Versioned keys, Group permissions, 48 viewing the key properties section – HP Secure Key Manager User Manual
Page 112: 28 key properties section components
key. Instead it gives a new name to the existing metadata and key bytes. To create a copy of an existing
key, use the Clone Key section.
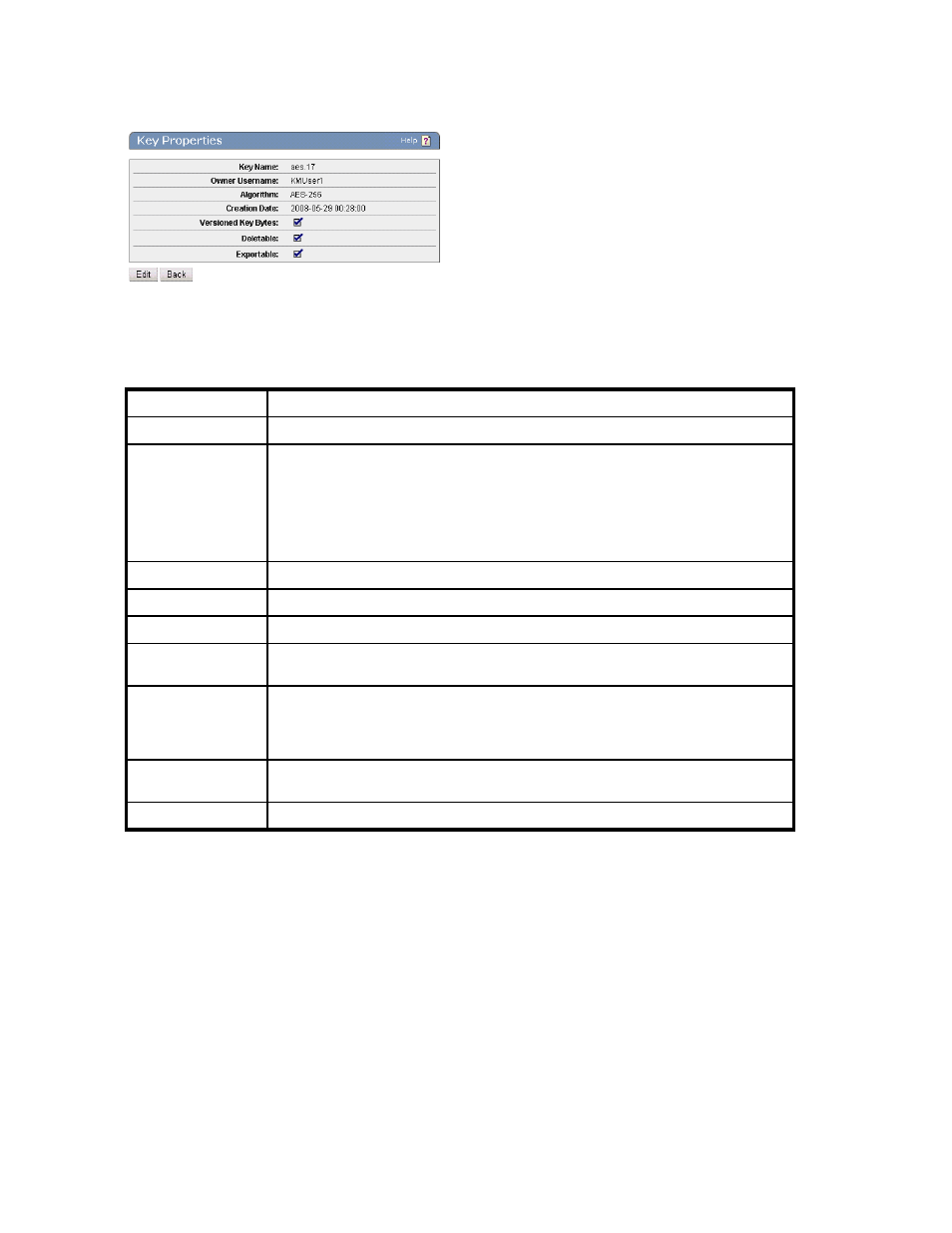
Figure 48 Viewing the Key Properties section
The following table describes the components of the Key Properties section.
Table 28 Key Properties section components
Component
Description
Key Name
Name of key described in the current row.
Owner Username
Name of the user that owns the key. If blank, the key is a global key and therefore
accessible to all users.
NOTE:
Once a key has an owner it is no longer a global key. You cannot change
it into a global key by removing the owner. This is true even if the key was
originally created as a global key.
Algorithm
The algorithm this key uses.
Creation Date
Display the timestamp made at the time of the key’s creation.
Versioned Key Bytes
Indicates if this is a versioned key.
Deletable
If selected, this key is deletable via an XML request by the key owner. This value
may be changed.
Exportable
If selected, this key is exportable via an XML request. An exportable key can be
exported by its owner and by members of a group with “Export” permission for the
key. A global key marked exportable can be exported by any user. This value
may be changed.
Edit
Click Edit to edit the Key Name, Owner Username, exportable, and deletable
settings.
Back
Click Back to return to the Key and Policy Configuration page.
Versioned keys
A versioned key maintains the same key metadata, but has a unique set of bytes for each version.
Thus, each version is different enough for encryption purposes, but similar enough to allow for easy
management. Each key version has its own key bytes, default IV, state, and creation date. The state
determines which key operations are available for a key version. Possible states are: active, restricted,
and retired.
•
Active: encryption and decryption and all key management options are allowed.
•
Restricted: only key information operations are allowed.
•
Retired: no operations or access to key management is allowed.
The state, combined with the key type and group permissions determine how the key version can be used.
Ultimately, a key version can only be used when: the key’s group permissions permit the operation, the
112
Using the Management Console
