11 ipsec debug, Figure 158 ike/ipsec debug example – ZyXEL Communications ZyXEL ZyWALL 2WG User Manual
Page 283
Chapter 14 IPSec VPN
ZyWALL 2WG User’s Guide
283
14.11 IPSec Debug
If you are having difficulty building an IPSec tunnel to a non-ZyXEL IPSec router, advanced
users may wish to examine the IPSec debug feature (in the commands).
"
If any of your VPN rules have an active network policy set to nailed-up, using
the IPSec debug feature may cause the ZyWALL to continuously display new
information. Type
ipsec debug level 0
and press [ENTER] to stop it.
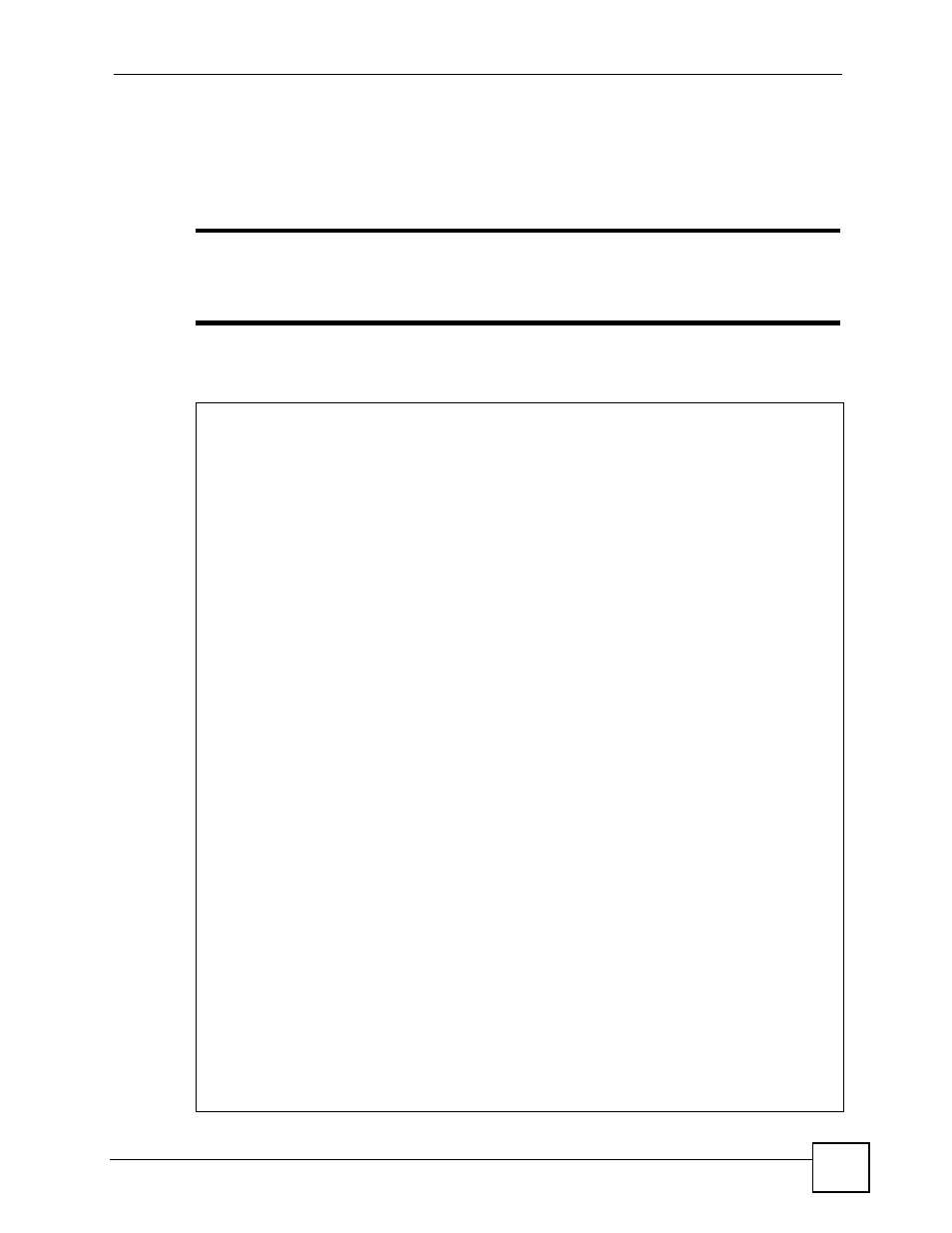
Figure 158 IKE/IPSec Debug Example
ras> ipsec debug
type level display
ras> ipsec debug type
<0:Disable | 1:Original on|off | 2:IKE on|off | 3: IPSec [SPI]|on|off |
4:XAUTH on|off | 5:CERT on|off | 6: All>
ras> ipsec debug level
<0:None | 1:User | 2:Low | 3:High>
ras> ipsec debug type 1 on
ras> ipsec debug type 2 on
ras> ipsec debug level 3
ras> ipsec dial 1
get_ipsec_sa_by_policyIndex():
Start dialing for tunnel
ikeStartNegotiate(): saIndex<0>
peerIp<5.1.2.3> protocol:
peer Ip <5.1.2.3> initiator(): type
initiator :
protocol: IPSEC_ESP, exchange mode: Main mode find_ipsec_sa():
find ipsec saNot found
Not found isadb_is_outstanding_req():
isakmp is outstanding req : SA not found
isadb_create_entry(): >> INITIATOR
isadb_get_entry_by_addr():
Get IKE entry by address: SA not found
SA not found ISAKMP SA created for peer
ISAKMP SA created for peer
ikePeer.s0
ISAKMP SA built, index = 0isadb_create_entry(): done
create IKE entry doneinitiator(): find myIpAddr = 0.0.0.0, use
<5.6.7.8> r
