Terminology of ddos protection, Ddos policy and learning rule, Detection rule – H3C Technologies H3C SecBlade IPS Cards User Manual
Page 159: Filtering rule, Implementation of ddos protection, Implementation of ddos protection -2
17-2
Terminology of DDoS Protection
DDoS Policy and Learning Rule
A DDoS policy defines a set of DDoS learning rules, which specify the attacks to be detected and the
minimum attack thresholds.
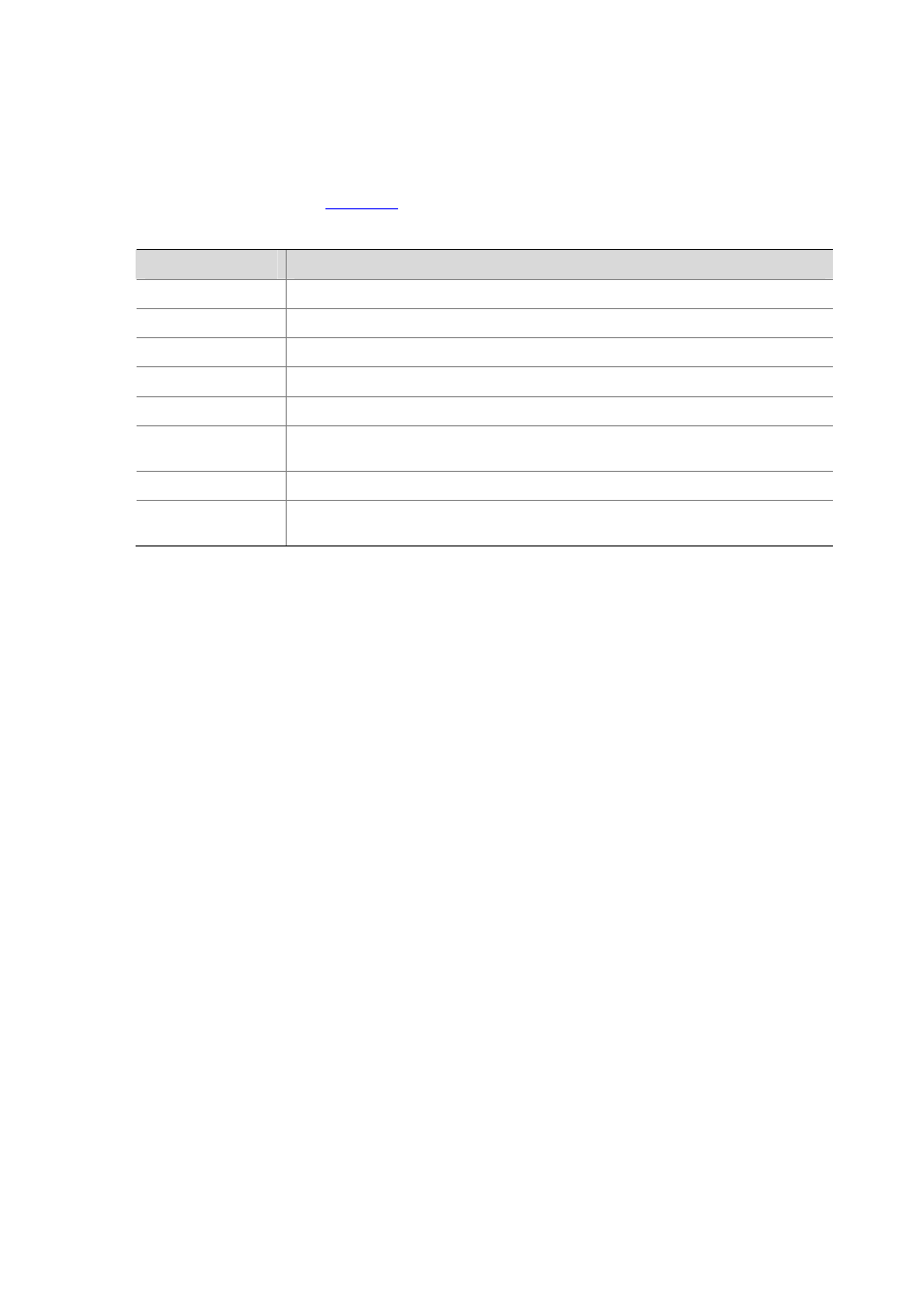
shows the categories of attacks that can be specified.
Table 17-1 Categories of attacks
Category
Description Attacks
TCP flood
SYN flood, ACK flood, FIN flood, RST flood, connect flood, empty connect flood.
HTTP flood
HTTP get/put flood, malicious URL, zombie
Port/host scan
Port scan, host scan
DNS flood
DNS request flood, DNS response flood
UDP flood
UDP flood
IP flood
Flood attacks of IP based protocols other than TCP and UDP, including IP flood and
ICMP flood
Worm Worm
Unknown DDoS
Flood attacks of specific flows, which are detected based on the IPS signature
database
Detection Rule
After learning normal traffic according to the learning rule, the system generates a detection rule, which
describes the characteristics of normal traffic and defines the action to be taken on abnormal traffic. A
detection rule involves parameters such as attack name, threshold type, level, threshold and protected
IP..
You can modify some parameters of a detection rule, and enable/disable the detection rule. You can
also select to automatically enable a detection rule after it is generated or manually start it.
Filtering Rule
Upon detection of abnormal traffic, the system generates a filtering rule, which defines the action (such
as source authentication, drop, or notify) to be taken on subsequent traffic with the same characteristics
as the detected abnormal traffic.
Filtering rules are either static or dynamic. Dynamic filtering rules are preferable.
z
Static filtering rule: It is configured by the user or predefined by the system.
z
Dynamic filtering rule: It is dynamically generated upon detection of abnormal traffic.
Implementation of DDoS Protection
The implementation of DDoS protection involves three phases.
1) Using the learning rules of the DDoS policy configured on the segment to create the normal traffic
model and then generating detection rules.
