Applying a ddos policy on a segment, Applying a ddos policy on a segment -8 – H3C Technologies H3C SecBlade IPS Cards User Manual
Page 165
17-8
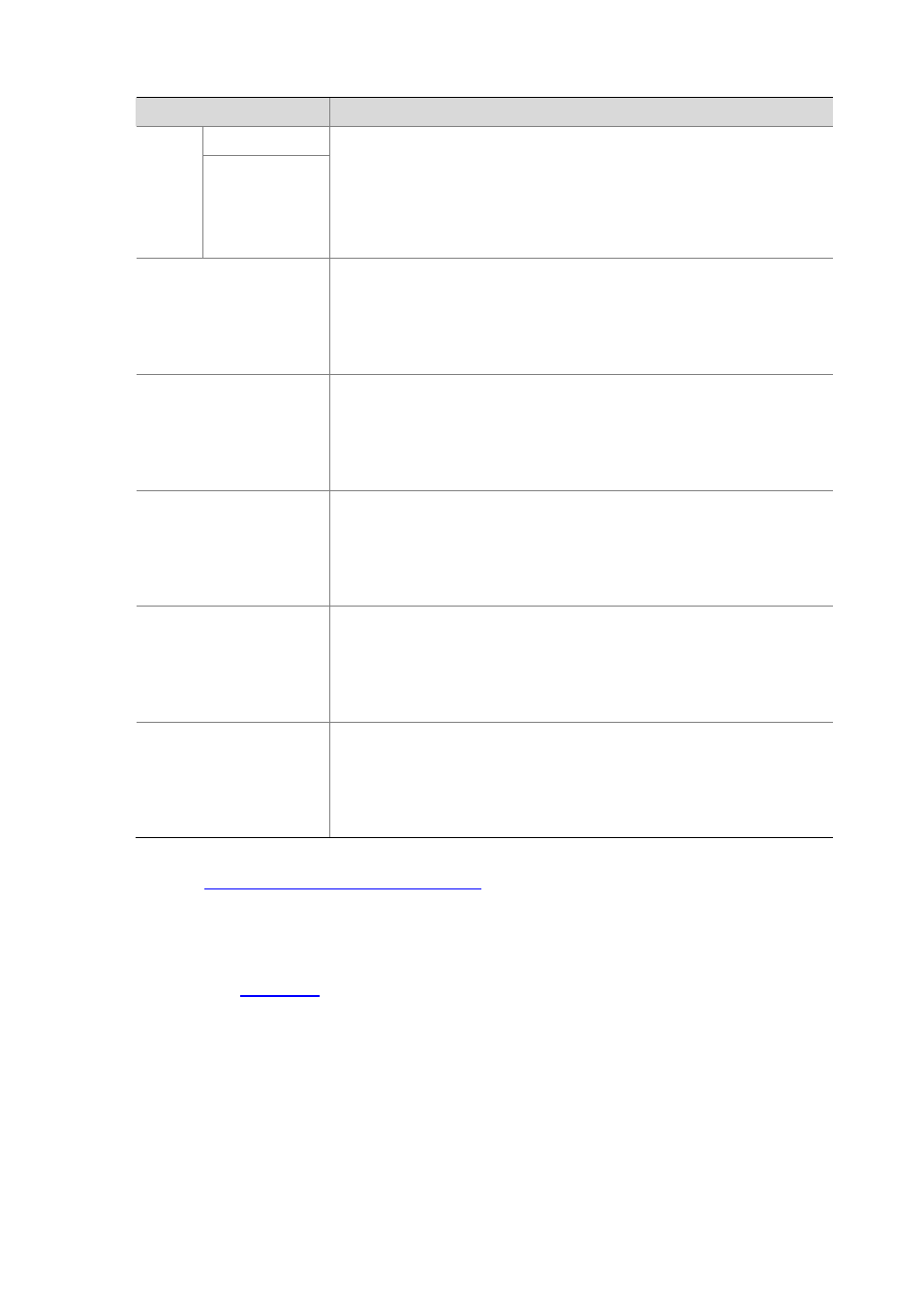
Item
Description
Port Scan
Port/Ho
st
Host Scan
Select the checkbox before Port/Host to enable detection of port/host scan
attacks and configure the minimum thresholds for specific port/host scan
attacks.
If you start traffic learning after above configuration, the system will generate
detection rules for port/host scan attacks. If the threshold for a specific attack in
a detection rule is lower than that in the corresponding learning rule, the latter
threshold will be used to detect that attack.
DNS Flood
Select the checkbox before DNS Flood to enable detection of DNS flood attacks
and configure the minimum thresholds for specific DNS flood attacks.
If you start traffic learning after above configuration, the system will generate
detection rules for DNS flood attacks. If the threshold for a specific attack in a
detection rule is lower than that in the corresponding learning rule, the latter
threshold will be used to detect that attack.
UDP Flood
Select the checkbox before UDP Flood to enable detection of UDP flood attacks
and configure the minimum thresholds for specific UDP flood attacks.
If you start traffic learning after above configuration, the system will generate
detection rules for UDP flood attacks. If the threshold for a specific attack in a
detection rule is lower than that in the corresponding learning rule, the latter
threshold will be used to detect that attack.
IP Flood
Select the checkbox before IP Flood to enable detection of IP flood attacks and
configure the minimum thresholds for specific IP flood attacks.
If you start traffic learning after above configuration, the system will generate
detection rules for IP flood attacks. If the threshold for a specific attack in a
detection rule is lower than that in the corresponding learning rule, the latter
threshold will be used to detect that attack.
Unknown DDoS
Select the checkbox before Unknown DDoS to enable detection of unknown
DDoS attacks and configure the minimum thresholds.
If you start traffic learning after above configuration, the system will generate
detection rules for unknown DDoS attacks. If the threshold for a specific attack
in a detection rule is lower than that in the corresponding learning rule, the latter
threshold will be used to detect that attack.
Worm
Select the checkbox before Worm to enable detection of Worm attacks and
configure the minimum thresholds for specific Worm attacks.
If you start traffic learning after above configuration, the system will generate
detection rules for Worm attacks. If the threshold for a specific attack in a
detection rule is lower than that in the corresponding learning rule, the latter
threshold will be used to detect that attack.
DDoS Protection Configuration Task List
.
Applying a DDoS Policy on a Segment
Select DDoS > Segment Policies from the navigation tree to enter the DDoS policy application list
. Click Add to enter the page for applying a DDoS policy on a segment, and
click Advanced Configuration on the page to configure advanced parameters.
