Snmp operations, Protocol versions, Configuring snmp basic parameters – H3C Technologies H3C S6300 Series Switches User Manual
Page 103
90
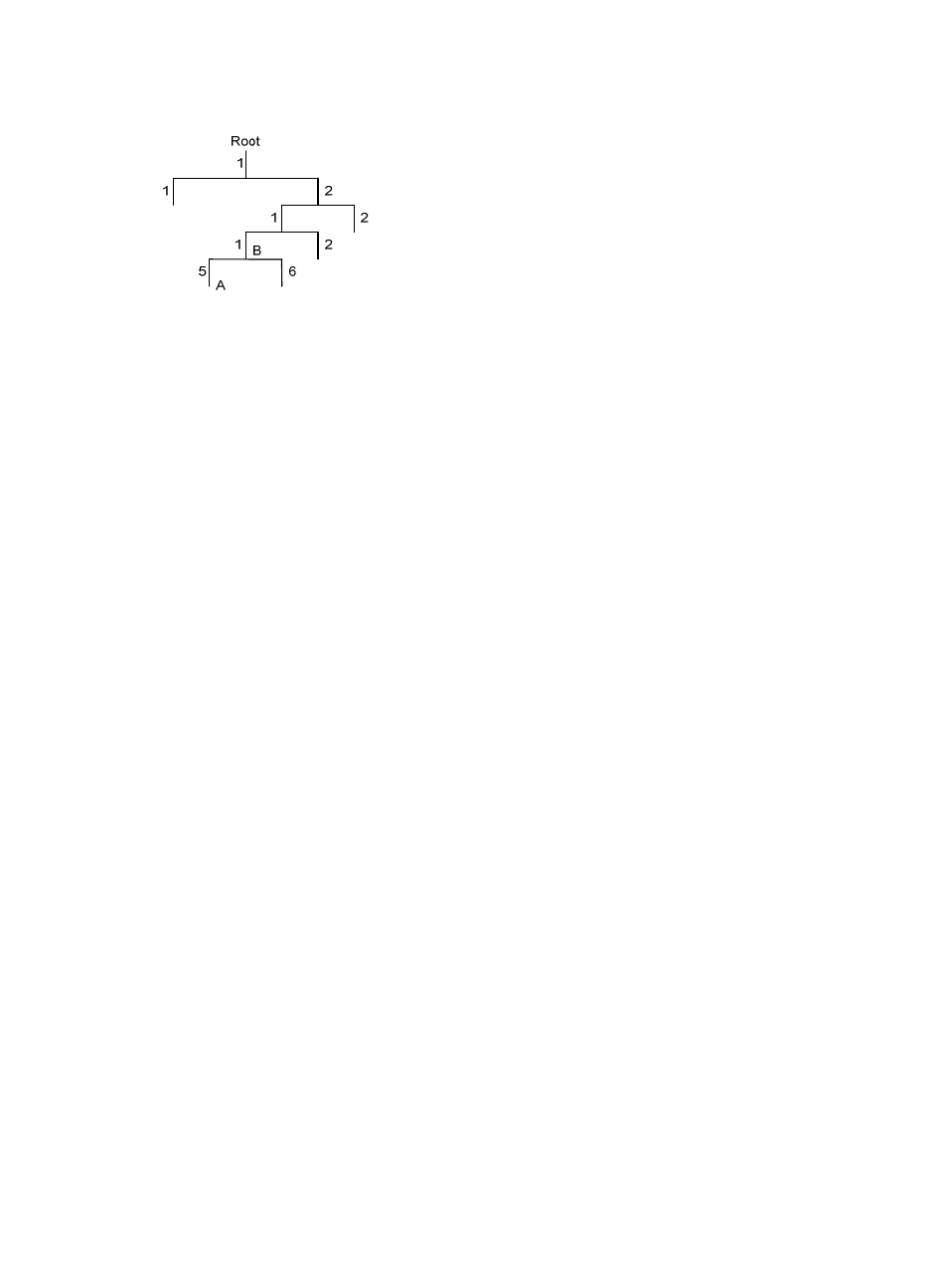
Figure 29 MIB tree
A MIB view represents a set of MIB objects (or MIB object hierarchies) with certain access privileges and
is identified by a view name. The MIB objects included in the MIB view are accessible while those
excluded from the MIB view are inaccessible.
A MIB view can have multiple view records each identified by a view-name oid-tree pair.
You control access to the MIB by assigning MIB views to SNMP groups or communities.
SNMP operations
SNMP provides the following basic operations:
•
Get—NMS retrieves the SNMP object nodes in an agent MIB.
•
Set—NMS modifies the value of an object node in an agent MIB.
•
Notification—SNMP agent sends traps or informs to report events to the NMS. The difference
between these two types of notification is that informs require acknowledgement but traps do not.
Traps are available in SNMPv1, SNMPv2c, and SNMPv3, but informs are available only in
SNMPv2c and SNMPv3.
Protocol versions
SNMPv1, SNMPv2c, and SNMPv3 are supported in non-FIPS mode. Only SNMPv3 is supported in FIPS
mode. An NMS and an SNMP agent must use the same SNMP version to communicate with each other.
•
SNMPv1—Uses community names for authentication. To access an SNMP agent, an NMS must use
the same community name as set on the SNMP agent. If the community name used by the NMS
differs from the community name set on the agent, the NMS cannot establish an SNMP session to
access the agent or receive traps from the agent.
•
SNMPv2c—Uses community names for authentication. SNMPv2c is compatible with SNMPv1, but
supports more operation types, data types, and error codes.
•
SNMPv3—Uses a user-based security model (USM) to secure SNMP communication. You can
configure authentication and privacy mechanisms to authenticate and encrypt SNMP packets for
integrity, authenticity, and confidentiality.
Configuring SNMP basic parameters
SNMPv3 differs from SNMPv1 and SNMPv2c in many ways. Their configuration procedures are
described in separate sections.
