Epon system security – H3C Technologies H3C S7500E Series Switches User Manual
Page 39
2-6
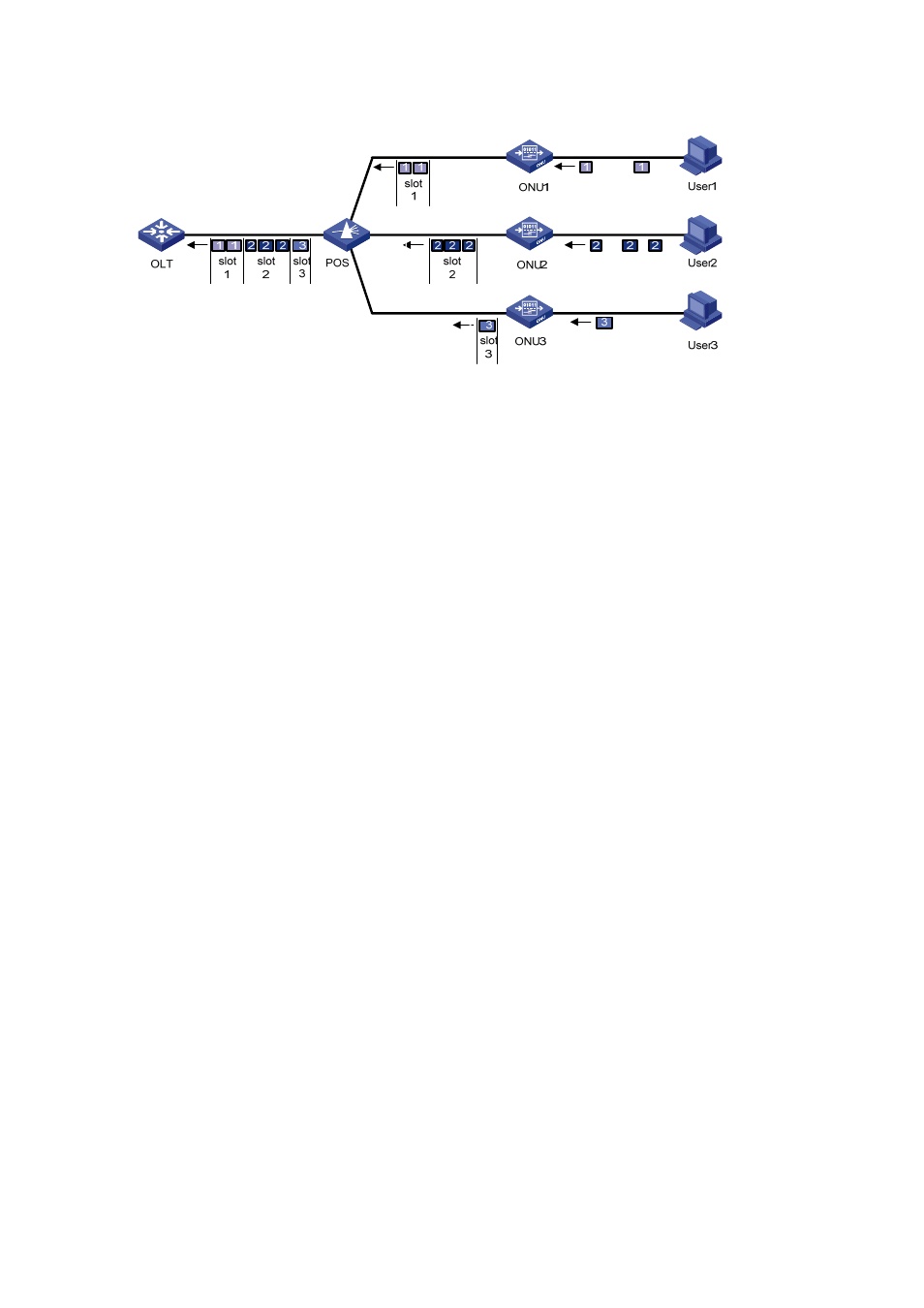
Figure 2-4
Uplink data transmission in an EPON system
The Time Division Multiple Access (TDMA) technology is used to transmit uplink data. This ensures
that one optical fiber between the OLT and the POS can transmit data signals from multiple ONUs to
the OLT without signal interference.
EPON System Security
Downlink data through the OLT is broadcast to each ONU. To prevent illegal interception of user
information, each LLID in an EPON system is assigned a unique key, which is updated periodically:
In a key update process, the OLT sends a new key request message to an ONU. Upon receiving the
new key request message, the ONU sends a new key notification message back to the OLT.
In a key update process, an OLT uses the key update timer and encryption response timer:
1) OLT key update timer
This timer is used to control the key update cycle. When the key update timer expires, the OLT sends
another key request message to start another key update process.
2) OLT encryption response timer
This timer is used to start another key update process when the OLT receives no new key notification
message, thus making the key update more reliable.
Upon sending a key update request message, the OLT starts the encryption response timer:
If the OLT receives a correct new key notification message from an ONU before the timer expires,
the OLT enables the new key and cancels the timer.
If the OLT receives no new key notification message before the timer expires, the OLT considers
the key update process has failed, resets the timer, and sends another key update request
message. Before the key update succeeds, an ONU keeps using the original key and the OLT
reports the key update failure information to the network management system.
If the OLT receives no new key notification message within the encryption response timer duration
after sending three new key request messages consecutively, the OLT sends an alarm to the
network management system and the old key continues to be used for downlink data. In this case,
you are recommended to adjust the value of the encryption response timer.
