Secure logs, Rotation schedule, 135 viewing the rotation schedule section – HP Secure Key Manager User Manual
Page 224: Log configuration page
Secure logs
The SKM allows you to sign your log files before moving them to another machine or downloading them,
which makes your log files more secure than unsigned log files.
A Log Signing Certificate is created the first time the SKM is run and when the machine is restored to the
factory defaults. If the Sign Log option is selected, a log file is signed with the Log Signing Certificate
right before it is downloaded or moved off of the SKM. The signed log file is then sent to the specified
host in multipart S/MIME E-mail format. The first part of the signed log file contains the clear text
log; the second part of the signed log file contains the signature in PEM encoded PKCS7 format. The
certificate used to verify the signed log file is embedded within the signature, but it is insecure to simply
rely on this embedded certificate for verification.
Signed logs do not appear in plaintext when downloaded.
IMPORTANT:
If you decide to recreate a Log Signing Certificate, it is very important to make a backup of the existing
certificate so that old log files signed with the existing certificate can still be properly verified.
TIP:
You should store your Log Signing Certificate separately from the signed logs files.
Log Configuration page
The Log Configuration page enables you to configure rotation schedules, syslog settings, create signed
logs, and specify log levels. This page contains the following sections:
• Rotation Schedule
• Log Rotation Properties
• Syslog Settings
• Log Signing
• Log Signing Certificate Information
• Activity Log Settings
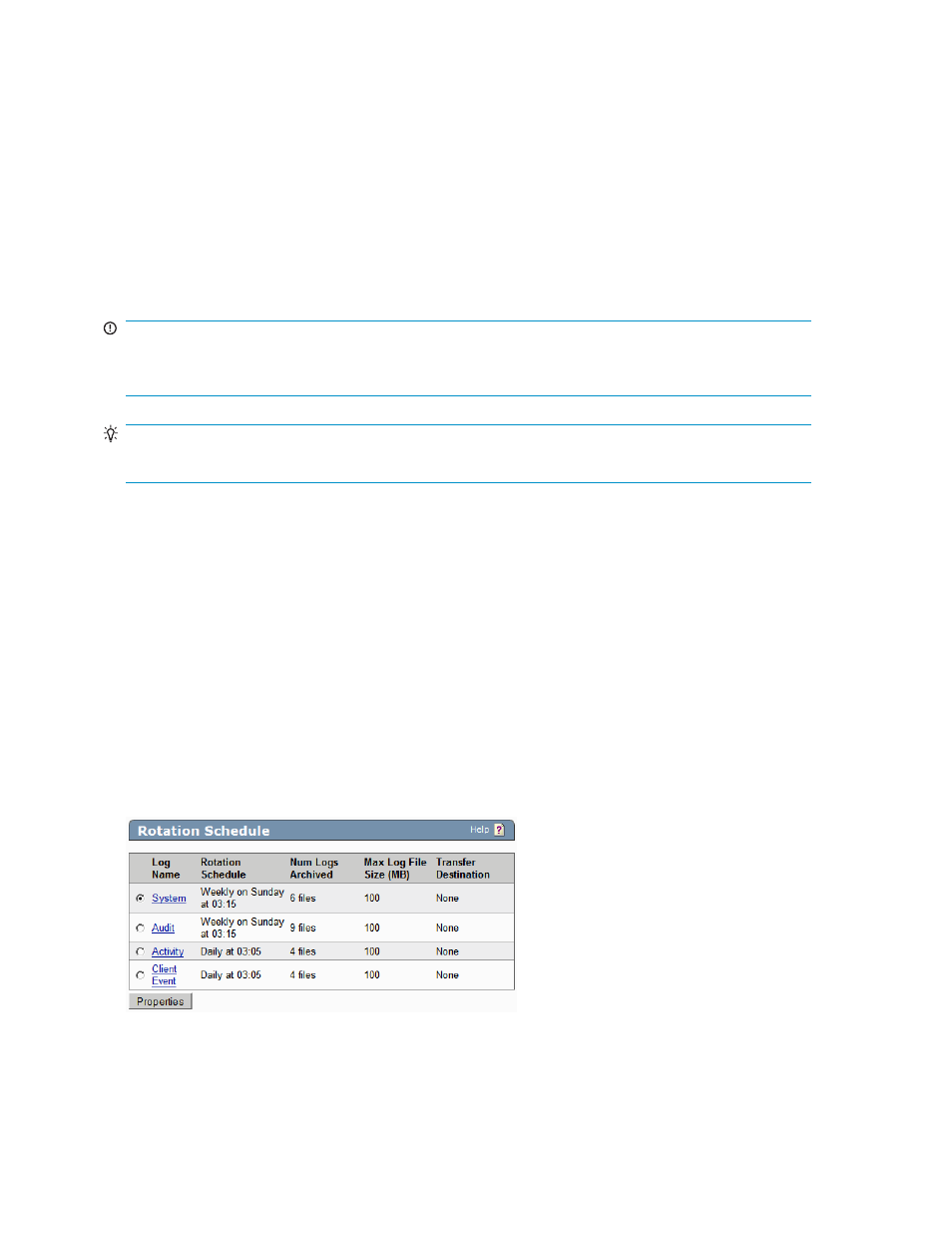
Rotation Schedule
The Rotation Schedule provides a summary view of the properties of the logs on an SKM.
Figure 135 Viewing the Rotation Schedule section
The following table describes the components of the Rotation Schedule section.
224
Using the Management Console
