Authentication of hosts (iscsi environments), Figure 12 – HP StorageWorks XP10000 Disk Array User Manual
Page 52
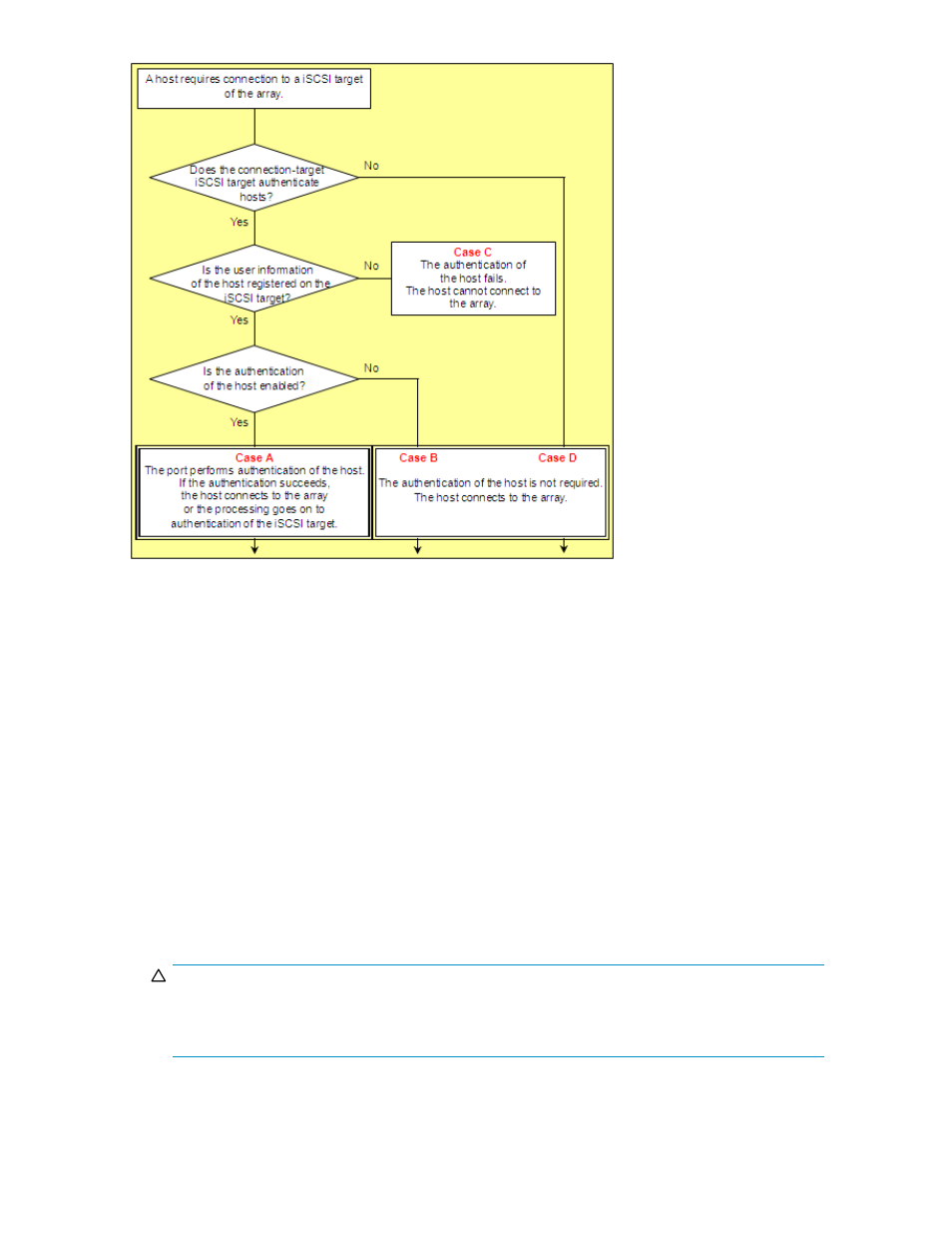
Figure 12 Authentication of hosts (iSCSI environments)
Case A to Case D in
are explained as follows:
•
Case A through Case C: When connecting via an iSCSI target that performs authentication of hosts
• Case A: If the host's user information is registered on the iSCSI target, and authentication of
the host is enabled
The iSCSI target authenticates the user information sent from the host. If authentication of the host
succeeds, either of the following actions occur:
• When the host is configured for mutual authentication, processing goes to authentication
of the iSCSI target.
• When the host is not configured for mutual authentication, the host connects to the array.
If the host is not configured for authentication by iSCSI targets with CHAP, the authentication
fails and the host cannot connect to the array.
• Case B: If the host's user information is registered on the iSCSI target, but authentication of
the host is disabled
The iSCSI target does not perform authentication of the host. The host connects to the array
without authentication regardless of whether or not the host is configured for authentication by
iSCSI targets with CHAP.
CAUTION:
If a host uses Microsoft iSCSI Initiator and is configured for authentication by iSCSI targets with
CHAP, authentication of the host fails. To allow such a host to connect to the iSCSI target without
authentication, do not configure it for authentication by ports with CHAP.
• Case C: If the host's user information is not registered on the iSCSI target
52
Overview of LUN Manager
