Mpls applications – HP Intelligent Management Center Licenses User Manual
Page 33
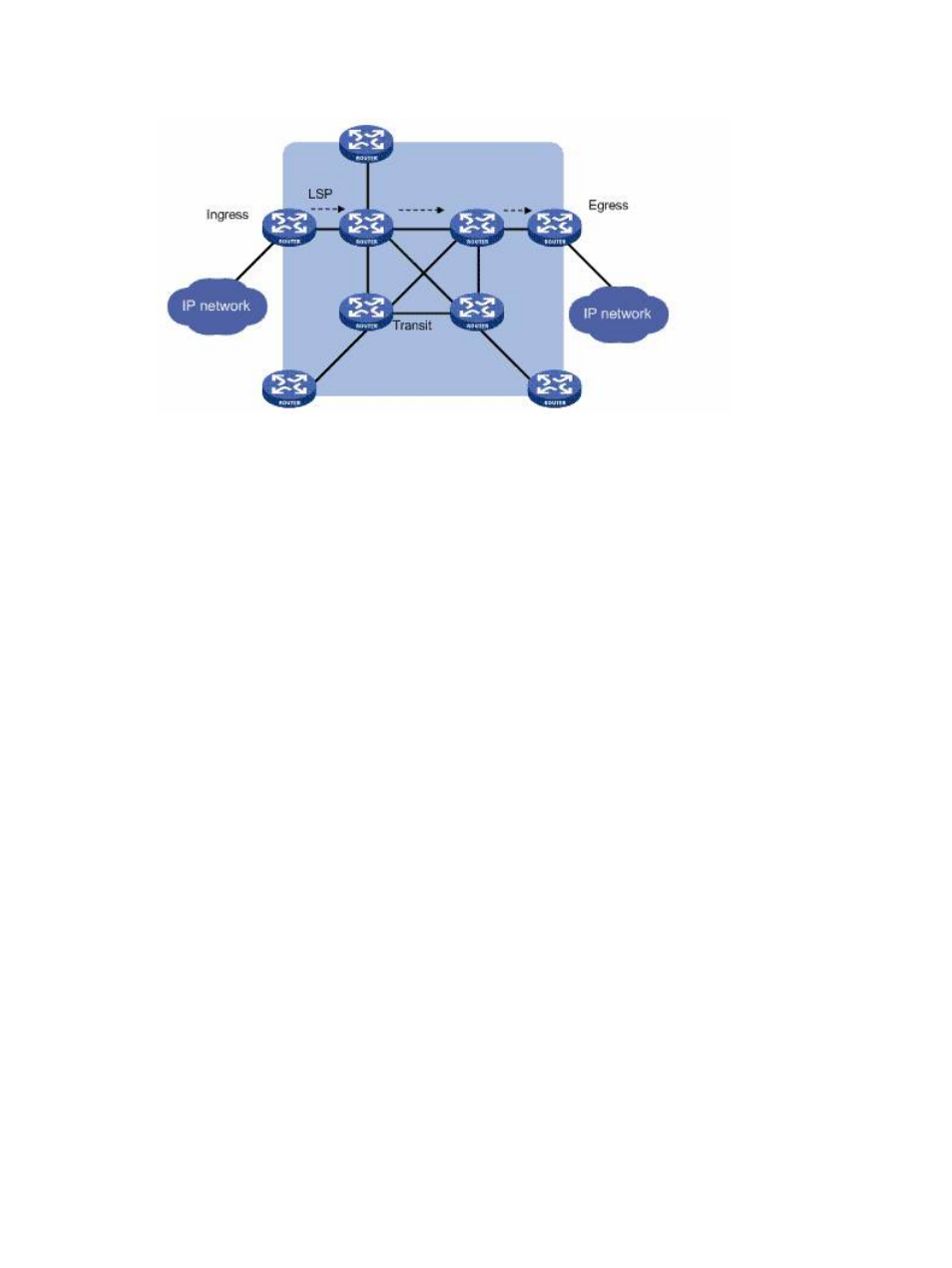
LER and then forwarded along an LSP to the egress LER. All the intermediate LSRs are called transit
LSRs.
The following describes how MPLS operates:
1.
First, the LDP protocol and the traditional routing protocol (such as OSPF and ISIS) work
together on each LSR to establish the routing table and the label information base (LIB) for
intended FECs.
2.
Upon receiving a packet, the ingress LER completes the Layer 3 functions, determines the FEC
to which the packet belongs, labels the packet, and forwards the labeled packet to the next
hop along the LSP.
3.
After receiving a packet, each transit LSR looks up its label forwarding table for the next hop
according to the label of the packet, replaces the label of the packet, and forwards the packet
to the next hop. None of the transit LSRs performs Layer 3 processing.
4.
When the egress LER receives the packet, it removes the label from the packet and performs
IP forwarding.
Obviously, MPLS is not a service or application, but actually a tunneling technology and a routing
and switching technology platform combining label switching with Layer 3 routing. This platform
supports multiple upper layer protocols and services, as well as secure transmission of information
to a certain degree.
MPLS Applications
By integrating both Layer 2 fast switching and Layer 3 routing, MPLS features improved route
lookup speed. However, with the development of the application specific integrated circuit (ASIC)
technology, route lookup speed is no longer the bottleneck hindering network development. This
makes MPLS not so outstanding in improving forwarding speed. Nonetheless, MPLS can easily
implement the seamless integration between IP networks and Layer 2 networks of ATM, frame
relay, and the like, and offer better solutions to TE (Traffic Engineering), and Virtual Private Network
(VPN) applications thanks to the following advantages.
1.
MPLS-based VPN
Traditional VPN depends on tunneling protocols such as GRE, L2TP, and PPTP to transport
data between private networks across public networks, while an LSP itself is a tunnel over
public networks. Therefore, implementation of VPN using MPLS is of natural advantages.
MPLS-based VPN connects geographically different branches of a private network to form a
united network by using LSPs as shown in the following figure.
MPLS Overview
33
