Querying attack logs – H3C Technologies H3C SecBlade IPS Cards User Manual
Page 100
13-10
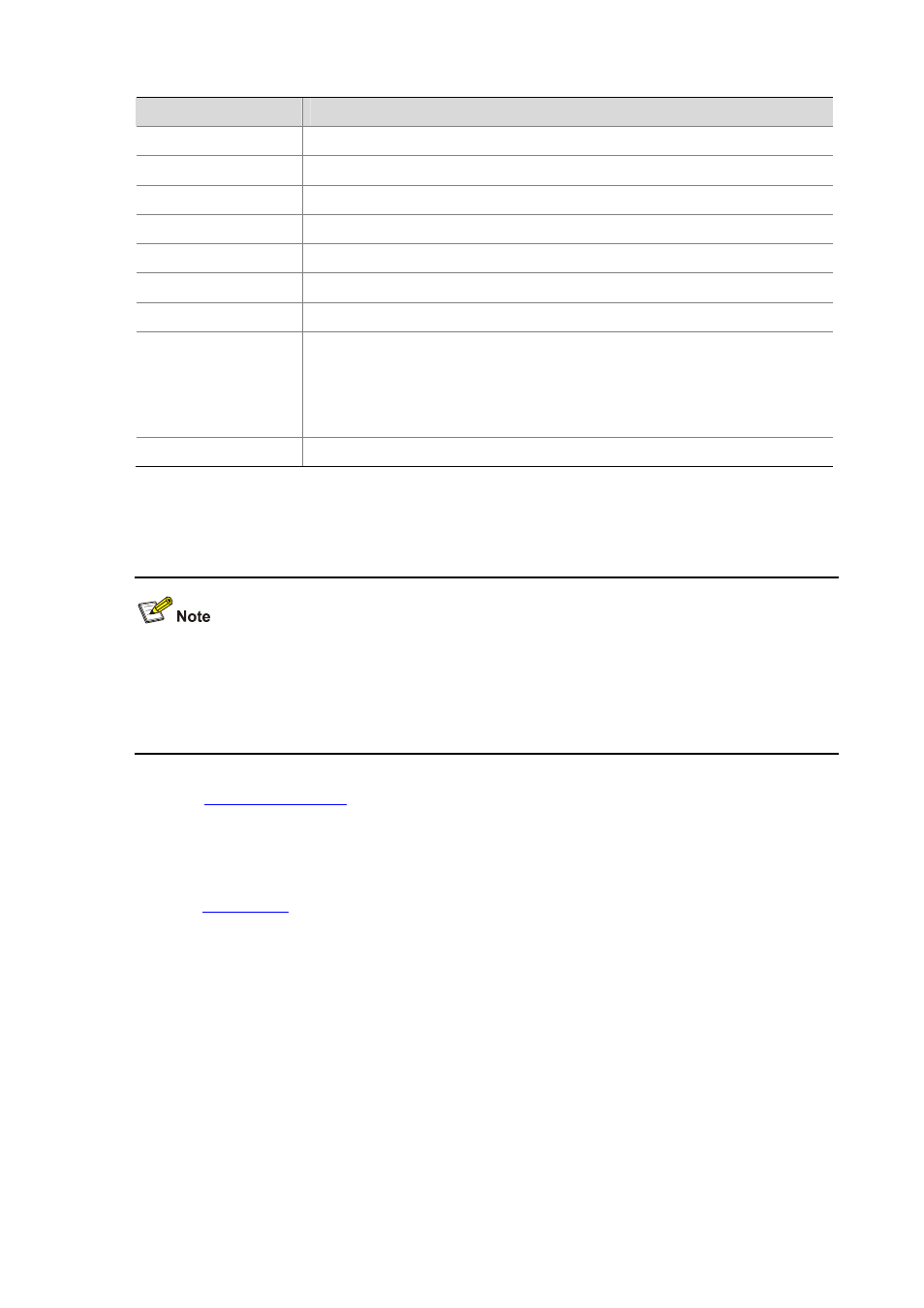
Item
Description
Direction
Direction of the attack: from inside to outside or from outside to inside.
Src ID
The source IP address of an attack
Dest IP
The destination IP address of an attack
Src Port
The source port of an attack
Dest Port
The destination port of an attack
App Layer
The application layer protocol corresponding to an attack
Hit Count
Count of times that the attack is detected.
Severity
Severity level of an attack, including the following:
z
Emergency: The system is unavailable.
z
Alert: Information that demands prompt reaction
z
Warning: Warnings
z
Informational: Informational information
Packet Trace
Packet Trace file name generated (with the download file link)
Click Export to CSV, and a popup window appears. You can display the log contents in the format of
CSV, or save them in the format of CSV locally.
z
Select the Refresh every seconds checkbox, and the system will automatically refresh the logs in
the specified interval; click the Refresh Now button, and you can refresh the latest logs manually.
z
To display the logs in the order defined by the title items, click the title items in the log information
table.
.
Querying Attack Logs
Select Log Management > Attack Logs > Query Logs to enter the page for querying attack logs, as
shown in
. The page allows you to query attack logs based on different conditions.
