HP Secure Key Manager User Manual
Page 289
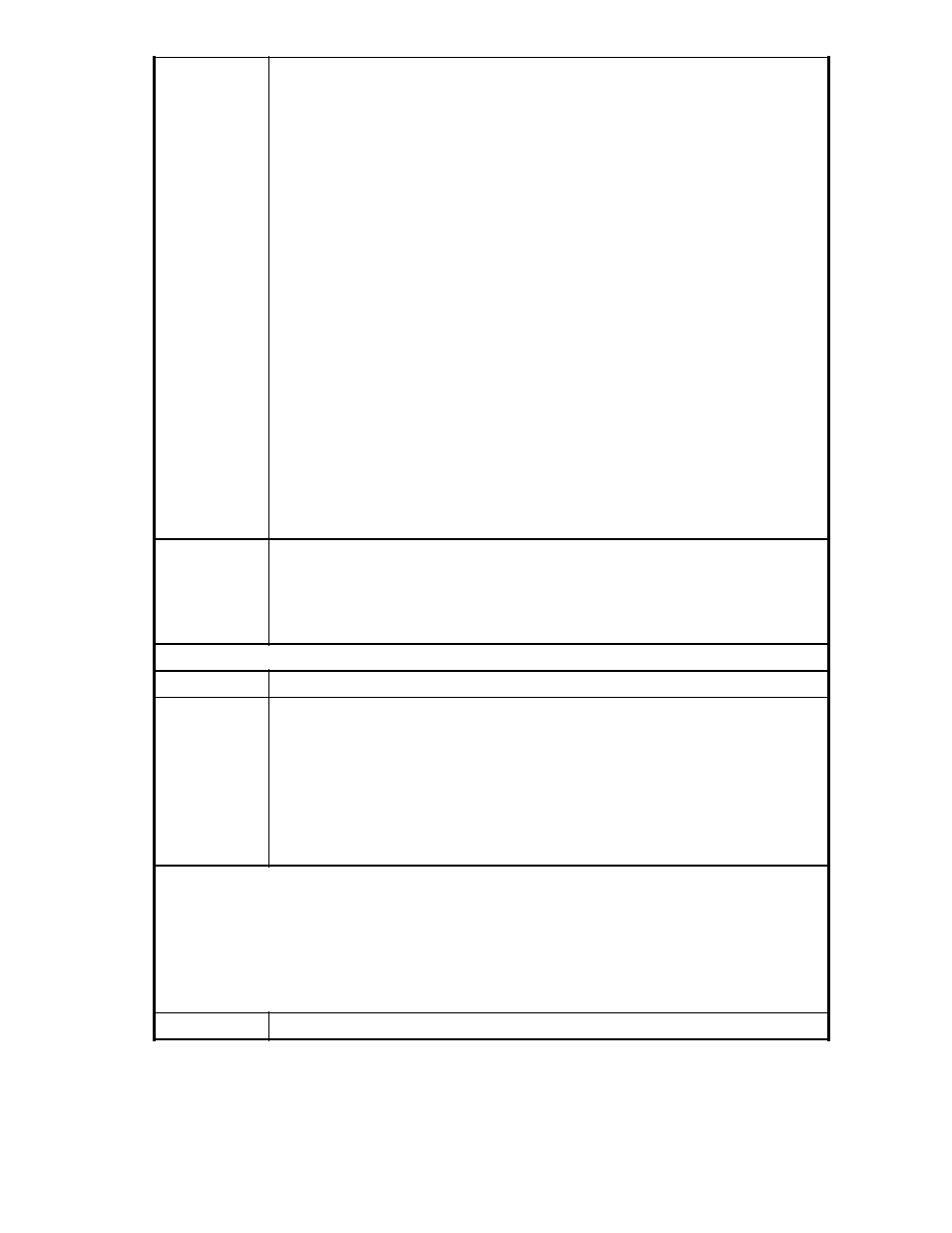
Syntax
hostname (config)# cipherspec priority
CURRENT PRIORITIES
The SSL cipher order is shown below:
Priority Key Exchange Cipher KeysizeHash
1 RSA AES128 128SHA-1
2 RSA AES256 256SHA-1
3 RSA 3DES 168SHA-1
Disabled (1) RSA RC4 128SHA-1
Disabled (2) RSA RC4 128MD5
Disabled (3) RSA Low Security DES 56SHA-1
Disabled (4) RSA Low Security RC4 56SHA-1
Disabled (5) RSA Low Security RC4 56MD5
Disabled (6) RSA Low Security RC2 56MD5
Disabled (7) RSA Low Security DES 40SHA-1
Disabled (8) RSA Low Security RC2 40MD5
Disabled (9) RSA Low Security RC4 40MD5
NEW PRIORITY CONFIGURATION
Please use the current priority from above to reference each
item.
Which item will have priority #1 (1..12):
Which item will have priority #2:
Which item will have priority #3:
Which item will have priority #4:
Cipher Order priorities successfully changed.
Related
command(s)
• show cpiherspec
• cipherspec
• no cipherspec
• no export cipherspec
• restore cipherspec
no cipherspec – disable a cipherspec.
Syntax
hostname (config)# no cipherspec
Related
command(s)
NOTE:
Unless you know the priority of the cipher you want to disable, you can use the show
cipherspec command to display the ciphers on the system.
• show cpiherspec
• cipherspec priority
• cipherspec
• no export cipherspec
• restore cipherspec
no export cipherspec – disable export cipherspecs (128–bit and below).
NOTE:
By executing this command, you are basically mandating that only high security ciphers (128–bit and
above) are used during SSL sessions. Please note that the cipher order pertains to the communication
channel between the client (application, database, etc.) and the SKM. It does not affect the keys that
might be used to encrypt data by the KMS Server.
You can restore the original SSL cipher order by executing the restore cipherspec command.
Syntax
hostname (config)# no export cipherspec
Secure Key Manager
289
