5 ports in authorized and unauthorized state, Canogaos configuration guide 39-3 – CANOGA PERKINS 9175 Configuration Guide User Manual
Page 252
CanogaOS Configuration Guide
39-3
RADIUS
server
EAPOL
Client
EAPOR
EAPOL-Start
EAP-Request/identity
EAP-Response/identity
RADIUS Aceess-Request
RADIUS Aceess-challenge
EAP-Request/OTP
EAP-Response/OTP
RADIUS Aceess-Request
RADIUS Aceess-Accept
EAPOL-Success
EAP-Request/identity
EAP-Response/identity
EAPOL-Logoff
Port authorized
Port unauthorized
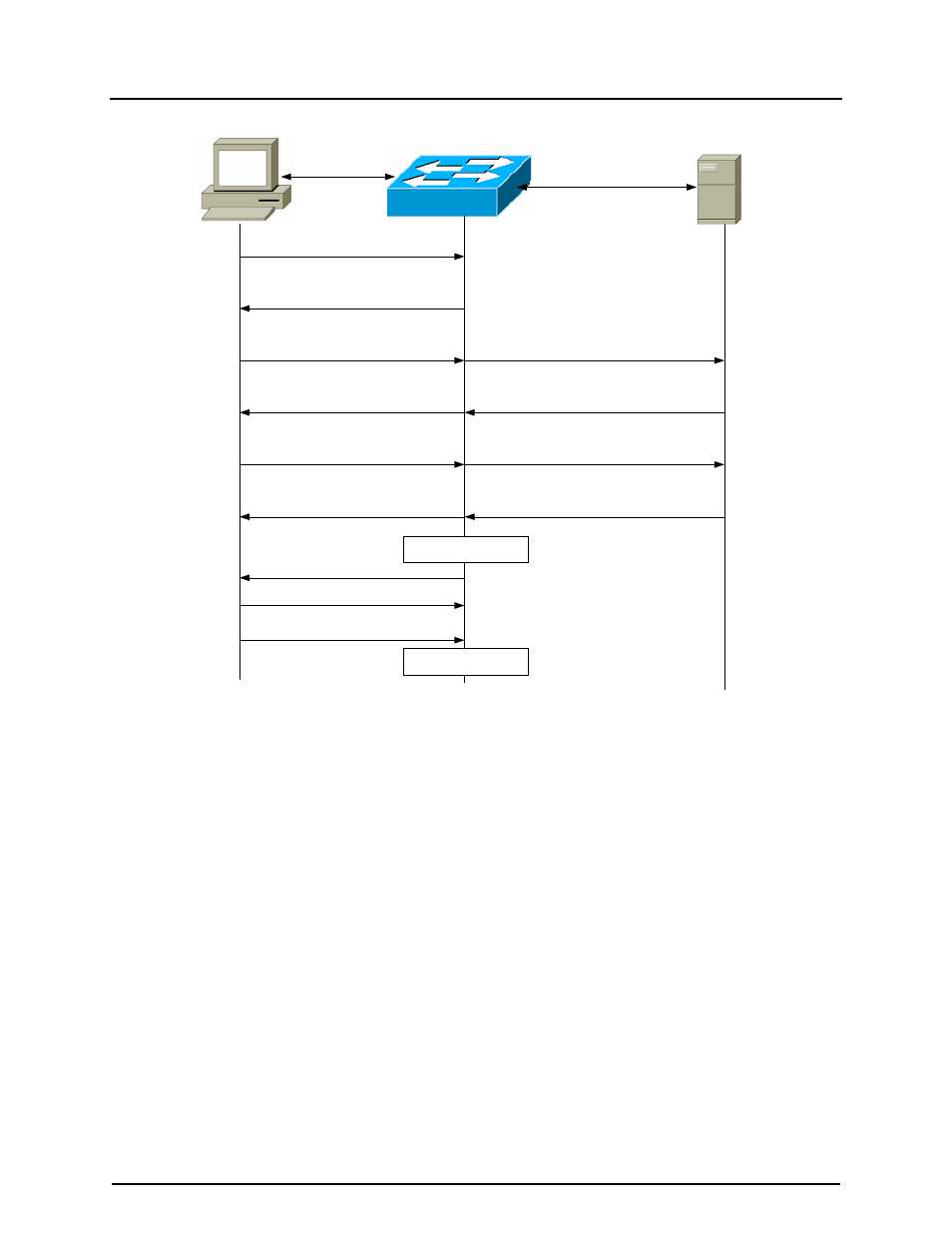
Figure 39-1: 802.1x Protocol
39.5 Ports in Authorized and Unauthorized state
Depending on the switch port state, the switch can grant a client access to the network.
The port starts in the unauthorized state. While in this state, the port that disallows all
ingress traffic (default unidirectional control) except for IEEE 802.1x packets. When a
client is successfully authenticated, the port changes to the authorized state, allowing all
traffic for the client to flow normally.
If a client that does not support IEEE 802.1x connects to an unauthorized IEEE 802.1x
port, the switch requests the client’s identity. In this situation, the client does not respond
to the request, the port remains in the unauthorized state, and the client is not granted
access to the network.
In contrast, when an IEEE 802.1x-enabled client connects to a port that is not running
the IEEE 802.1x standard, the client initiates the authentication process by sending the
EAPOL-start frame. When no response is received, the client sends the request for a
fixed number of times. Because no response is received, the client begins sending
frames as if the port is in the authorized state.
You control the port authorization state by using the dot1x port-control interface
configuration command and these keywords:
