High security procedures, Configuring the skm for fips compliance – HP Secure Key Manager User Manual
Page 159
IMPORTANT:
Modifying
any
of the items in the Security Settings Configured Elsewhere section immediately takes the
SKM out of FIPS compliance.
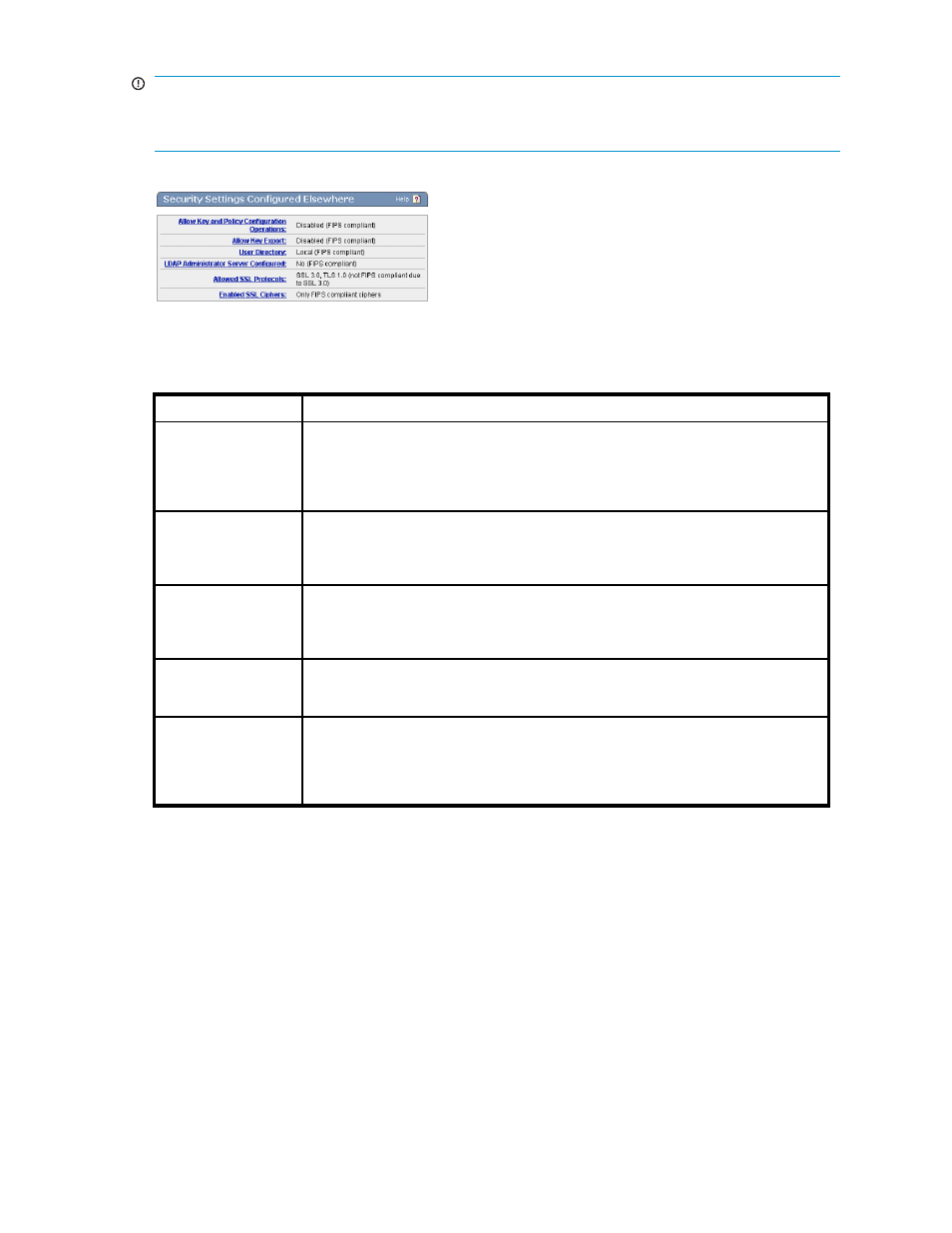
Figure 95 Viewing the Security Settings Configured Elsewhere section
The following table describes the components of the Security Settings Configured Elsewhere section.
Table 74 Security Settings Configured Elsewhere section components
Component
Description
Allow Key and
Policy Configuration
Operations
Displays the value of the Allow Key and Policy Configuration Operations field in
the KMS Server Settings section. When enabled, users can configure keys and
authorization policies through the XML Interface. Click the link to access the KMS
Server Settings section. For FIPS compliance, this functionality must be disabled,
or SSL must be enabled.
Allow Key Export
Displays the value of the Allow Key Export field in the KMS Server Settings section.
When enabled, users can export keys from the SKM through the XML Interface.
Click the link to access the KMS Server Settings section. For FIPS compliance, this
functionality must be disabled, or SSL must be enabled.
User Directory
Displays the value of the User Directory field in the KMS Server Authentication
Settings section, which determines whether the KMS Server uses a local directory
or an LDAP server. Click the link to access the KMS Server Authentication Settings
section. For FIPS compliance, a local user directory must be used.
Allowed SSL Protocols
Displays the SSL Protocols enabled in the SSL Options section. Click the link to
access the SSL Options section. FIPS compliance requires that SSL 2.0 and SSL
3.0 be disabled.
Enabled SSL Ciphers
Indicates the security strength of the SSL ciphers enabled in the SSL Cipher Order
section. Click the link to access the SSL Cipher Order section. On FIPS capable
devices, this field indicates if the enabled SSL ciphers permit FIPS compliance and, if
not, what is preventing compliance. For FIPS compliance, you must disable ciphers
with key sizes smaller than 128-bits and all RC4 ciphers.
High Security Procedures
This section describes the procedures for managing the high security features of SKM.
It explains the following processes:
• Configuring the Key Manager for FIPS Compliance
• Configuring the High Security Settings on a Key Manager
Configuring the SKM for FIPS Compliance
The HP DL360 R05 can be configured to comply with FIPS 140-2, Level 2 standards.
To configure the SKM for FIPS compliance:
Secure Key Manager
159
