2 examples for configuration and protected volumes – Hitachi TAGMASTORE MK-90RD011-25 User Manual
Page 316
298
Chapter 4 Performing CCI Operations
4.16.2 Examples for Configuration and Protected Volumes
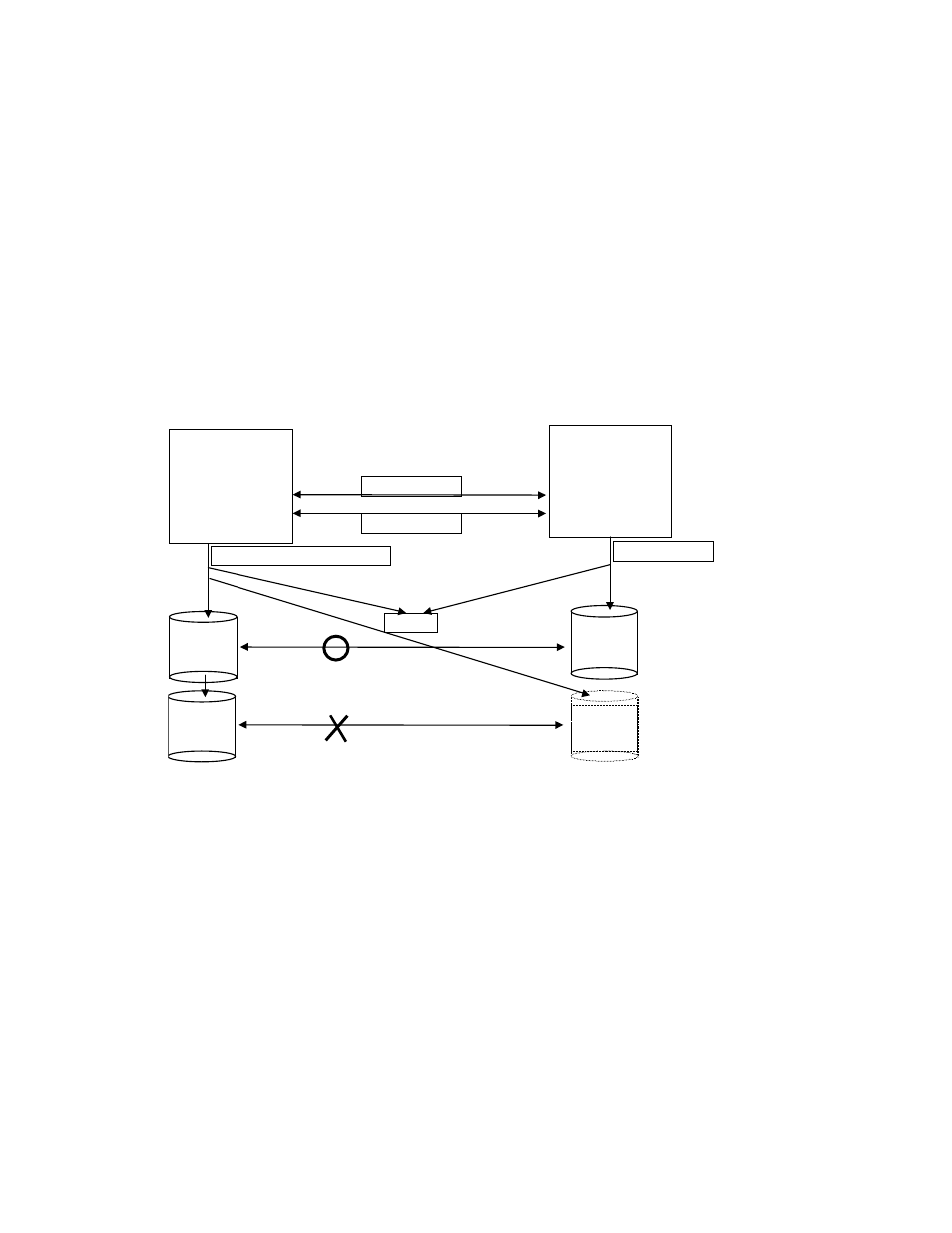
Case (1): Two Hosts (Figure 4.73). In protect mode Ora2 are rejected to be operate the
paired volume, because of Unknown for Grp4 on HOST2.
Case (2): One Host (Figure 4.74). In protect mode Ora1 and Ora2 are rejected to be operate
the paired volume, because of Unknown for Grp2 and Grp4 on HOST1. If HOST1 has a
protection OFF command device, then Ora1 and Ora2 are permitted to operate the paired
volume.
Note: The Protection Facility is implemented by only CCI. CCI needs to know the protection
attribute for the command device whether should be permitted the operation for paired
volume. If HORCM has protection ON command device at its time, then HORCM checks a
permission for a paired volume.
Grp1
Grp2
Horcm.conf on
HOST1
volumes for Grp1
volumes for Grp3
Horcm.conf on
HOST2
volumes for Grp2
volumes for Grp4
Visible to Grp2
Visible to Grp1,Grp3,Grp4
Grp3
Grp4
Ora1
Ora2
CM*
* CM = protection “On” command device
Figure 4.73 Example for the Two Host Configuration
