ZyXEL Communications ZyXEL ZyWALL 2WG User Manual
Page 184
Chapter 10 Wireless LAN
ZyWALL 2WG User’s Guide
184
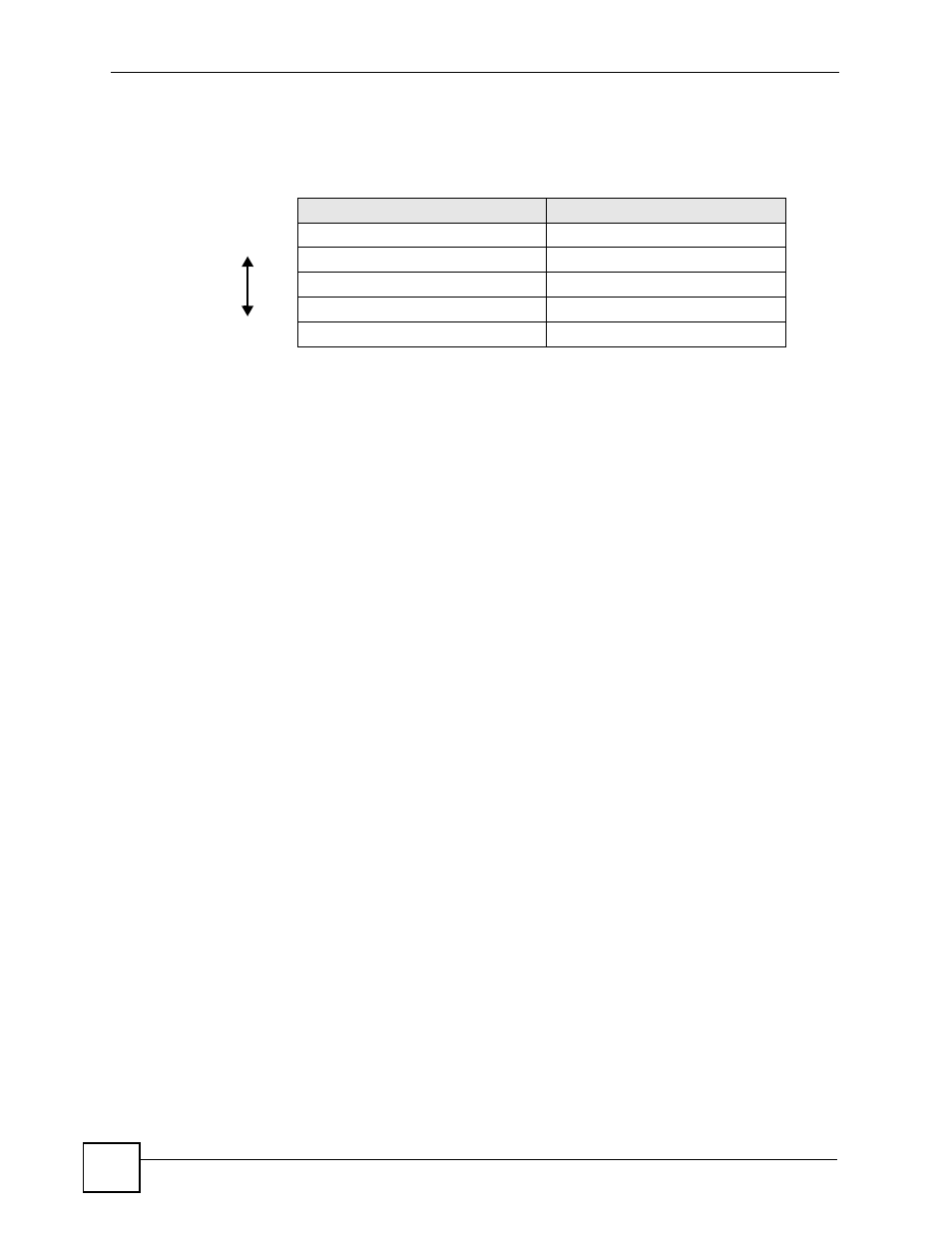
The types of encryption you can choose depend on the type of user authentication. (See
For example, if the wireless network has a RADIUS server, you can choose WPA or WPA2.
If users do not log in to the wireless network, you can choose no encryption, Static WEP,
WPA-PSK, or WPA2-PSK.
Usually, you should set up the strongest encryption that every wireless client in the wireless
network supports. For example, suppose the AP does not have a local user database, and you
do not have a RADIUS server. Therefore, there is no user authentication. Suppose the wireless
network has two wireless clients. Device A only supports WEP, and device B supports WEP
and WPA. Therefore, you should set up Static WEP in the wireless network.
Note: It is recommended that wireless clients use WPA-PSK, WPA, or stronger
encryption. IEEE 802.1x and WEP encryption are better than none at all, but it
is still possible for unauthorized devices to figure out the original information
pretty quickly.
It is not possible to use WPA-PSK, WPA or stronger encryption with a local
user database. In this case, it is better to set up stronger encryption with no
authentication than to set up weaker encryption with the local user database.
If some wireless clients support WPA and some support WPA2, you should set up WPA2-
PSK-Mix or WPA2-Mix (depending on the type of wireless network login) in the ZyWALL.
Many types of encryption use a key to protect the information in the wireless network. The
longer the key, the stronger the encryption. Every wireless client in the wireless network must
have the same key.
10.6.5 Additional Installation Requirements for Using 802.1x
• A computer with an IEEE 802.11a/b/g wireless LAN card.
• A computer equipped with a web browser (with JavaScript enabled) and/or Telnet.
• A wireless station must be running IEEE 802.1x-compliant software. Currently, this is
offered in Windows XP.
• An optional network RADIUS server for remote user authentication and accounting.
Table 55 Types of Encryption for Each Type of Authentication
No Authentication
RADIUS Server
Weakest
No Security
Static WEP
802.1x +Static WEP
WPA-PSK
WPA
Strongest
WPA2-PSK or WPA2-PSK-Mix
WPA2 or WPA2-Mix
