Ssl cipher order, 98 viewing the ssl options section, 78 ssl options section components – HP Secure Key Manager User Manual
Page 166
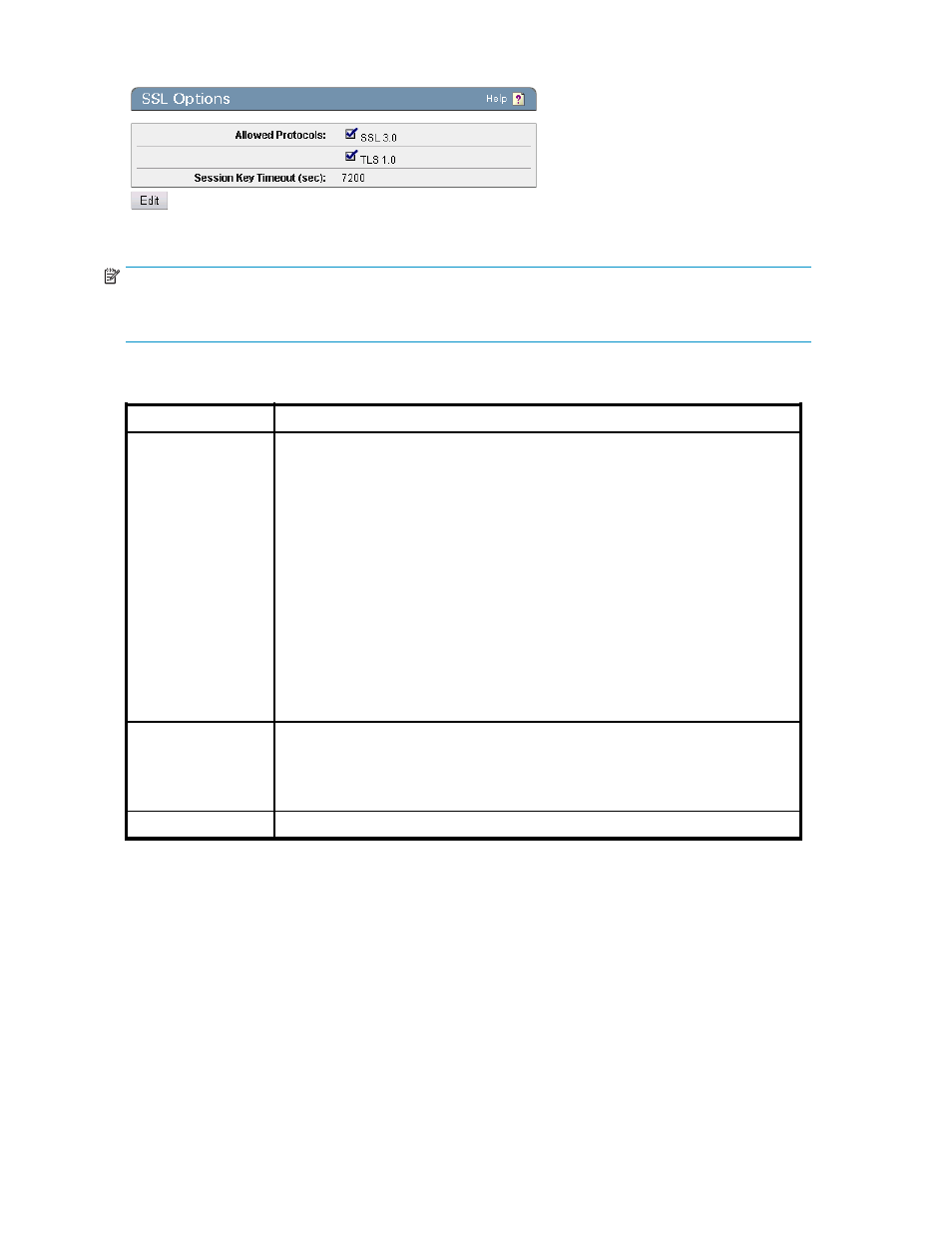
Figure 98 Viewing the SSL Options section
NOTE:
Changes to the SSL Options cause the KMS Server to restart, which takes the KMS offline for a few
seconds.
The following table describes the components of the SSL Options section.
Table 78 SSL Options section components
Component
Description
Allowed Protocols
The Allowed Protocols field allows you to specify which versions of SSL and TLS are
enabled on the SKM. The supported protocols are:
•
SSL 2.0 (Secure Sockets Layer version 2.0): This protocol is disabled by default
because it has many known security vulnerabilities. We strongly recommend that
you not enable this protocol.
•
SSL 3.0 (Secure Sockets Layer version 3.0).
•
TLS 1.0 (Transport Layer Security version 1.0).
NOTE:
If your internet browser is not configured to use the protocol selected here you
will be denied access to the Management Console. Consult and alter your
browser settings before changing these values.
NOTE:
Enabling SSL 2.0 or 3.0 on a FIPS-compliant device will take the device out
of FIPS compliance - possibly in a manner that does not comply with FIPS
standards. For information on disabling FIPS compliance, see
Session Key Timeout
(sec)
The Session Key Timeout option specifies the number of seconds that a previously
negotiated session key is reused for incoming SSL client connections to the SKM.
This option determines how frequently key renegotiation takes place on the client
application. The default value is 7200 seconds (2 hours). Setting this value to
0 disables the time-out.
Edit
Click Edit to modify the SSL options.
SSL Cipher Order
Use this section to enable, disable, and order the priority of SSL ciphers.
Different applications and databases support different encryption algorithms for securing SSL sessions. The
SKM supports many SSL ciphers and consequently can communicate securely using all common ciphers.
Please note that the SSL Cipher Order pertains to the communication channel between the client
(application, database, etc.) and the SKM. It does not affect the keys that might be used to encrypt data
by the KMS Server. When an application or database presents the SKM with a list of supported ciphers,
the SKM chooses the supported cipher that is highest on its priority list.
166
Using the Management Console
