Deleting operation logs, Backing up operation logs, Attack logs – H3C Technologies H3C SecBlade IPS Cards User Manual
Page 98: Attack logs overview
13-8
Deleting Operation Logs
Select Log Management > Operation Logs > Delete Logs to enter the page for deleting operation
logs, as shown in
.
Figure 13-7 Delete operation logs
Select the checkbox before the operation log files to be deleted, and then click Delete to delete the
corresponding operation log files.
.
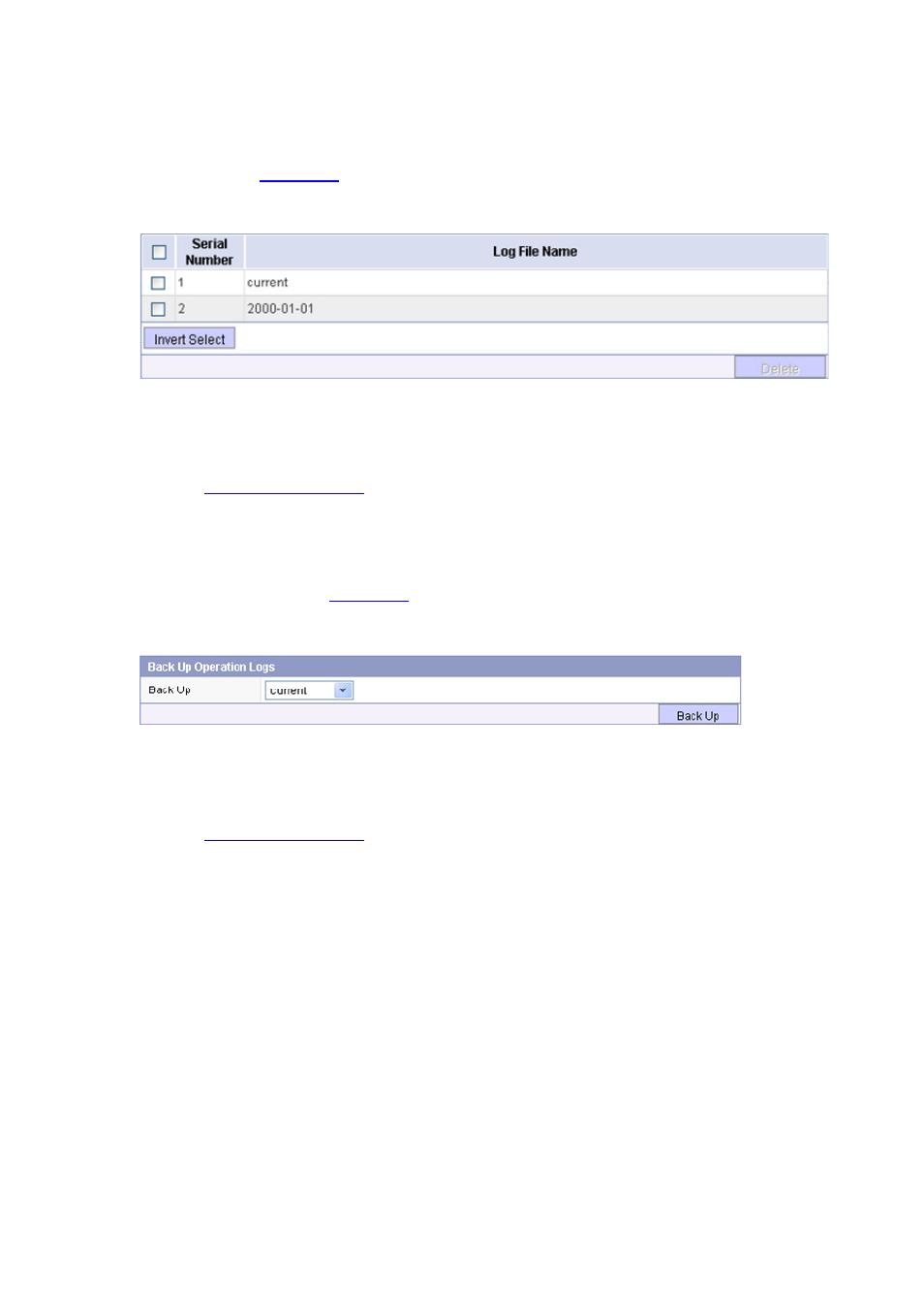
Backing Up Operation Logs
Select Log Management > Operation Logs > Back up Logs to enter the page for backing up
operation logs, as shown in
Figure 13-8 Back up operation logs
Select the operation log files to be backed up, and then click Back Up to back up the operation log files
to the local host in the format of CSV.
.
Attack Logs
Attack Logs Overview
The system analyzes and archives the attack events occurred during device running to generate attack
logs and saves them in the database. Attack logs enable you to monitor the device running status and
diagnose network device faults.
The functions provided by the attack logs module are listed in the following table:
