HP Virtual Connect Flex-10 10Gb Ethernet Module for c-Class BladeSystem User Manual
Page 67
Virtual Connect users and roles 67
o
Non-alphanumeric character
Click Apply to save your changes.
•
To set a session timeout period, enter a number between 10 and 1440 in the Session Timeout box. To
disable a session timeout period, enter 0. Click Apply to save your changes.
Any change in the timeout value affects all open sessions and is applied to new sessions.
•
To edit the delete confirmation preference, select or clear Auto Populate Name During Delete
Confirmation, and then click Apply. VCM displays confirmation dialog boxes when deleting objects
such as server profiles, networks, and so on. These dialog boxes require you to enter the name of the
item you want to delete and, in some cases, you must also enter the word "delete." If you enable the
Auto Populate Name During Delete option, the confirmation dialog boxes appear with the required
information automatically populated, enabling you to simply click OK to proceed with the deletion. This
is a domain-wide setting.
•
To enable local users, select the Enable Local Users checkbox. To disable local users, clear the Enable
Local Users checkbox. Click Apply to save your changes. You cannot disable local users if you are
logged in as a local user. Log in as an LDAP, TACACS, or RADIUS authenticated user with domain
privileges to disable local users.
•
To select the Primary Remote Authentication Method, select an option from the Primary Remote
Authentication Method list. Click Apply to save your changes. The Primary Remote Authentication
Method is the primary authentication mechanism that triggers the re-enablement of local user
authentication (if it was disabled) if the remote authentication servers are found to be unavailable
during login by a remote VC user. Valid values include NONE, LDAP, RADIUS, and TACACS. The
default value is NONE.
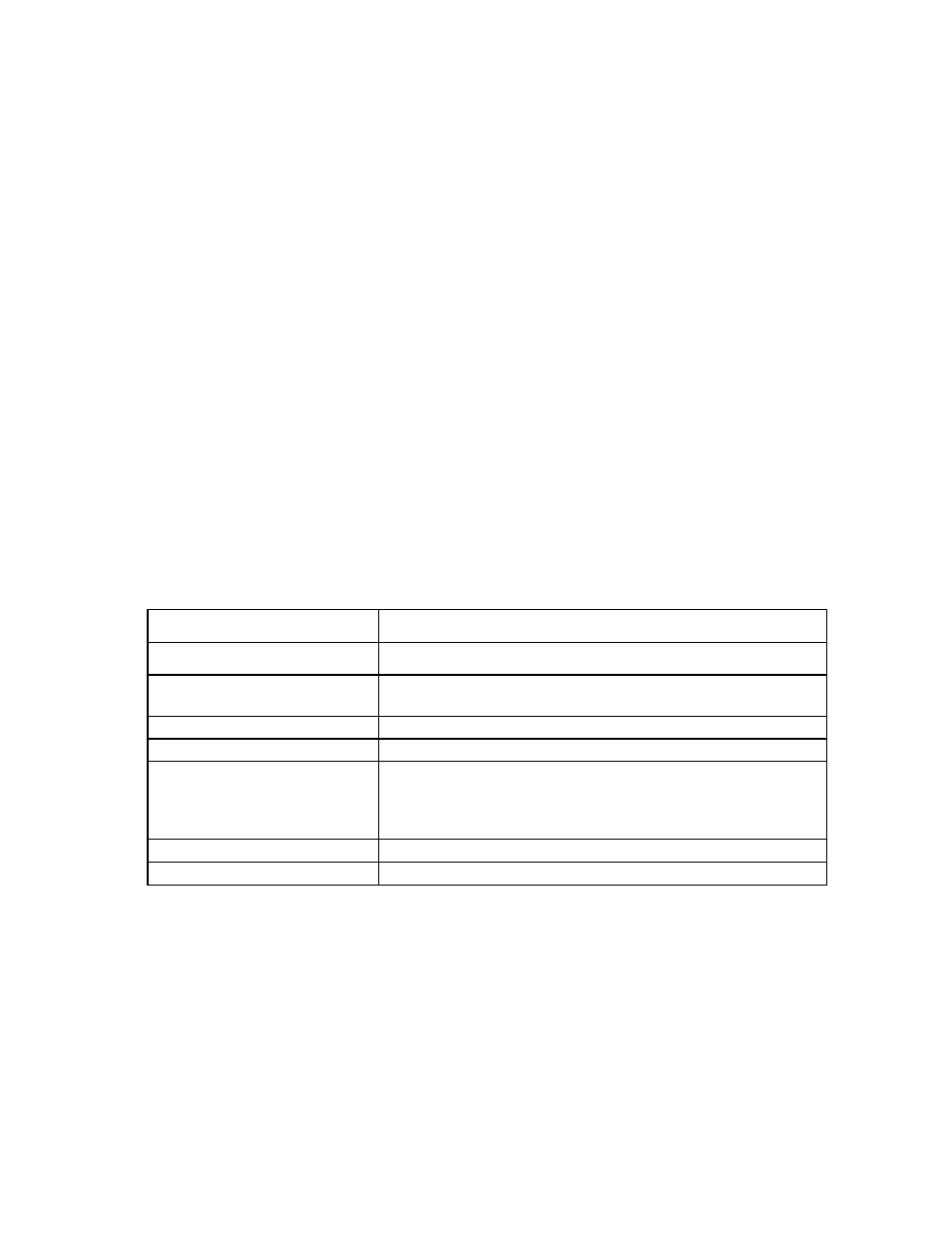
The following table describes the columns within the Local Users screen.
Column
Description
User Name
The user name must begin with a letter and is case sensitive.
Roles
Shows what role permissions the user has (Domain, Network, Storage,
and/or Server)
Role Operations
Specific role operations assigned to this user
Full Name
The user's full name. All users can modify their own full name.
Contact Info
Contact information for the user account. The contact information can be
the name of an individual, a telephone number, or other useful
information.
All users can modify their own contact information.
Account Status
Shows whether a user account is enabled or disabled.
Action
Perform edit and delete operations
- Virtual Connect FlexFabric 10Gb24-port Module for c-Class BladeSystem Virtual Connect Flex-10.10D Module for c-Class BladeSystem Virtual Connect 4Gb Fibre Channel Module for c-Class BladeSystem Virtual Connect 8Gb 24-port Fibre Channel Module for c-Class BladeSystem 4GB Virtual Connect Fibre Channel Module for c-Class BladeSystem Virtual Connect 8Gb 20-port Fibre Channel Module for c-Class BladeSystem
