C using the command line interface, Shell commands, Command line interface syntax – HP Secure Key Manager User Manual
Page 240: Quoting arguments, 155 viewing the kms statistics section, 139 kms statistics section components
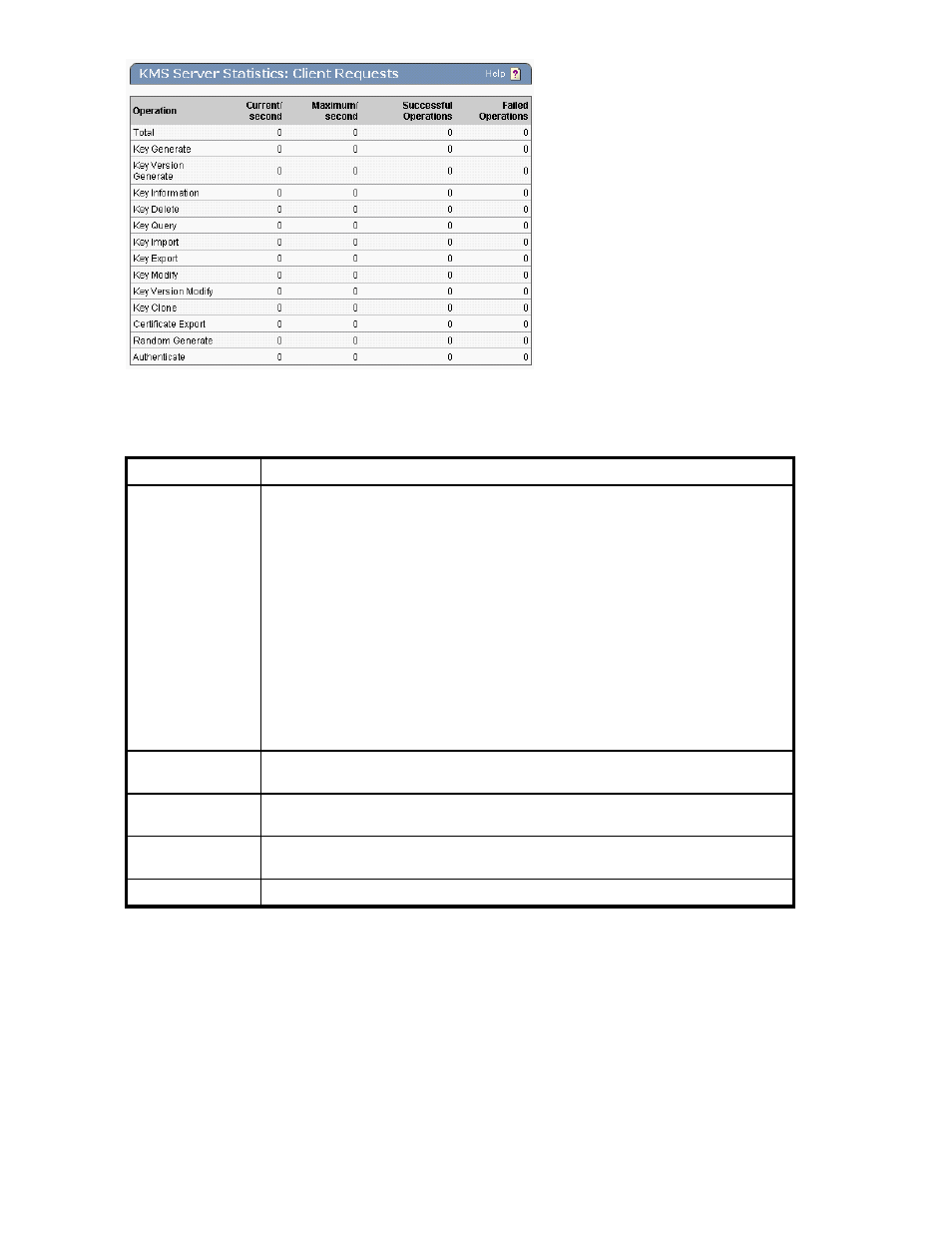
Figure 155 Viewing the KMS Statistics section
The following table describes the components of the KMS Statistics section.
Table 139 KMS Statistics section components
Component
Description
KMS Operations
•
Total - total number of client requests since the SKM was last rebooted.
•
Key Generate - request to generate a cryptographic key.
•
Key Information - requests for information about a particular key.
•
Key Delete - request to delete a key.
•
Key Query - request to view all keys available to a client.
•
Key Import - request to import a key.
•
Key Export - request to export a key.
•
Key Modify - request to modify a key.
•
Key Clone - request to clone a key.
•
Certificate Export - request to export a certificate.
•
Random Generate - request to generate a random byte sequence.
•
Cryptographic Operation - request to perform a cryptographic operation.
•
Authenticate - request to authenticate.
Current/second
The Current per second column shows how many of a given statistic were counted on
the SKM in the second the KMS Statistics were refreshed.
Maximum/second
The Maximum per second column shows the maximum number of a given statistic that
were counted by the SKM during any one second.
Successful
Operations
Displays the number of successful operations.
Failed Operations
Displays the number of failed operations.
240
Using the Management Console
