Kms server authentication settings, 80 kms server settings section components, Server authentication settings – HP Secure Key Manager User Manual
Page 170
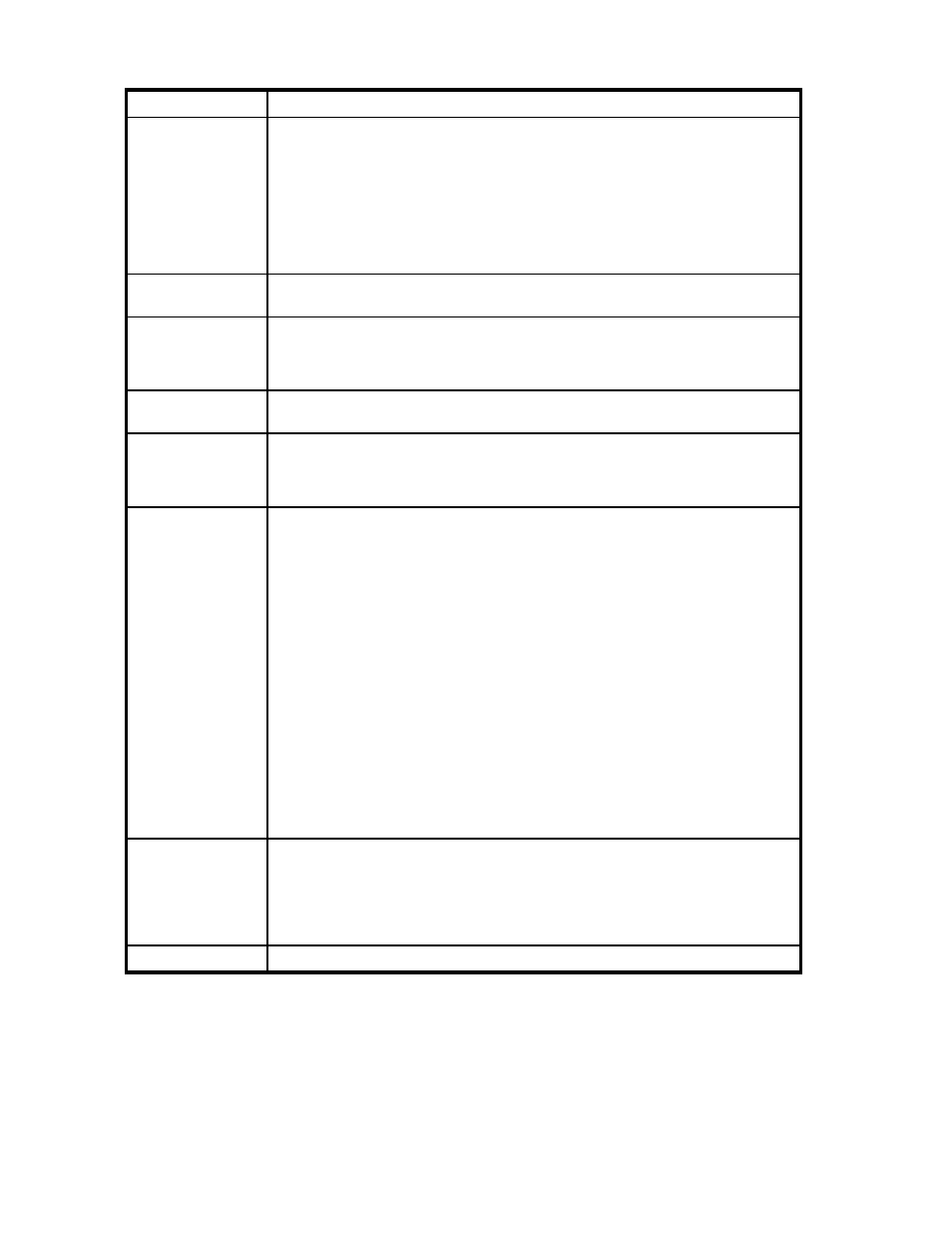
Table 80 KMS Server Settings section components
Component
Description
IP
This field specifies the IP address(es) on which the KMS Server is enabled on the SKM.
The drop-down box consists of all IP addresses bound to the SKM.
IMPORTANT:
We strongly recommend that you select a specific IP address instead of
specifying [All]. If you have four IP addresses bound to the SKM, then the KMS
Server listens for traffic on four different IP addresses; whereas, if you specify a
single IP address, the KMS Server listens for traffic on only one IP address. This
can greatly reduce system vulnerability to outside attacks.
Port
Port on which the KMS Server is listening for client requests. The default port is 9000;
however, you can use any available port.
Use SSL
Specify whether you want to require that clients connect to the KMS Server using an
SSL connection. A check mark in the box indicates that the KMS Server only accepts
traffic on an SSL connection. If the Use SSL option is not enabled, the KMS Server
will not accept SSL connections.
Server Certificate
If you are requiring SSL, you must provide the certificate that will be used to
authenticate the KMS Server to clients.
Connection Timeout
(sec)
The Connection Timeout value specifies in seconds how long client connections can
remain idle before the KMS Server begins closing them. The default value is 60; the
maximum value is 7200 (2 hours). Specifying a value of 0 means that the KMS Server
will not close client connections due to inactivity.
Allow Key and
Policy Configuration
Operations
When this feature is enabled, the KMS Server allows the following actions:
•
key creation and deletion.
•
key import.
•
users with User Administration Permission can create, delete, and modify users and
groups (available only through the XML interface.)
When this feature is disabled, only authentication, cryptographic, and random
number generation requests are available. By default, this feature is disabled.
When using the multiple credentials feature, enabling this option allows users (and
unauthenticated sessions) to perform the actions listed without being subjected to the
multiple credentials rule.
IMPORTANT:
This feature may pose a security loophole. You might allow this access for
automated scripts, or you might disallow it to tighten security.
IMPORTANT:
Enabling this feature on a FIPS-compliant device will take the device out of FIPS
compliance - possibly in a manner that does not comply with FIPS standards.
For information on disabling FIPS compliance, see
.
Allow Key Export
When this feature is enabled, the KMS Server allows key export.
IMPORTANT:
Enabling this feature on a FIPS-compliant device will take the device out of FIPS
compliance - possibly in a manner that does not comply with FIPS standards.
For information on disabling FIPS compliance, see
.
Edit
Click Edit to modify the KMS Server settings.
KMS Server Authentication Settings
The KMS Server Authentication Settings section, shown here, allows you to specify whether and how
clients authenticate to the KMS Server.
170
Using the Management Console
