Figure 17-5 – H3C Technologies H3C SecBlade IPS Cards User Manual
Page 164
17-7
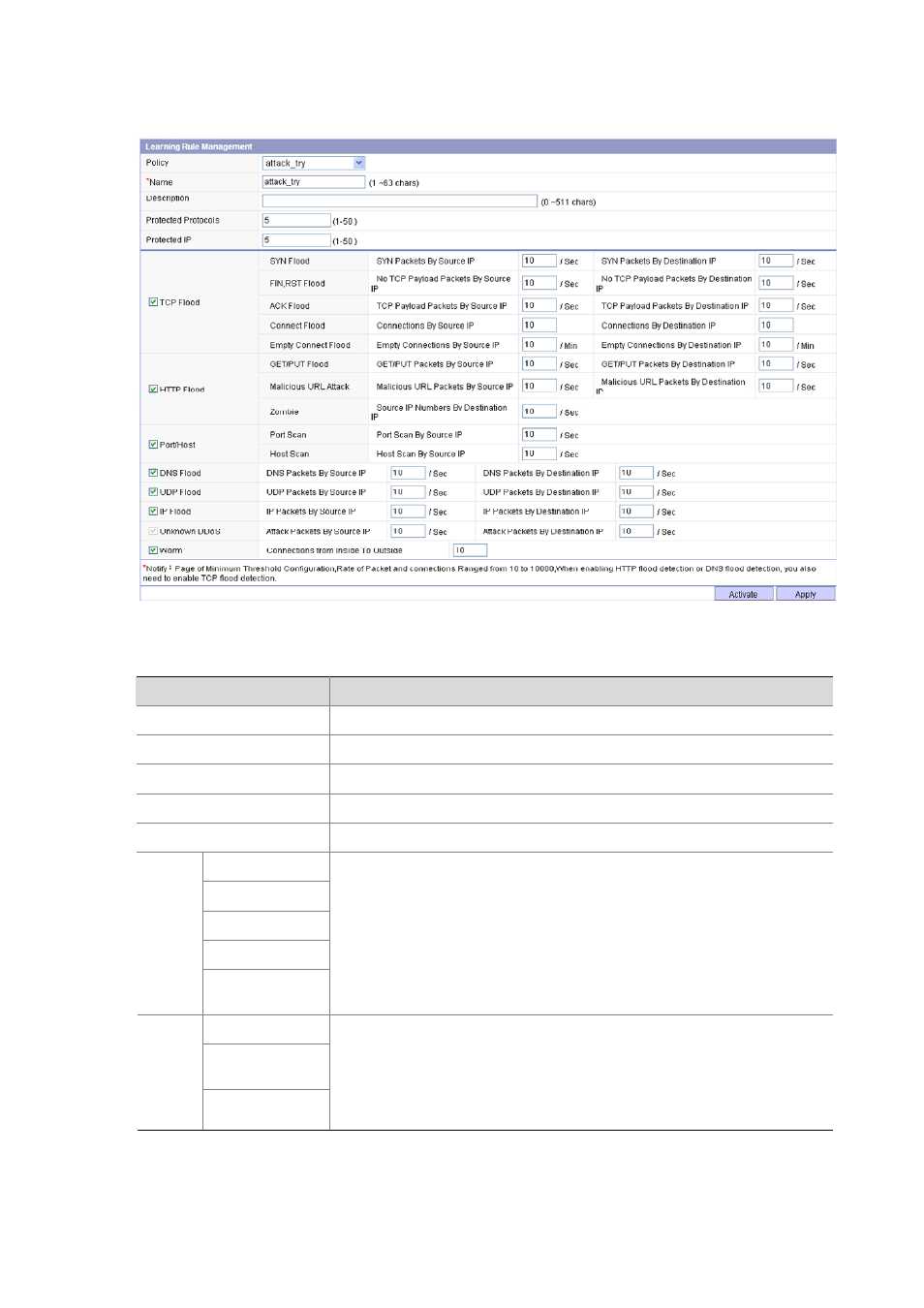
Figure 17-5 Learning rule management page of a user-defined DDoS policy
Table 17-4 Configuration items on the learning rule management page
Item
Description
Policy
Select a DDoS policy to view or modify its learning rules
Name Configure
the
name
of the DDoS policy
Description
Configure a description for the DDoS policy
Protected protocols
Maximum number of protocols to be protected
Protected IP
Maximum number of IP addresses to be protected
SYN Flood
FIN,RST Flood
ACK Flood
Connect Flood
TCP
Flood
Empty Connect
Flood
Select the checkbox before TCP Flood to enable detection of TCP flood attacks
and configure the minimum thresholds for specific TCP flood attacks.
If you start traffic learning after above configuration, the system will generate
detection rules for TCP flood attacks. If the threshold for a specific attack in a
detection rule is lower than that in the corresponding learning rule, the latter
threshold will be used to detect that attack.
GET,PUT Flood
Malicious URL
attack
HTTP
Flood
Zombie
Select the checkbox before HTTP Flood to enable detection of HTTP flood
attacks and configure the minimum thresholds for specific HTTP flood attacks.
If you start traffic learning after above configuration, the system will generate
detection rules for HTTP flood attacks. If the threshold for a specific attack in a
detection rule is lower than that in the corresponding learning rule, the latter
threshold will be used to detect that attack.
