, but before
any upper layer protocols contained in the packet (such as TCP and UDP).
IPSec Protocol
Select the security protocols used for an SA.
Both AH and ESP increase ZyWALL processing requirements and
communications latency (delay).
Encryption Algorithm When DES is used for data communications, both sender and receiver must
know the same secret key, which can be used to encrypt and decrypt the
message or to generate and verify a message authentication code. The DES
encryption algorithm uses a 56-bit key. Triple DES (3DES) is a variation on DES
that uses a 168-bit key. As a result, 3DES is more secure than DES. It also
requires more processing power, resulting in increased latency and decreased
throughput. This implementation of AES uses a 128-bit key. AES is faster than
3DES. Select NULL to set up a tunnel without encryption. When you select
NULL, you do not enter an encryption key.
Authentication
Algorithm
MD5 (Message Digest 5) and SHA1 (Secure Hash Algorithm) are hash
algorithms used to authenticate packet data. The SHA1 algorithm is generally
considered stronger than MD5, but is slower. Select MD5 for minimal security
and SHA-1 for maximum security.
