Security profile, Wep encryption 802.1x authentication – Proxim ORiNOCO AP-700 User Manual
Page 93
Performing Advanced Configuration
AP-700 User Guide
SSID/VLAN/Security
93
Security Profile
The AP supports the following Security features:
•
: The original encryption technique specified by the IEEE 802.11 standard.
•
: An IEEE standard for client authentication.
•
Wi-Fi Protected Access (WPA/WPA2)
: A new standard that provides improved encryption security over WEP.
WEP Encryption
The IEEE 802.11 standards specify an optional encryption feature, known as Wired Equivalent Privacy or WEP, that is designed to provide a
wireless LAN with a security level equal to what is found on a wired Ethernet network. WEP encrypts the data portion of each packet
exchanged on an 802.11 network using an Encryption Key (also known as a WEP Key).
When Encryption is enabled, two 802.11 devices must have the same Encryption Keys and both devices must be configured to use
Encryption in order to communicate. If one device is configured to use Encryption but a second device is not, then the two devices will not
communicate, even if both devices have the same Encryption Keys.
802.1x Authentication
IEEE 802.1x is a standard that provides a means to authenticate and authorize network devices attached to a LAN port. A port in the context
of IEEE 802.1x is a point of attachment to the LAN, either a physical Ethernet connection or a wireless link to an Access Point. 802.1x
requires a RADIUS server and uses the Extensible Authentication Protocol (EAP) as a standards-based authentication framework, and
supports automatic key distribution for enhanced security. The EAP-based authentication framework can easily be upgraded to keep pace
with future EAP types.
Popular EAP types include:
•
EAP-Message Digest 5 (MD5): Username/Password-based authentication; does not support automatic key distribution
•
EAP-Transport Layer Security (TLS): Certificate-based authentication (a certificate is required on the server and each client); supports
automatic key distribution
•
EAP-Tunneled Transport Layer Security (TTLS): Certificate-based authentication (a certificate is required on the server; a client’s
username/password is tunneled to the server over a secure connection); supports automatic key distribution
•
PEAP - Protected EAP with MS-CHAP: Secure username/password-based authentication; supports automatic key distribution
Different servers support different EAP types and each EAP type provides different features. Refer to the documentation that came with your
RADIUS server to determine which EAP types it supports.
NOTE
The AP supports the following EAP types when Security Mode is set to 802.1x, WPA, or 802.11i (WPA2): EAP-TLS, PEAP,
EAP-TTLS, EAP-MD5, and EAP-SIM.
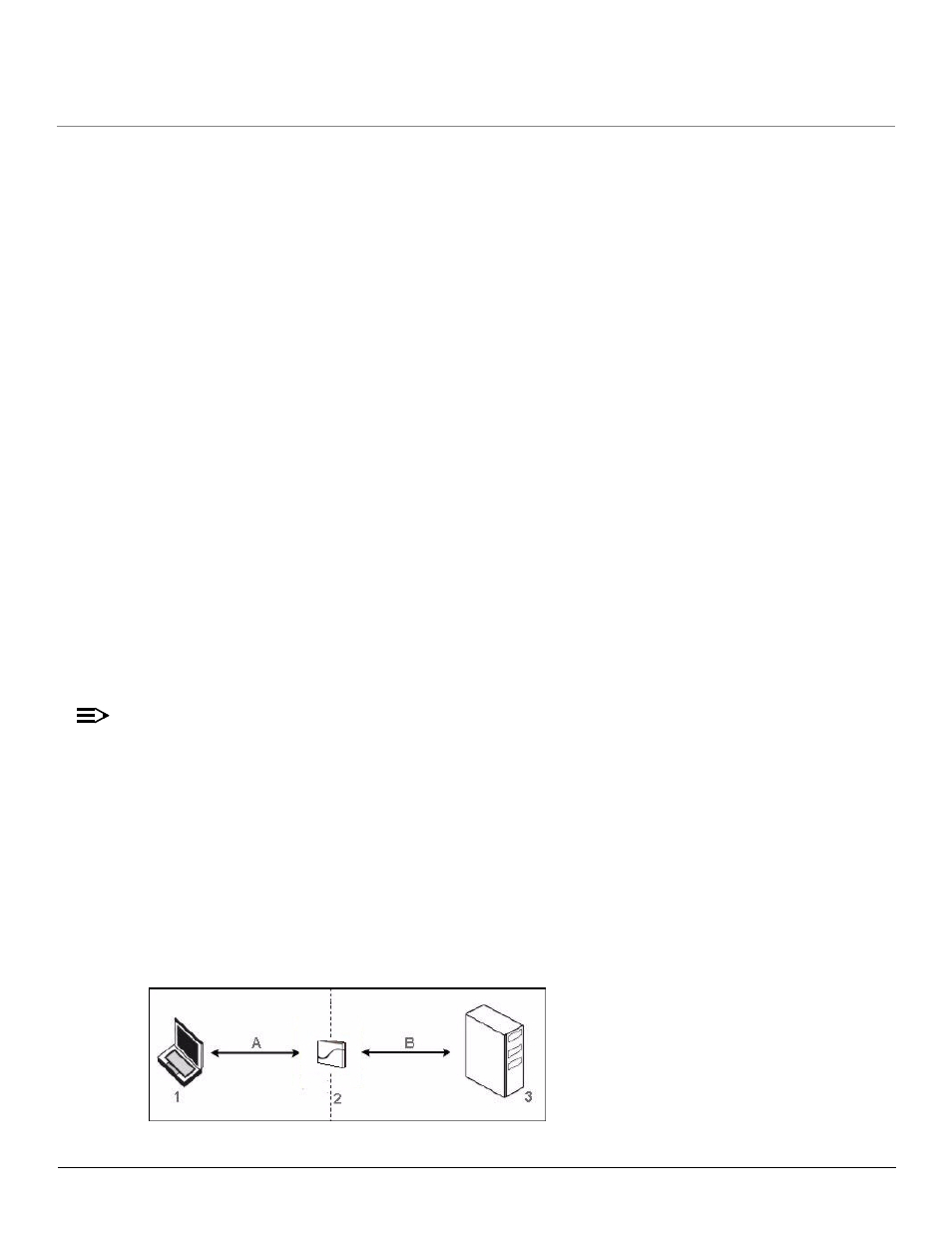
Authentication Process
There are three main components in the authentication process. The standard refers to them as:
1.
Supplicant (client PC)
2.
Authenticator (Access Point)
3.
Authentication server (RADIUS server)
When the Security Mode is set to 802.1x Station, WPA Station, or 802.11i Station you need to configure your RADIUS server for
authentication purposes.
Prior to successful authentication, an unauthenticated client PC cannot send any data traffic through the AP device to other systems on the
LAN. The AP inhibits all data traffic from a particular client PC until the client PC is authenticated. Regardless of its authentication status, a
client PC can always exchange 802.1x messages in the clear with the AP (the client begins encrypting data after it has been authenticated).
Figure 4-36 RADIUS Authentication Illustrated
