Password management overview, 104 create ldap administrator section components – HP Secure Key Manager User Manual
Page 206
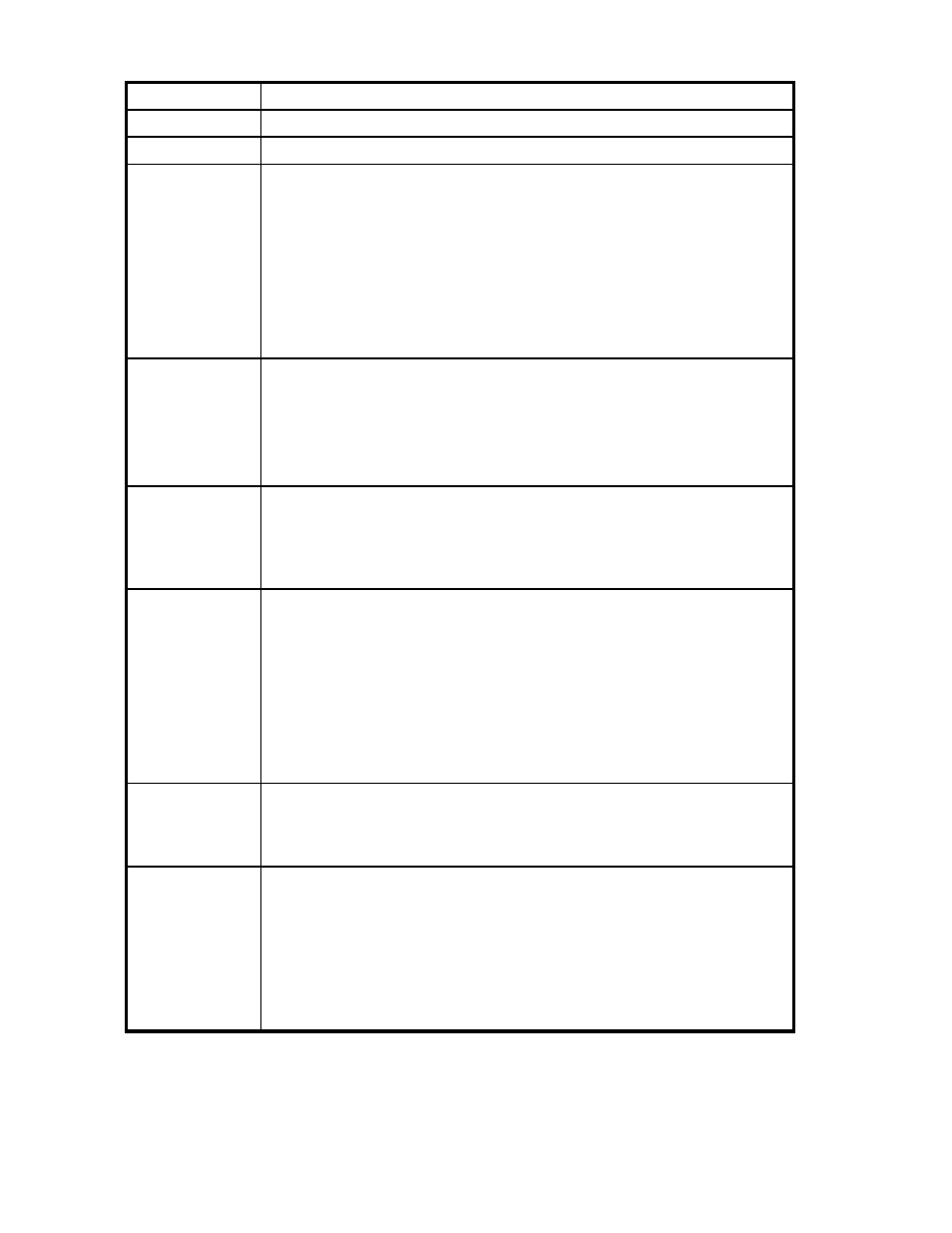
Table 104 Create LDAP Administrator section components
Component
Description
Username
Enter the login name the administrator uses to access the SKM.
Browse
Click to access the Select LDAP Username section.
Access Control
– Security
Configuration
Access control options related to device security configuration.
•
Keys and Authorization Policies: Create, modify and delete keys and establish
authorization policies.
•
Users and Groups: create and modify local users and groups and maintain LDAP
user server settings.
•
Certificates: Create and import certificates.
•
Certificate Authorities: Manage certificate authorities on the SKM.
•
Advanced Security: Manage advanced security settings, including FIPS
configuration.
•
SSL: Modify SSL configuration.
Access Control
– Device
Configuration
Access controls relating to general SKM configuration.
•
Cluster: create a cluster, join or remove this device from an existing cluster.
•
Network and Date/Time: Configure network and date/time settings.
•
High Availability: Enable and configure high availability settings.
•
SNMP: Manage SNMP community names and management stations.
•
Logging: Modify logging settings.
Access Control -
Enterprise Manager
Access control options relating to the Enterprise Manager feature. This section is only
visible when the Enterprise Manager feature is activated.
•
Enterprise Services: Access Enterprise Services.
•
Profile Creation & Configuration: Add, delete and edit profiles.
•
Profile Key Selection: Add and remove keys from profiles.
Access Control –
Backup & Restore
Access controls relating to backing up and restoring device and cryptographic
configurations.
•
Backup Configuration: Create system backups that include everything but keys,
certificates and local CAs.
•
Backup Keys & Certificates: Create backups of keys and certificates
•
Backup Local CAs: Create backups of local CAs.
•
Restore Configuration: Restore system backups that include everything but keys,
certificates and local CAs.
•
Restore Keys and Certificates: Restore backups of keys and certificates.
•
Restore Local CAs: Restore backups of local CAs.
Access Control –
Maintenance
Access control options relating to device maintenance.
•
Services: Modify startup service setting.
•
Software Upgrade and System Health: Upgrade to a new version of the software
and perform RAID disk add or remove options.
Access Control
– Administrative
Access
Access control options relating to remotely administering the SKM.
•
Admin Access via Web: Administer the SKM through the web interface.
•
Admin Access via SSH: Administer the SKM through SSH.
These access control options specify whether an administrator can configure the
SKM appliance from the Management Console and the CLI. You should note that
administrators who cannot log in via either of these interfaces can only manage
the SKM appliance from a serial console connection, which would preclude that
administrator from modifying almost all security configuration settings and some device
configuration settings (for example: Server, Keys, Users & Groups, Database Tools).
206
Using the Management Console
