User authentication – HP XP7 Storage User Manual
Page 55
command device can be restricted. For the details about the settings to HORCM_ALLOW_INST,
please refer to "Configuration definition file".
•
Security setting for virtual command device
By using the following environment variable, security can be set to virtual command device.
$HORCM_IPCMDSEC=
Specify the number (from 0 to 7) to
want, in reference with the following table.
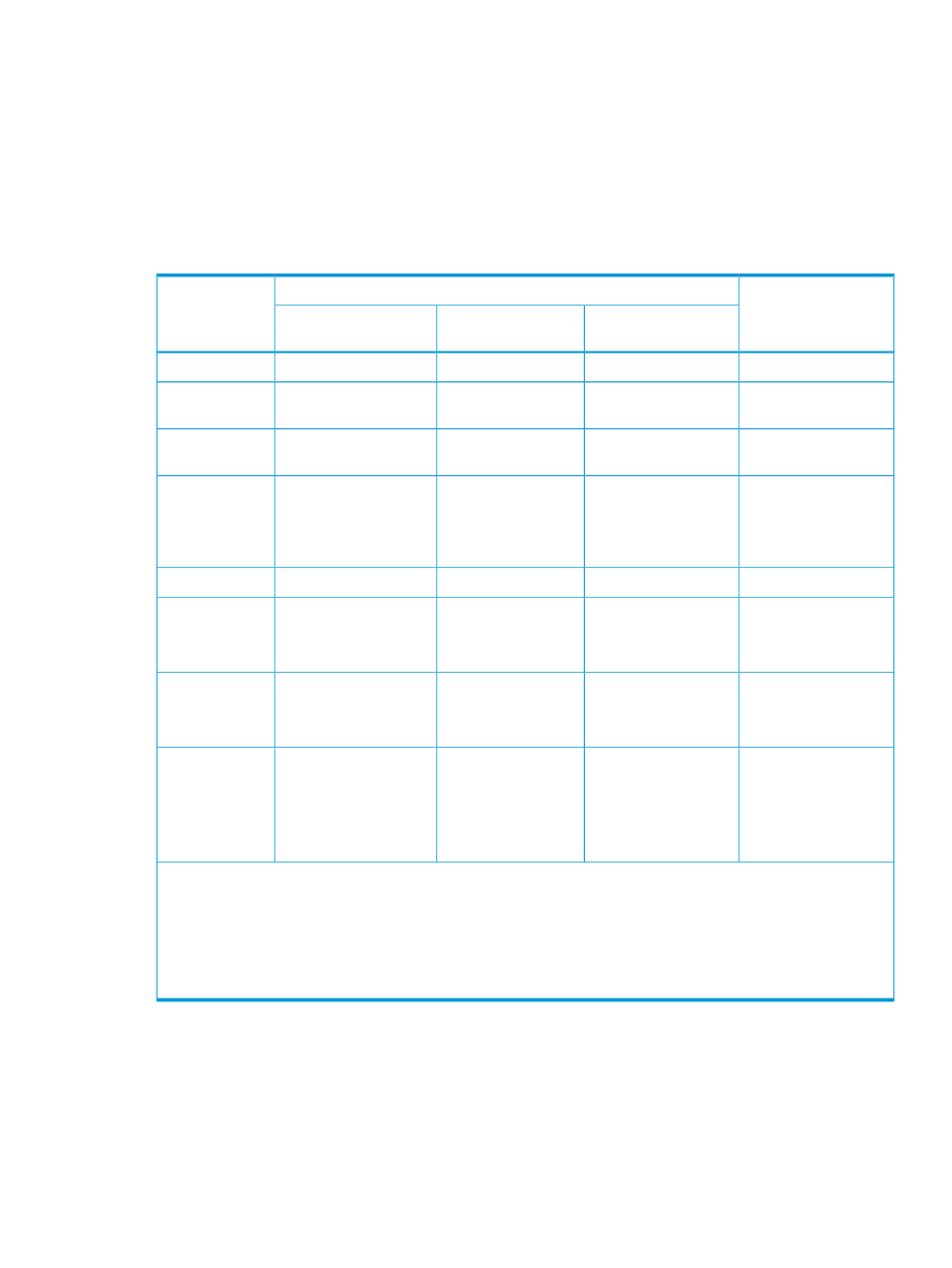
Table 13 Security setting for virtual command device
Security to be set
Command device setting
Value specifying
to
Group information
acquisition
User authentication
Security
No security
0
0
0
0
Only HORCM_DEV
allowed
1
0
0
1
User authentication
required
0
1
0
2
User authentication
required
1
1
0
3
Only HORCM_DEV
allowed
CMD security
0
0
1
4
CMD security
1
0
1
5
Only HORCM_DEV
allowed
CMD security
0
1
1
6
User authentication
required
CMD security
1
1
1
7
User authentication
required
Only HORCM_DEV
allowed
Notes:
•
Only HORCM_DEV allowed : means to be able to perform the operation for only paired logical volumes described
at HORCM_DEV.
•
User authentication required: means that only the commands issued by the authorized users can be executed.
•
CMD security: means that only the devices recognizable from the host can be operated. For details about CMD
security, please refer to "
“Data Protection facility” (page 189)
User authentication
RAID Manager allows user authentication by using the user information managed by Remote Web
Console and the SVP.
User authentication is arbitrary in the Replication operation in the in-band method while the operation
by user authentication is mandatory in the configuration information operation and in the out-of-band
method.
User authentication
55
