17 ddos protection configuration, Overview, Introduction to ddos – H3C Technologies H3C SecBlade IPS Cards User Manual
Page 158: Ddos protection configuration
17-1
17
DDoS Protection Configuration
Overview
Introduction to DDoS
A Denial of Service (DoS) attack is an attempt to make the target system or network unable to provide
normal services. DoS attacks are implemented by either consuming the bandwidth/system resources of
the attacked target or making the target fail to respond to abnormities by exploiting the vulnerabilities of
its programs.
A Distributed Denial of Service (DDoS) attack is mounted by multiple hosts to a target. Because the
attacking host does not attack the target directly, it cannot be detected or tracked, and thus its identity is
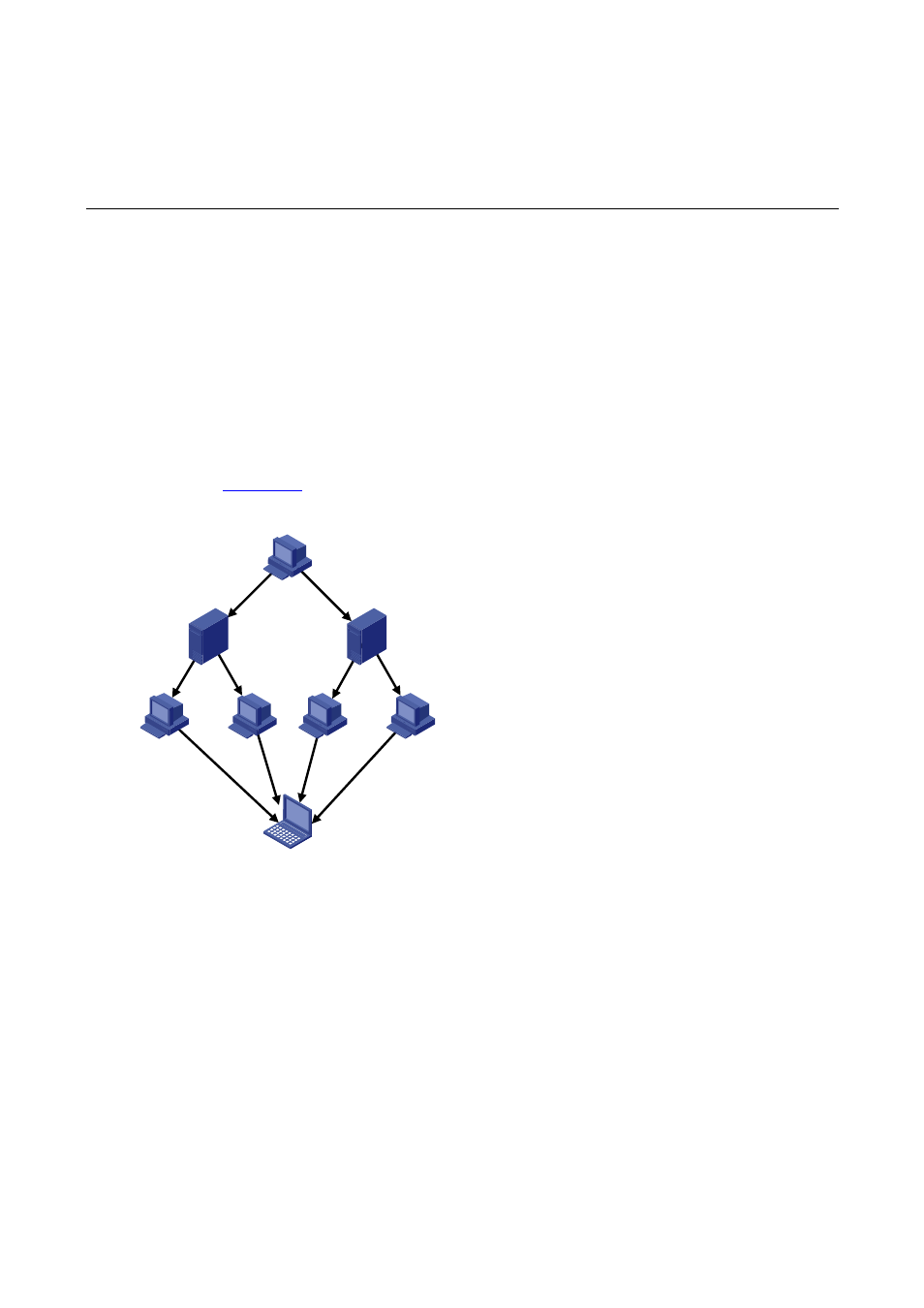
shows a DDoS attack.
Figure 17-1 DDoS attack network diagram
Attacker
Handler
Attacked host
Agent
Handler
Agent
Agent
Agent
z
Attacker: It sends attack commands to handlers.
z
Handler: Handlers are compromised and controlled by the attacker, and they also control many
agents. A handler has specific programs installed to receive commands from the attacker and send
such commands to agents.
z
Agent: Agents are comprised by the attacker through the handlers. They run attacking programs,
and receive and execute commands from handlers to attack a target.
The DDoS protection feature enables a device to detect and take countermeasures against DDoS
attacks. Specifically, the feature can:
z
Detect external worm attacks and reduce the impact;
z
Detect and stop DDoS attacks made by using DDoS tools;
z
Detect and stop DDoS attacks made via zombie networks;
z
Detect Challenge Collapsar (CC) attacks and reduce the impact.
