4 additional ipsec vpn topics, 1 sa life time, Figure 148 vpn/nat example – ZyXEL Communications ZyXEL ZyWALL 2WG User Manual
Page 265
Chapter 14 IPSec VPN
ZyWALL 2WG User’s Guide
265
Aggressive mode does not provide as much security as main mode because the identity of the
ZyWALL and the identity of the remote IPSec router are not encrypted. It is usually used
when the address of the initiator is not known by the responder and both parties want to use
pre-shared keys for authentication (for example, telecommuters).
14.3.1.5 VPN, NAT, and NAT Traversal
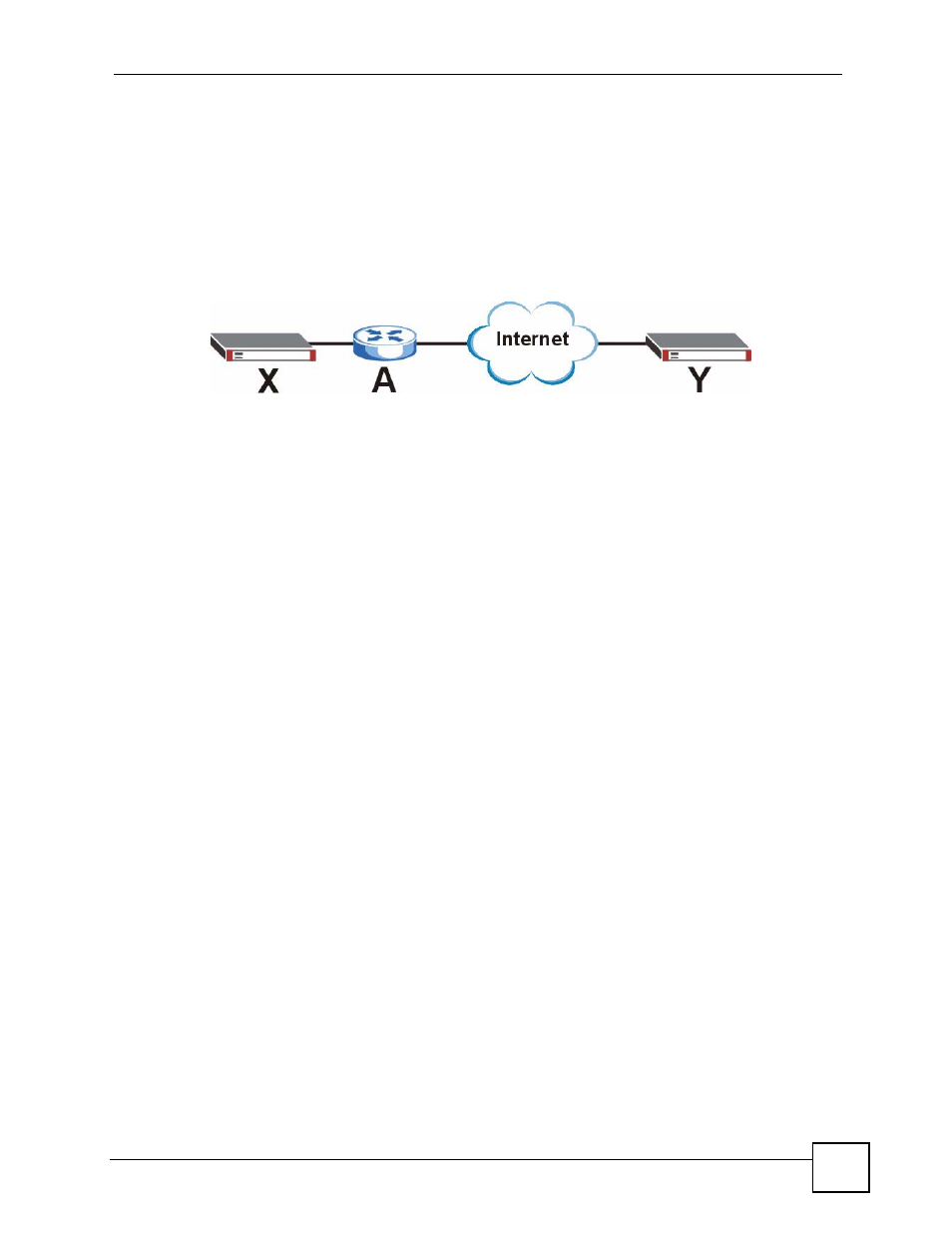
In the following example, there is another router (A) between router X and router Y.
Figure 148 VPN/NAT Example
If router A does NAT, it might change the IP addresses, port numbers, or both. If router X and
router Y try to establish a VPN tunnel, the authentication fails because it depends on this
information. The routers cannot establish a VPN tunnel.
Most routers like router A now have an IPSec pass-through feature. This feature helps router A
recognize VPN packets and route them appropriately. If router A has this feature, router X and
router Y can establish a VPN tunnel as long as the active protocol is ESP. (See
for more information about active protocols.)
If router A does not have an IPSec pass-through or if the active protocol is AH, you can solve
this problem by enabling NAT traversal. In NAT traversal, router X and router Y add an extra
header to the IKE SA and IPSec SA packets. If you configure router A to forward these
packets unchanged, router X and router Y can establish a VPN tunnel.
You have to do the following things to set up NAT traversal.
• Enable NAT traversal on the ZyWALL and remote IPSec router.
• Configure the NAT router to forward packets with the extra header unchanged. (See the
field description for detailed information about the extra header.)
The extra header may be UDP port 500 or UDP port 4500, depending on the standard(s) the
ZyWALL and remote IPSec router support.
14.4 Additional IPSec VPN Topics
This section discusses other IPSec VPN topics that apply to either IKE SAs or IPSec SAs or
both. Relationships between the topics are also highlighted.
14.4.1 SA Life Time
SAs have a lifetime that specifies how long the SA lasts until it times out. When an SA times
out, the ZyWALL automatically renegotiates the SA in the following situations:
• There is traffic when the SA life time expires
• The IPSec SA is configured on the ZyWALL as nailed up (see below)
