Interlogix NS3702-24P-4S User Manual User Manual
Page 112
112
Tagged:
Ports with tagging enabled will put the VID number, priority and other VLAN information into the
header of all packets that flow into those ports. If a packet has previously been tagged, the port
will not alter the packet, thus keeping the VLAN information intact. The VLAN information in the
tag can then be used by other 802.1Q compliant devices on the network to make
packet-forwarding decisions.
Untagged:
Ports with untagging enabled will strip the 802.1Q tag from all packets that flow into those
ports. If the packet doesn't have an 802.1Q VLAN tag, the port will not alter the packet. Thus,
all packets received by and forwarded by an untagging port will have no 802.1Q VLAN
information. (Remember that the PVID is only used internally within the Switch). Untagging is
used to send packets from an 802.1Q-compliant network device to a non-compliant network
device.
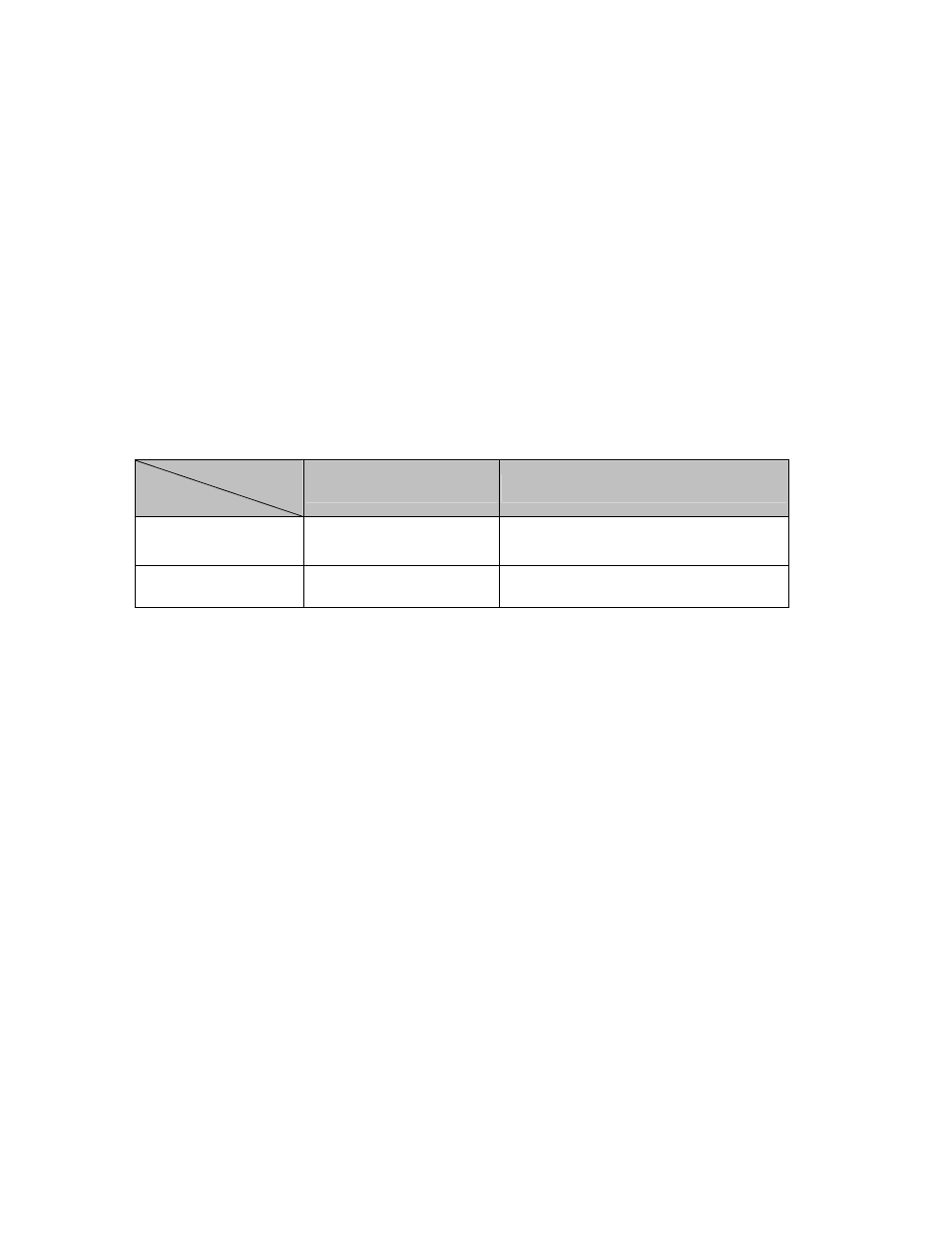
Frame Income
Frame Leave
Income Frame is tagged
Income Frame is untagged
Leave port is tagged
Frame remains tagged
Tag is inserted
Leave port is untagged
Tag is removed
Frame remain untagged
Table 4-6-1:
Ingress / Egress Port with VLAN VID Tag / Untag Table
■ IEEE 802.1Q Tunneling (Q-in-Q)
IEEE 802.1Q Tunneling (QinQ) is designed for service providers carrying traffic for multiple customers across their networks. QinQ
tunneling is used to maintain customer-specific VLAN and Layer 2 protocol configurations even when different customers use the
same internal VLAN IDs. This is accomplished by inserting Service Provider VLAN (SPVLAN) tags into the customer’s frames
when they enter the service provider’s network, and then stripping the tags when the frames leave the network.
A service provider’s customers may have specific requirements for their internal VLAN IDs and number of VLANs supported. VLAN
ranges required by different customers in the same service-provider network might easily overlap, and traffic passing through the
infrastructure might be mixed. Assigning a unique range of VLAN IDs to each customer would restrict customer configurations,
require intensive processing of VLAN mapping tables, and could easily exceed the maximum VLAN limit of 4096.
