Acl configuration example, Network requirements, Configuration procedure – H3C Technologies H3C SecBlade NetStream Cards User Manual
Page 152
137
ACL configuration example
IPv4 packet filtering and NetStream logging configuration
example
Network requirements
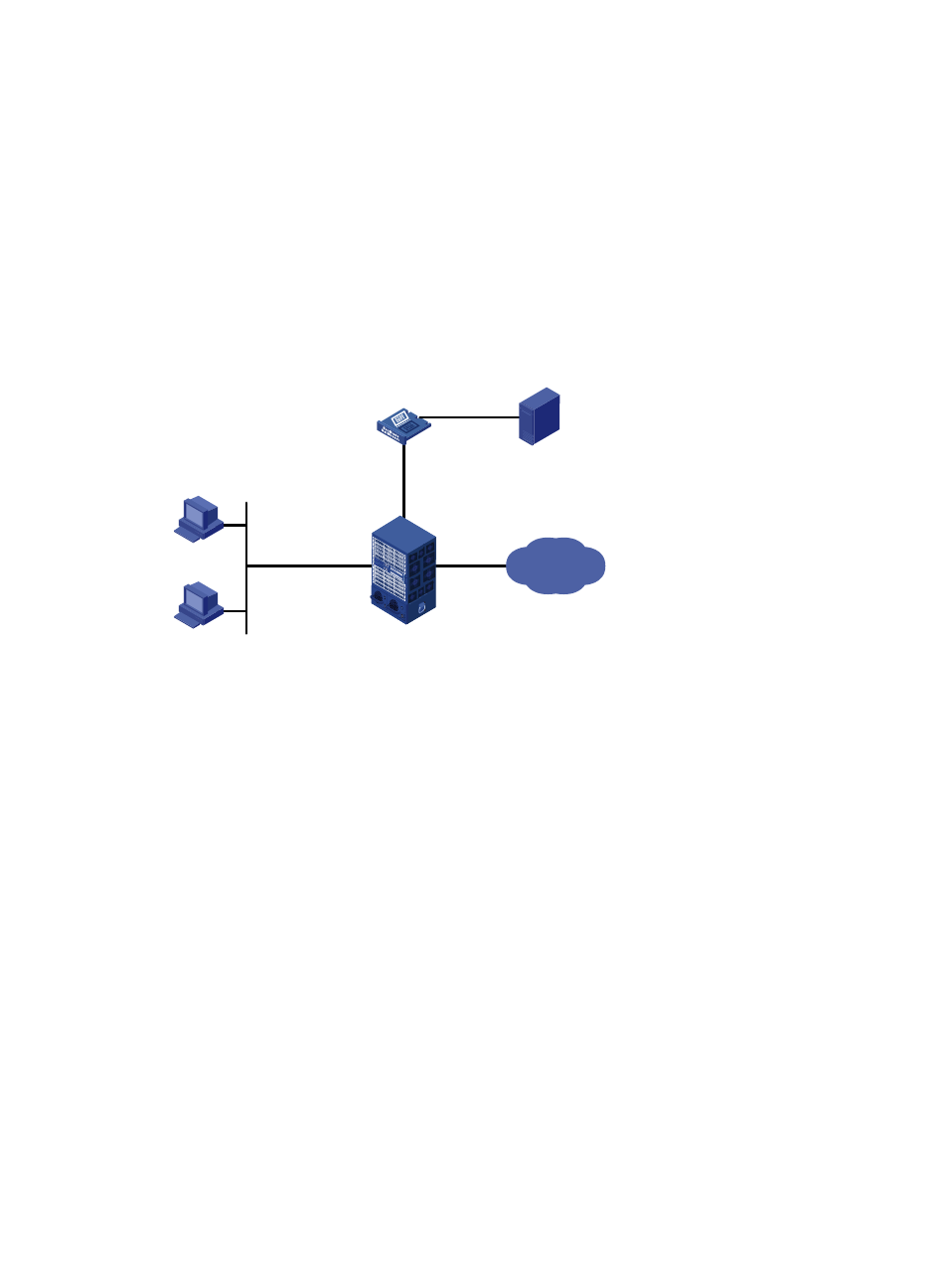
Apply an IPv4 ACL to deny the traffic from Host A on GigabitEthernet 1/0/1 of Device, and copy the
traffic to the SecBlade NetStream card on the device. Enable the packet filtering logging function on the
card, and configure the card to output IPv4 packet filtering logs to the console at 30-second intervals.
Figure 45 IPv4 packet filtering and NetStream logging scenario
Configuration procedure
1.
Configure Device
# Create IPv4 ACL 2009, and configure a rule in the ACL to deny packets sourced from Host A.
[Device] acl number 2009
[Device-acl-basic-2009] rule deny source 192.168.1.2 0
[Device-acl-basic-2009] quit
# Create VLAN 101 and VLAN 102.
[Device] vlan 101 to 102
# Assign GigabitEthernet 1/0/1 to VLAN 101. Apply ACL 2009 to filter incoming packets on
GigabitEthernet 1/0/1, and copy the matching packets to the SecBlade NetStream card in slot 2.
[Device] interface GigabitEthernet1/0/1
[Device-GigabitEthernet1/0/1] port access vlan 101
[Device-GigabitEthernet1/0/1] packet-filter 2009 inbound logging-slot 2
[Device-GigabitEthernet1/0/1] quit
# Assign GigabitEthernet 1/0/2 to VLAN 102.
[Device] interface GigabitEthernet1/0/2
[Device-GigabitEthernet1/0/2] port access vlan 102
[Device-GigabitEthernet1/0/1] quit
IP network
GE1/0/1
Host A
192.168.1.2/24
Device
Host B
192.168.1.3/24
NSC
XGE0/0
XGE2/0/1
SecBlade
GE1/0/2
