Tracert – H3C Technologies H3C S6300 Series Switches User Manual
Page 16
3
2.
The intermediate device (Device B) adds the IP address of its outbound interface (1.1.2.1) to the RR
option of the ICMP echo request, and forwards the packet.
3.
Upon receiving the request, the destination device copies the RR option in the request and adds the
IP address of its outbound interface (1.1.2.2) to the RR option. Then the destination device sends
an ICMP echo reply.
4.
The intermediate device adds the IP address of its outbound interface (1.1.1.2) to the RR option in
the ICMP echo reply, and then forwards the reply.
5.
Upon receiving the reply, the source device adds the IP address of its inbound interface (1.1.1.1)
to the RR option. The detailed information of routes from Device A to Device C is formatted as:
1.1.1.1 <-> {1.1.1.2; 1.1.2.1} <-> 1.1.2.2.
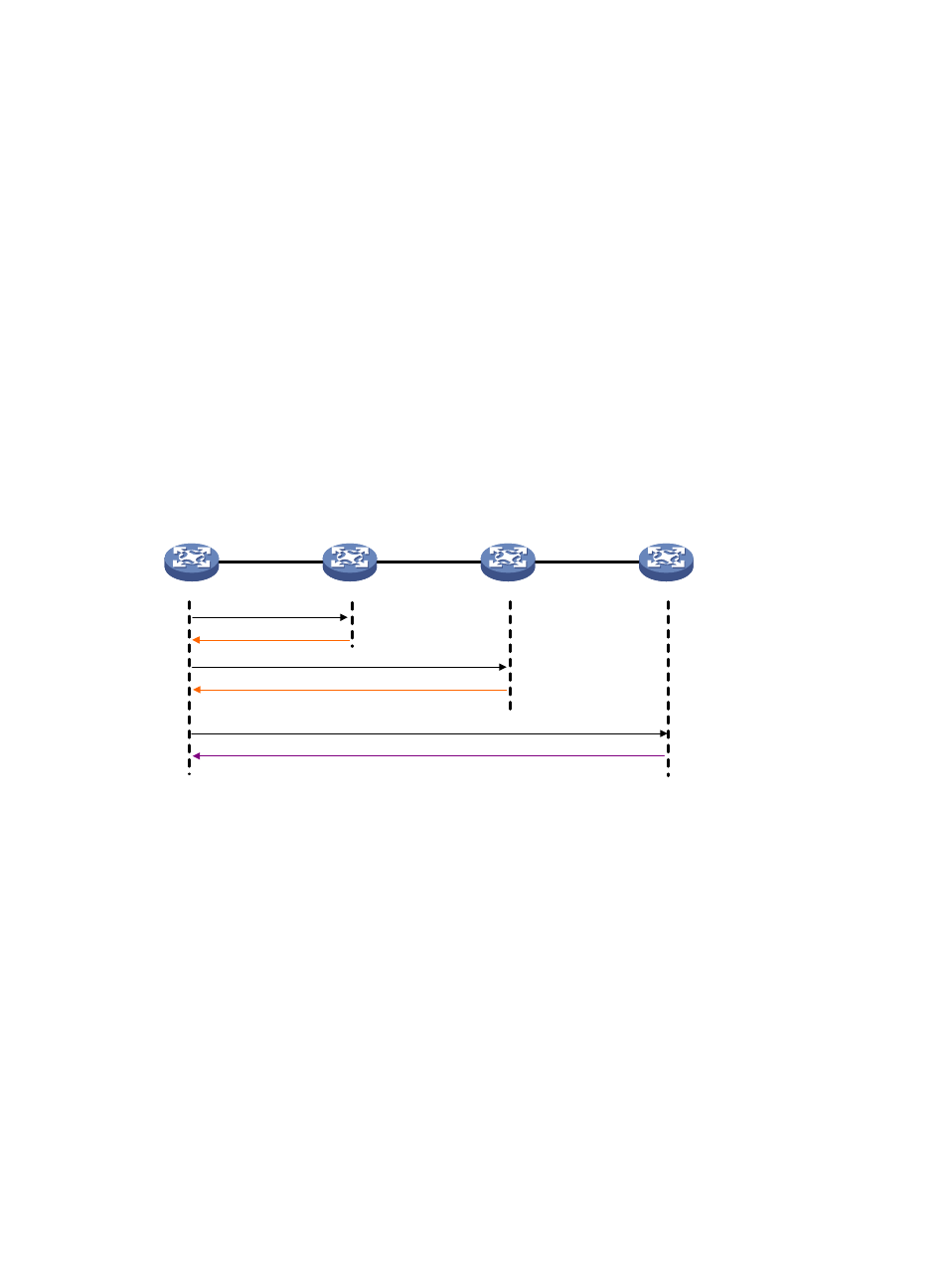
Tracert
Tracert (also called "Traceroute") enables retrieval of the IP addresses of Layer 3 devices in the path to a
specific destination. In the event of network failure, use tracert to test network connectivity and identify
failed nodes.
Figure 2 Tracert operation
Tracert uses received ICMP error messages to get the IP addresses of devices. Tracert works as shown
in
:
1.
The source device sends a UDP packet with a TTL value of 1 to the destination device. The
destination UDP port is not used by any application on the destination device.
2.
The first hop (Device B, the first Layer 3 device that receives the packet) responds by sending a
TTL-expired ICMP error message to the source, with its IP address (1.1.1.2) encapsulated. This
way, the source device can get the address of the first Layer 3 device (1.1.1.2).
3.
The source device sends a packet with a TTL value of 2 to the destination device.
4.
The second hop (Device C) responds with a TTL-expired ICMP error message, which gives the
source device the address of the second Layer 3 device (1.1.2.2).
5.
This process continues until a packet sent by the source device reaches the ultimate destination
device. Because no application uses the destination port specified in the packet, the destination
device responds with a port-unreachable ICMP message to the source device, with its IP address
encapsulated. This way, the source device gets the IP address of the destination device (1.1.3.2).
Device A
Device B
Device D
Device C
1.1.1.1/24
1.1.1.2/24
Hop Lmit=1
TTL exceeded
1.1.2.1/24
1.1.3.1/24
1.1.2.2/24
1.1.3.2/24
Hop Lmit=2
TTL exceeded
UDP port unreachable
Hop Lmit=n
