CANOGA PERKINS 9175 Configuration Guide User Manual
Page 255
CanogaOS Configuration Guide
39-6
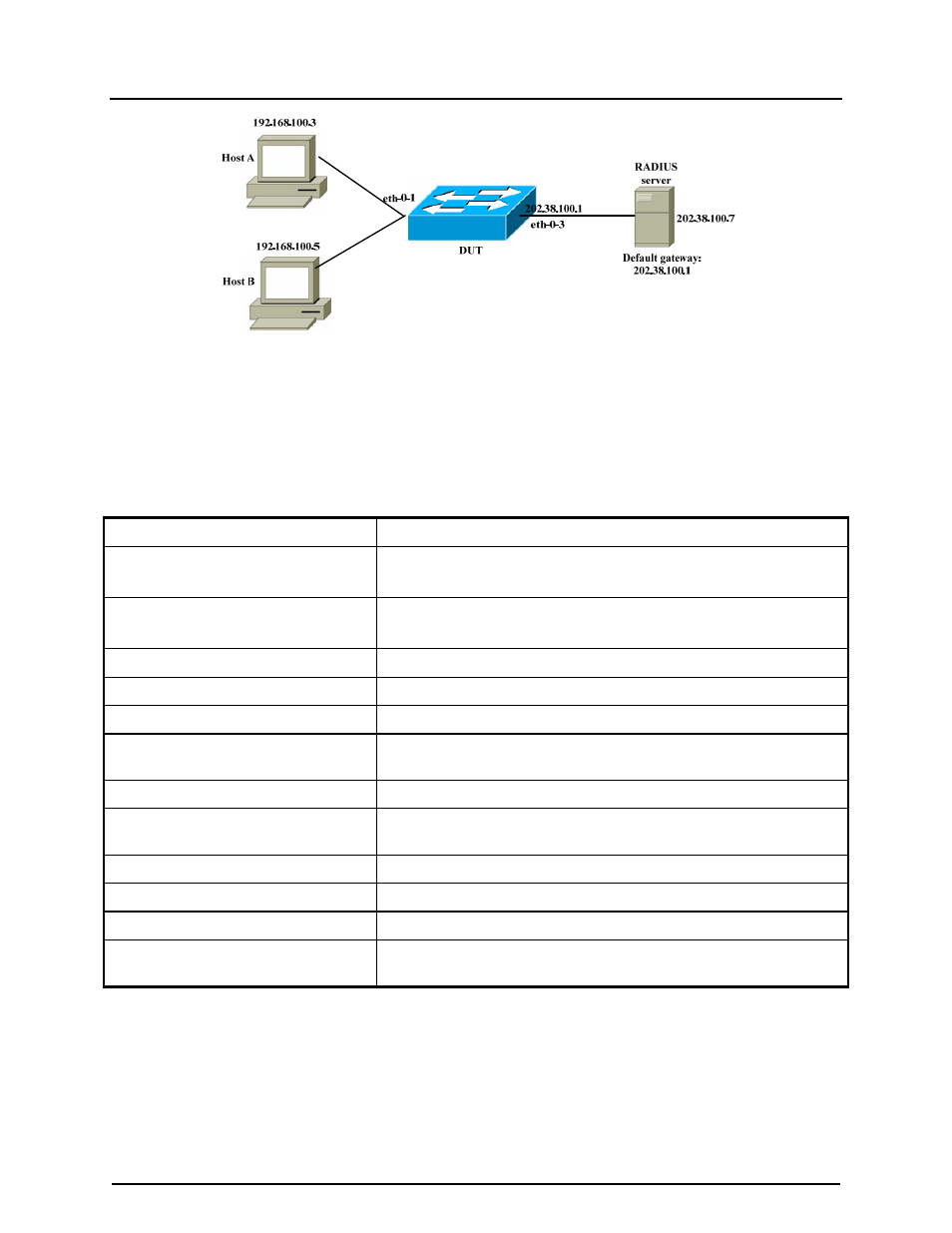
Figure 39-2: 802.1X Authentication
In this example, the Radius Server keeps the Client information, validating the identity of
the Client and updating the switch about the authentication status of the client. The
Switch is the physical access between the two Clients and the Server. It requests
information from the client, relays information to the Server and then back to the Client.
To configure 802.1x authentication, first enable authentication on ports eth-0-1 and then
specify the Radius Server IP address and port.
DUT# configure terminal
Enter the Configure mode.
DUT(config)# dot1x system-auth-ctrl
Enable IEEE 802.1x authentication globally on the switch.
DUT(config)#radius-server host
202.38.100.7 key test
Specify the radius server and the shared key
DUT(config)#interface eth-0-1
Enter the interface mode
DUT(config-if)#swichport mode access Set the port to access mode
DUT(config-if)# dot1x port-control auto
Enable IEEE 802.1x authentication on the interface
DUT(config-if)# dot1x port-control dir
both
Set the control direction as both
DUT(config-if)# dot1x reauthentication
Enable reauthentication
DUT(config-if)# dot1x timeout
re-authperiod 7200
Set the timer: re-auth period to 2 hours(7200)
DUT(config)# exit
Exit interface mode and enter the Configure mode.
DUT(config)#interface eth-0-3
Enter the interface mode
DUT(config-if)# no switchport
Configure the port as layer3 routed port
DUT(config-if)# ip address
202.38.100.1/24
Set the IP address for the routed port
Configuring the Switch-to-RADIUS-Server Communication
RADIUS security servers are identified by their host name or IP address, host name and
specific UDP port numbers, or IP address and specific UDP port numbers. The
combination of the IP address and UDP port number creates a unique identifier, which
enables RADIUS requests to be sent to multiple UDP ports on a server at the same IP
