Wi-fi protected access (wpa), Advanced configuration – HP ProCurve 520wl Wireless Access Point User Manual
Page 77
Advanced Configuration
NOTE
The AP supports the following EAP types when Authentication Mode is set to 802.1x or WPA: EAP-TLS,
PEAP, and EAP-TTLS. When Authentication Mode is set to Mixed, the AP supports the following EAP types:
EAP-TLS, PEAP, EAP-TLLS, and EAP-MD5 (MD5 does not support automatic key distribution; therefore, if
you choose this method you need to manually configure each client with the network's encryption key).
Authentication Process
There are three main components in the authentication process. The standard refers to them as:
1. supplicant (client PC)
2. authenticator (Access Point)
3. authentication server (RADIUS server)
When using Authentication Mode is set to 802.1x, WPA, or Mixed mode (802.1x and WEP), you need to configure your
RADIUS server for authentication purposes.
Prior to successful authentication, an unauthenticated client PC cannot send any data traffic through the AP device to
other systems on the LAN. The AP inhibits all data traffic from a particular client PC until the client PC is authenticated.
Regardless of its authentication status, a client PC can always exchange 802.1x messages in the clear with the AP
(the client begins encrypting data after it has been authenticated).
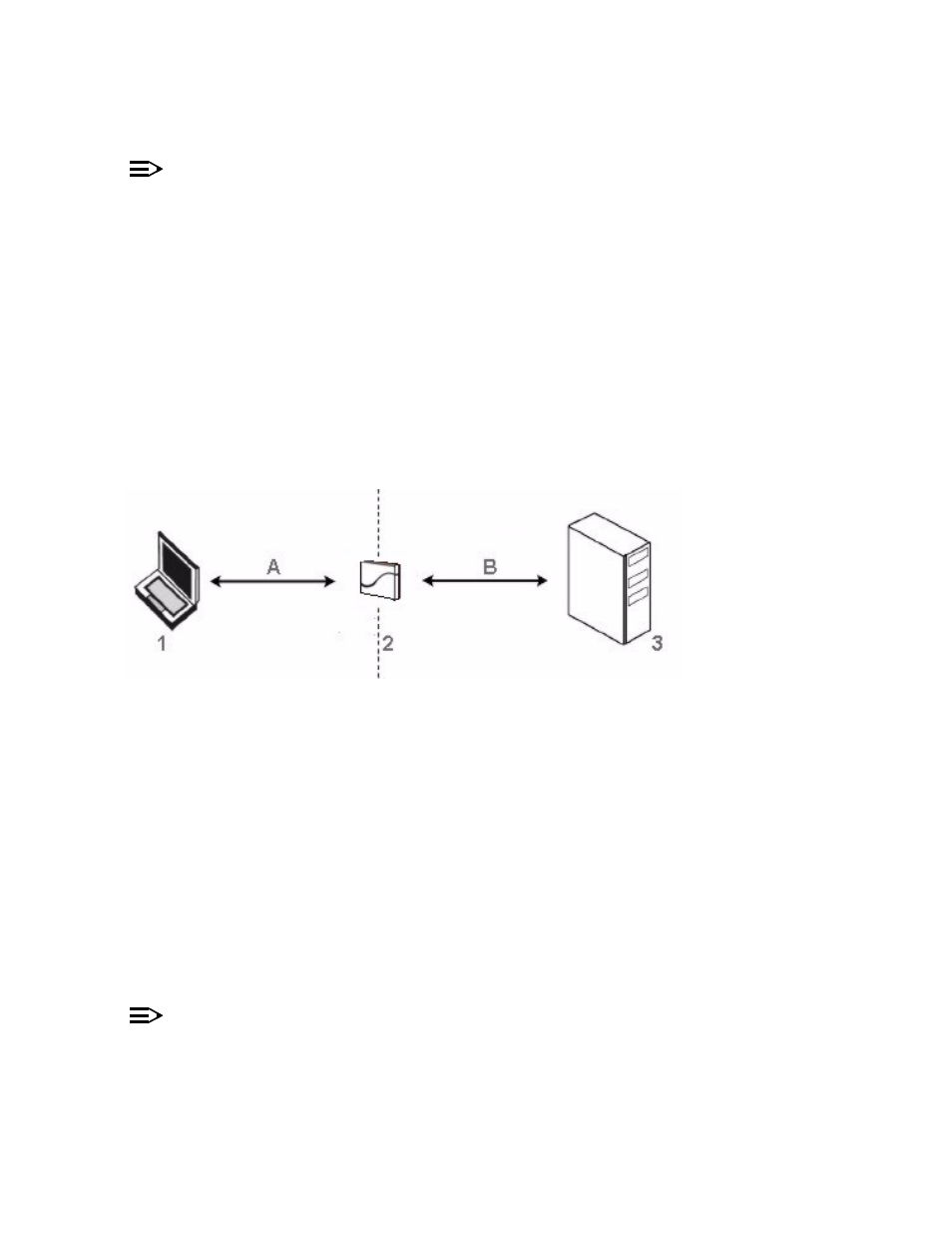
Figure 4-15 RADIUS Authentication Illustrated
The AP acts as a pass-through device to facilitate communications between the client PC and the RADIUS server. The
AP (2) and the client (1) exchange 802.1x messages using an EAPOL (EAP Over LAN) protocol (A). Messages sent
from the client station are encapsulated by the AP and transmitted to the RADIUS (3) server using EAP extensions (B).
Upon receiving a reply EAP packet from the RADIUS, the message is typically forwarded to the client, after translating
it back to the EAPOL format. Negotiations take place between the client and the RADIUS server. After the client has
been successfully authenticated, the client receives an Encryption Key from the AP (if the EAP type supports
automatic key distribution). The client uses this key to encrypt data after it has been authenticated.
For 802.11a and 802.11b/g clients that communicate with an AP, each client receives its own unique encryption key;
this is known as Per User Per Session Encryption Keys.
Wi-Fi Protected Access (WPA)
Wi-Fi Protected Access (WPA) is a security standard designed by the Wi-Fi Alliance in conjunction with the Institute of
Electrical and Electronics Engineers (IEEE). WPA is a sub-set of the forthcoming IEEE 802.11i security standard,
currently in draft form. (IEEE 802.11i is also referred to as "WPA2" and will be available in 2004.)
NOTE
For Dual-radio APs: WPA is available for APs an HP ProCurve Wireless 802.11g AP Card 170wl only.
WPA is a replacement for Wired Equivalent Privacy (WEP), the encryption technique specified by the original 802.11
standard. WEP has several vulnerabilities that have been widely publicized. WPA addresses these weaknesses and
provides a stronger security system to protect wireless networks.
4-35
